Right To Privacy
Section 44(3) of the DPDP Act
From UPSC perspective, the following things are important :
Prelims level: Section 44(3)
Why in the News?
Opposition parties have raised concerns over the Digital Personal Data Protection (DPDP) Act, 2023, demanding the repeal of Section 44(3), claiming it could undermine the Right to Information (RTI) Act, 2005.
About DPDP Act and Section 44(3)
- Recognizing the right to privacy as fundamental in India, the Supreme Court in Justice K.S. Puttaswamy vs. Union of India (2017) led to the introduction of the DPDP Act in 2023.
- The Act regulates the processing of personal data, balancing individual privacy rights and lawful processing needs.
- Key Provisions: It mandates informed consent, establishes a Data Protection Board of India (DPBI), and outlines the responsibilities of data fiduciaries in ensuring data protection.
- Section 44(3) modifies Section 8(1)(j) of the RTI Act, which previously exempted personal information from disclosure unless public interest justified it.
- The amendment broadens this exemption, stating that all personal information should be exempt from disclosure, without requiring a public interest justification.
Concerns Related to Section 44(3)
- Reduced Transparency: Activists and critics argue that this section undermines the RTI Act, which has been a cornerstone of transparency and accountability in governance.
- Limited Access to Public Information: The broad exemption allows government officials to shield information like asset disclosures, which are critical for public accountability.
- Potential for Misuse: There are concerns that personal data protection could be used as an excuse to block vital information about government activities, weakening the public’s right to know.
- Conflict Between Public Interest and Privacy: Critics argue that privacy protection should not override the principle of transparency.
Back2Basics: Right to Information (RTI) Act, 2005
|
| [UPSC 2018] Right to Privacy is protected as an intrinsic part of Right to Life and Personal Liberty. Which of the following in the Constitution of India correctly and appropriately imply the above statement?
(a) Article 14 and the provisions under the 42ndAmendment to the Constitution. (b) Article 17 and the Directive Principles of State Policy in Part IV. (c) Article 21 and the freedoms guaranteed in Part III. (d) Article 24 and the provisions under the 44thAmendment to the Constitution. |
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
The challenge of policing digital giants
From UPSC perspective, the following things are important :
Mains level: Digital Market challenges;
Why in the News?
On November 18, 2024, the Competition Commission of India (CCI) imposed a fine of ₹213.14 crore on Meta Platforms, Inc., for abusing its dominant position through WhatsApp’s 2021 Privacy Policy. This landmark decision underscores the growing intersection of competition law and data privacy, marking a significant step in regulating digital markets in India.
What were the key findings of the Competition Commission of India (CCI)?
|
Why did the National Company Law Appellate Tribunal (NCLAT) grant a stay on CCI’s five-year ban and penalty imposed on Meta?
- Prima Facie Case for Meta: NCLAT found grounds to review CCI’s decision, indicating that Meta’s appeal had merit and required further examination. Example: Meta argued that its privacy policy update did not force users but offered them a choice, which needed deeper legal scrutiny.
- Irreparable Harm to Meta’s Business: The five-year ban on sharing WhatsApp user data with Facebook and Instagram could cause significant financial and operational disruption to Meta’s business. Example: Meta claimed that restricting data integration would affect its targeted advertising model, reducing its revenue from India.
- Dominance and anti-competitive effects: NCLAT noted that CCI’s conclusions on abuse of dominance and anti-competitive effects required further legal and economic analysis before enforcement. Example: The tribunal wanted to assess whether the policy update genuinely harmed consumers or merely provided better services through personalized ads.
- Balance of Convenience: The tribunal ruled that temporarily halting the penalty and data-sharing ban would not cause immediate harm to consumers but would protect Meta from disproportionate damages while the case was under review. Example: If Meta had to immediately comply but later won the appeal, reversing the business impact would be difficult.
- Conditional Relief with Partial Penalty Payment: NCLAT granted the stay but directed Meta to deposit 50% of the ₹213.14 crore penalty, ensuring some accountability while legal proceedings continued. Example: This allowed Meta to continue operations without full compliance but ensured it remained engaged in the legal process.
How does data play a role in creating and sustaining dominance in digital markets?
- Data-Driven Network Effects: More users generate more data, which improves algorithms and services, attracting even more users, creating a self-reinforcing loop. Example: Google’s search engine improves as more users search, making its results better than competitors, reinforcing its market dominance.
- Competitive Barrier Through Data Aggregation: Large tech firms collect massive user data across multiple services, making it hard for new entrants to compete due to a lack of comparable datasets. Example: Meta collects data from Facebook, Instagram, and WhatsApp, allowing it to offer highly personalized ads, making it difficult for smaller ad platforms to compete.
- Monetization & Market Lock-In: Companies use vast data pools to refine targeted advertising, personalize user experiences, and create dependencies, discouraging users from switching. Example: Amazon leverages consumer purchase data to optimize product recommendations, making it harder for new e-commerce platforms to attract customers.
Which global regulatory actions have been taken against Meta and Google for their anti-competitive practices?
|
What should be amendments in India’s Competition Act, 2002 to address data-centric monopolies? (Way forward)
- Recognizing “Data Monopolization” as a Form of Market Power: The Act should explicitly define data dominance as a key factor in determining market power and abuse of dominance.
- Example: The EU’s Digital Markets Act (DMA) considers large data control a sign of dominance. India could adopt similar provisions to regulate companies like Meta and Google that leverage massive user data to eliminate competition.
- Mandatory Interoperability and Data-Sharing Regulations: The Act should mandate interoperability and restrict exclusive data-sharing agreements that create entry barriers for competitors.
- Example: In Germany, Meta was restricted from combining user data across platforms without explicit consent. Similarly, India could prevent dominant firms from self-preferencing their services and enforce data portability rules to promote fair competition.
Mains PYQ:
Q How have digital initiatives in India contributed to the functioning of the educational system in the country? Elaborate your answer.” (UPSC 2020)
Reason: This question underscores the significant impact of digital platforms on key sectors. The influence of digital giants extends to education (e.g., online learning platforms, content distribution), highlighting their pervasive role and the need for understanding and potentially regulating their impact.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Plight of Prisoners with Disabilities needs attention SC
From UPSC perspective, the following things are important :
Prelims level: Read the attached story
Why in the News?
The Supreme Court has acknowledged a serious issue regarding the lack of disabled-friendly infrastructure in prisons, following a petition citing the trauma and inhumane conditions faced by Professor G. Saibaba and Stan Swamy.
A bench comprising Justices Vikram Nath and Sandeep Mehta noted that even the Persons with Disabilities Act (2016) lacks a legal framework to safeguard the rights of disabled prisoners.
Challenges Faced by Disabled Prisoners:
- Inaccessible Infrastructure: Most prisons lack ramps, handrails, wheelchair-accessible cells, and essential assistive devices.
- Denial of Medical Care: Many disabled prisoners do not receive necessary medical treatment, physiotherapy, or even basic aids like hearing devices or walking supports.
- Psychological Distress: Isolation, lack of facilities, and mistreatment lead to anxiety, depression, and deteriorating mental health among disabled prisoners.
- Data Deficiency: No official records track the number or condition of disabled prisoners, making policy implementation difficult.
Rights of Persons with Disabilities (in Prisons)
- Article 14 guarantees equality before the law, ensuring that prisoners are not discriminated against based on disability.
- Article 21 upholds the right to life and dignity, including humane treatment for prisoners.
- Rights of Persons with Disabilities Act, 2016 mandates accessible public spaces, medical care, and assistive devices for persons with disabilities, but implementation in prisons remains inadequate.
- Model Prison Manual, 2016 recommends disability-friendly infrastructure such as ramps and medical care provisions, yet many states have not adopted these reforms.
- Supreme Court Judgments:
-
- In Upendra Baxi vs. State of U.P. (1983), the Supreme Court reaffirmed that prisoners are entitled to humane treatment.
- In Rama Murthy vs. State of Karnataka (1996), the Court highlighted the urgent need for prison reform, including facilities for disabled inmates.
- The Stan Swamy Case (2021) brought attention to the denial of essential assistive tools such as straws and sippers for Parkinson’s patients.
Past Committees on Prison Reform:
- Mulla Committee (1983):
- Recommended improved prison infrastructure, special provisions for disabled inmates, and measures to reduce overcrowding.
- Suggested protection against abuse and better training for prison staff.
- Krishna Iyer Committee (1987): Focused on the welfare of women prisoners, recommending separate facilities, healthcare, and special provisions for pregnant inmates.
- Justice A.N. Mulla Committee (1993): Emphasized the need for humane treatment and rehabilitation, along with stricter measures against custodial torture.
- Justice Krishna Iyer Report (2000): Called for legal aid for undertrial prisoners and mandatory inspections to monitor prison conditions.
- Model Prison Manual (2016):
- Provided guidelines for standardized prison reforms, including healthcare, accessibility, and rehabilitation programs.
- Despite being issued by the Ministry of Home Affairs, many states have failed to adopt its recommendations.
PYQ:[2016] Does the Rights of Persons with Disabilities Act, 2016 ensure effective mechanism for empowerment and inclusion of the intended beneficiaries in the society? Discuss. |
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Why are PwDs worried about DPDP rules?
From UPSC perspective, the following things are important :
Mains level: Issues related to PwDs;
Why in the News?
The Ministry of Electronics and Information Technology (MeitY) plans to complete public consultations on the draft Rules for the Digital Personal Data Protection Act, 2023, by March 5. Meanwhile, disability rights activists are urging changes to a key provision of the Act.
Why are persons with disabilities concerned about a certain provision in the draft Rules of the Digital Personal Data Protection Act, 2023?
- Infringement on Autonomy and Decision-Making Capacity: Section 9(1) clubs adult PwDs with children, requiring consent from a legal guardian for processing personal data. This undermines their ability to make independent decisions.
- Example: An adult with a physical disability wanting to access online banking may be restricted if the platform requires guardian consent.
- Lack of Clarity and Ambiguity in Implementation: The Act does not clearly outline how consent should be obtained across various disabilities and degrees of severity, leading to confusion.
- Example: A person with limited cognitive impairment under “limited guardianship” may still be treated as entirely incapable.
- Conflict with UNCRPD Principles: The provision conflicts with the United Nations Convention on the Rights of Persons with Disabilities (UNCRPD), which emphasizes supported decision-making over substituted decision-making.
- Example: Under the RPWD Act, a PwD may receive assistance only when necessary, but the DPDP Act assumes total incapacity if a legal guardian exists, contradicting the UNCRPD framework.
- Concerns About Privacy and Data Security: Platforms may need to collect sensitive information (like whether a user has a disability) to verify guardianship status, raising privacy concerns.
- Exclusion from Digital Services: The additional procedural burden on PwDs and data fiduciaries could lead to exclusion from essential digital platforms.
How do guardianships for Persons with Disabilities (PwDs) function?
How are legal guardians defined under the draft rules?
Who are data fiduciaries and data principals?
|
Where does the conflict lie?
- Presumption of Incapacity vs. Legal Recognition of Capacity: The DPDP Act assumes adult PwDs lack the capacity to give consent if a guardian is involved, whereas the RPWD Act recognizes their legal capacity and promotes their right to make decisions.
- Example: A person with mild intellectual disability working in a corporate setting may need guardian approval for routine data-related tasks, despite their ability to understand and consent.
- Data Privacy vs. Intrusive Verification: The DPDP Act may require platforms to collect and verify sensitive disability information, potentially breaching privacy rights, while the UNCRPD emphasizes the right to privacy without discrimination.
- Example: An online service requiring disability verification for consent could store unnecessary sensitive data, increasing risks of unauthorized access or misuse.
Way forward:
- Adopt a Supported Decision-Making Model: Align the DPDP Act with the RPWD Act and UNCRPD by recognizing limited guardianship and allowing PwDs to provide independent consent with appropriate support when needed.
- Ensure Privacy and Minimize Data Collection: Limit the collection of sensitive disability information to essential cases, ensuring purpose limitation and data minimization while protecting PwDs’ privacy rights.
Mains PYQ:
Q Impact of digital technology as a reliable source of input for rational decision-making is a debatable issue. Critically evaluate with a suitable example. (UPSC IAS/2021)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
[25th February 2025] The Hindu Op-ed: Surveillance capitalism: the power to control personal data
PYQ Relevance:Q) Data security has assumed significant importance in the digitized world due to rising cyber-crimes. The Justice B. N. Srikrishna Committee Report addresses issues related to data security. What, in your view, are the strengths and weaknesses of the Report relating to protection of personal data in cyber space? (UPSC CSE 2018) |
Mentor’s Comment: UPSC mains have always focused on “ Data security” (2018), and the Impact of digital technology (2021).
Surveillance capitalism is an economic system where tech companies collect, analyze, and sell personal data to predict and influence behaviour. This system, described by Shoshana Zuboff in The Age of Surveillance Capitalism (2018), treats human experiences as a resource for profit, similar to how colonialism and industrial capitalism exploited natural and human resources.
Today’s editorial highlights current issues related to surveillance capitalism and its impact. This topic is relevant for GS Paper 2 and 3 in the UPSC Mains.
_
Let’s learn!
Why in the News?
Recently, surveillance capitalism has depended on turning personal data into a product. It affects people’s privacy and freedom while being closely linked to government surveillance.
What is Surveillance Capitalism?
|
How does surveillance capitalism rely on the commodification of personal data?
- Collection of Personal Data as Raw Material: Google Search tracks every query a user makes, including location and device information. This data is processed to understand user preferences and behaviour patterns.
- Behavioural Prediction for Targeted Advertising: Companies monetize behavioural data by selling it to advertisers who target users with precision, maximizing ad effectiveness.
- Meta (Facebook) monitors user activity across its platforms to deliver highly personalized ads. Users discussing fitness products may soon see ads for gym memberships.
- Continuous Data Harvesting Across Devices: Data is continuously extracted from smart devices, even during routine interactions, deepening the pool of user insights.
- Amazon’s Alexa collects voice commands and ambient sounds to refine product recommendations and improve its machine-learning models.
- Algorithmic Manipulation to Influence Behaviour: Algorithms shape user behaviour by curating content that fosters prolonged engagement, increasing ad revenue.
- YouTube’s recommendation algorithm analyses watch history to suggest videos that keep users engaged, often promoting content that aligns with their interests or biases.
What are the strong connections between data commodification and state surveillance?
- Mass Data Collection Programs: Governments collaborate with private tech companies to access vast amounts of personal data for surveillance purposes. Example: The PRISM program by the U.S. National Security Agency (NSA) collected user data from major tech companies like Google, Facebook, and Microsoft to monitor global communications.
- Legal Mandates for Data Sharing: Many countries enforce laws requiring digital platforms to share user data with state agencies for national security and law enforcement. Example: India’s Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021 require platforms to trace the origin of messages, facilitating state surveillance.
- Surveillance Technologies Integration: States use advanced technologies like facial recognition and AI-driven monitoring to track citizens’ movements and online activities. Example: China’s Social Credit System uses surveillance cameras and digital monitoring to track citizens’ behavior, affecting access to services based on their social scores.
What are the negative impacts of commodifying personal data?
- Privacy Erosion: When personal data is commodified, individuals lose control over their private information, leading to widespread privacy violations. Example: Social media platforms like Facebook have been criticized for selling user data to third parties, such as Cambridge Analytica which used it for targeted political advertising without users’ explicit consent.
- Exploitation and Manipulation: Personal data is often used to influence behaviour through targeted advertising or algorithmic content curation, exploiting vulnerabilities. Example: Companies like Google and Amazon use personal data to create highly targeted ads.
- Increased Risk of Data Breaches: The collection and trade of personal data raise the likelihood of data breaches, leading to identity theft, financial loss, and other harms. Example: The Equifax data breach in 2017 exposed the personal information of 147 million people.
- Inequality and Discrimination: Commodified data can reinforce social and economic inequalities by enabling discriminatory practices, such as price discrimination or exclusion from services. Example: Insurance companies may use personal data to charge higher premiums to individuals based on their health or lifestyle, disproportionately affecting vulnerable groups.
- Loss of Autonomy and Trust: The exploitation of personal data weakens public trust in institutions and reduces individuals’ sense of control over their own information. Example: The revelation that apps like TikTok collect and share user data with governments or third parties.
What steps has the Indian government taken?
What steps have been taken at the global level?
|
Way forward:
- Stronger Regulatory Frameworks: Implement comprehensive and adaptive data protection laws with clear accountability for data handlers, regular audits, and stringent penalties to safeguard user privacy and prevent misuse.
- User Empowerment and Transparency: Promote data literacy programs and ensure platforms provide clear, accessible consent mechanisms, allowing users greater control over their personal information and how it is shared.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Should voter IDs be linked with Aadhaar?
From UPSC perspective, the following things are important :
Mains level: Electoral Rolls;
Why in the News?
Two political parties have accused each other of tampering the voter lists before the Delhi Assembly elections. This has brought back the discussion about linking voter IDs (EPIC) with Aadhaar numbers.
Why was the National Electoral Rolls Purification and Authentication Program?
The National Electoral Rolls Purification and Authentication Program (NERPAP) was launched by the Election Commission of India on March 3, 2015, with the primary goal of creating an error-free and authenticated electoral roll.
- Linking EPIC with Aadhaar: The program sought to link the Elector’s Photo Identity Card (EPIC) data with the Aadhaar database to authenticate voter identities and eliminate duplicate entries in the electoral rolls.
- Error Correction: NERPAP aimed to facilitate the correction of errors in voter data and improve the overall quality of images on electoral documents.
- Voluntary Disclosure of Multiple Entries: Voters were encouraged to voluntarily disclose any multiple registrations, allowing for timely corrections and deletions of unnecessary entries from the electoral rolls.
- Enhanced Communication: The initiative also aimed to collect mobile numbers and email addresses from voters, enabling the Election Commission to provide important updates regarding elections, such as poll dates and revision schedules.
- Public Participation: To ensure maximum engagement, special camps and facilitation centers were organized nationwide to assist voters in linking their Aadhaar with EPIC and addressing any concerns regarding their registrations.
What did the Supreme Court mandate in the Puttaswamy case in 2018?
- In the Puttaswamy case, the Supreme Court recognized the right to privacy as a fundamental right under the Constitution. It ruled that while Aadhaar could be used for various purposes, including voter registration, individuals cannot be denied their right to vote for failing to provide their Aadhaar number.
- This ruling emphasized that any legal framework must respect individual privacy rights and ensure that no citizen is disenfranchised due to administrative requirements.
What are the pros and cons?
Pros:
- Elimination of Duplicate Entries: Linking Aadhaar with EPIC can help remove multiple registrations for individuals who may have registered in different locations due to migration.
- Real-time Authentication: The unique identity provided by Aadhaar enables online verification, enhancing the accuracy of voter rolls.
- Updated Voter Database: The initiative aims to maintain an updated and accurate record of voters, which is crucial for free and fair elections.
Cons:
- Database Errors: Errors within the Aadhaar database could lead to wrongful rejection or deletion of legitimate voter entries.
- Proof of Citizenship Concerns: Aadhaar serves as proof of residence but not citizenship, potentially failing to address non-citizen registrations on electoral rolls.
- Privacy Risks: While linkage may not directly violate privacy rights, there are concerns about misuse as electoral rolls are accessible to political parties.
What can be the way forward?
- Transparent and Voluntary Process: Modify electoral forms to clearly indicate that providing Aadhaar is voluntary, ensuring no voter is denied registration for not furnishing their Aadhaar number.
- Strengthen Data Accuracy and Privacy Safeguards: Establish mechanisms to verify Aadhaar data accuracy and implement robust data protection measures to prevent misuse of linked electoral rolls.
Mains PYQ:
Q Examine the scope of Fundamental Rights in the light of the latest judgement of the Supreme Court on Right to Privacy.(UPSC IAS/2017)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
In today’s India, can the Constitution protect individual dignity?
From UPSC perspective, the following things are important :
Mains level: Constitution of India; Individual liberty and dignity;
Why in the News?
The SC has emphasized the importance of individual dignity within the context of Article 21 in several landmark cases.
- Discussions around individual dignity have again gained traction, especially when former SC Justice Kurian Joseph emphasized that the Constitution prioritizes individual dignity, making it a vital topic for contemporary legal discourse.
How effectively does the Constitution safeguard individual dignity?
The Constitution of India is designed to protect individual dignity through a framework that entitles citizens to fundamental rights.
- Entrenchment of Individual Rights: The Constitution explicitly guarantees individual rights, aiming to protect the freedom and dignity of all citizens.
- Fundamental Rights under Part III of the Constitution, such as the Right to Equality (Article 14), Right to Freedom (Articles 19-22), and Right to Life and Personal Liberty (Article 21), explicitly safeguard individual dignity.
- Checks and Balances: The Constitution establishes institutional checks and balances to prevent the abuse of power.
- In Maneka Gandhi v. Union of India (1978), the Supreme Court broadened the scope of Article 21, holding that any law depriving personal liberty must meet the standards of fairness, justice, and reasonableness.
- Political Equality: By affirming political equality among citizens, the Constitution enables individuals to participate actively in the democratic process.
- Article 326 guarantees universal adult suffrage, enabling all citizens to participate equally in democratic processes, affirming their political dignity and sense of inclusion.
What role do societal attitudes and systemic issues play in protecting dignity?
Societal attitudes and systemic issues significantly influence the protection of individual dignity under the Constitution:
- Community Identity vs. Individual Rights: The emphasis on community identity whether based on caste, religion, or nation can undermine individual dignity. When societal attitudes prioritize group identities over individual rights, it can lead to discrimination and marginalization.
- Trust and Cooperation: A lack of trust among citizens can hinder collective efforts to uphold constitutional values. When individuals measure each other against rigid identities, it subverts the freedom that the Constitution aims to protect.
- Oligarchic Power: Concentration of wealth and power can distort democratic processes, leading to a situation where certain groups’ interests overshadow individual rights. This systemic issue can erode the effectiveness of constitutional protections for dignity.
Can legal frameworks adapt to evolving understandings of dignity?
The legal framework established by the Constitution has the potential to adapt to evolving understandings of dignity:
- Basic Structure Doctrine: The Basic Structure Doctrine, established in Kesavananda Bharati v. State of Kerala (1973), ensures that core principles like dignity remain inviolable while allowing amendments to address evolving needs.
- For example, The 103rd Constitutional Amendment (2019) introduced a 10% reservation for Economically Weaker Sections (EWS) in education and public employment.
- Ongoing Democratic Negotiation: The Constitution leaves questions regarding economic structure open for ongoing negotiation, allowing for discussions around justice and inclusion that are vital for protecting dignity in a changing society.
- For example, The introduction of the Transgender Persons (Protection of Rights) Act, 2019 marked a significant step toward affirming the dignity and rights of transgender individuals.
- Judicial Interpretation: Courts play a critical role in interpreting constitutional provisions related to dignity.
- For example, Navtej Singh Johar v. Union of India (2018) decriminalized consensual same-sex relationships by reading down Section 377 of the Indian Penal Code.
Way forward:
- Promoting Constitutional Values: Enhance public awareness and foster societal attitudes that prioritize individual dignity, equality, and mutual respect over group identities.
- Strengthening Institutional Adaptability: Empower judicial and legislative mechanisms to address systemic inequities, interpret evolving notions of dignity, and implement inclusive policies.
Mains PYQ:
Q Examine the scope of Fundamental Rights in the light of the latest judgement of the Supreme Court on Right to Privacy. (UPSC IAS/2017)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
What is a Polygraph Test?
From UPSC perspective, the following things are important :
Prelims level: Polygraph Test, Judments mentioned
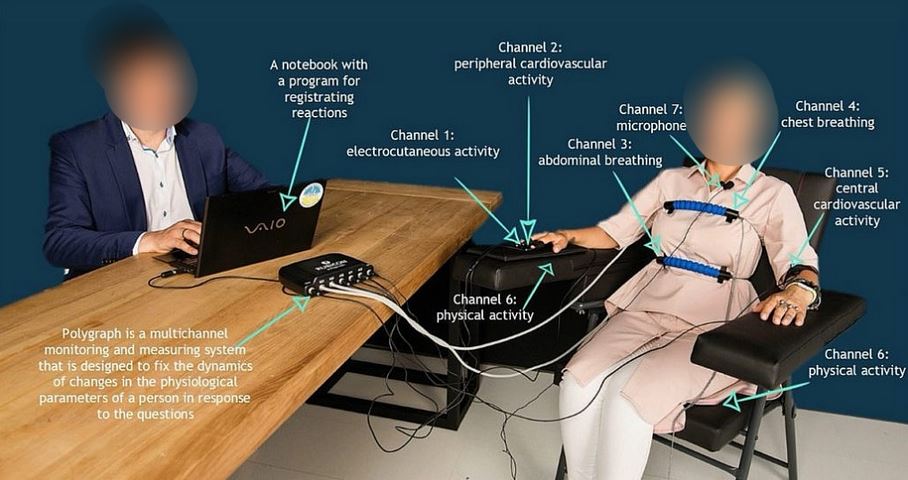
Why in the News?
The Central Bureau of Investigation (CBI) concluded polygraph tests on the accused in the Kolkata Rape and Murder Case.
About Polygraph Tests in India
| Details | |
| Definition | A procedure measures physiological responses like blood pressure, pulse, respiration, and skin conductivity while a subject answers questions to detect deception. |
| Physiological Indicators | • Heart Rate and Blood Pressure: Monitored for changes. • Respiratory Rate: Tracks breathing patterns. • Galvanic Skin Response (GSR): Measures skin’s electrical conductance, which varies with moisture levels. |
| Procedure | • Sensor Connection: Attached to the chest, fingertips, and arm. • Baseline Questions: Establish physiological response baselines. • Control and Relevant Questions: Analyzed to identify deceptive responses by comparing physiological changes. |
| Constitutional Provisions | • Article 20(3): Protects against self-incrimination; necessitates consent for polygraph tests. • Article 21: Concerns about potential violations of the right to life and privacy due to mental torture aspects of polygraph tests. |
| Legal and Judicial Rulings | • Selvi vs. State of Karnataka (2010): Tests must be voluntary with informed consent. • D.K. Basu vs. State of West Bengal (1997): Involuntary tests could violate the Right to Life and Privacy. |
| Admissibility in Court | According to the Indian Evidence Act, 1871, results from polygraph tests are not admissible as evidence in court. |
| Guidelines | National Human Rights Commission Guidelines (1999): Establish consent and procedural requirements for administering polygraph tests to align with human rights standards. |
PYQ:[2018] Right to Privacy is protected as an intrinsic part of Right to Life and Personal Liberty. Which of the following in the Constitution of India correctly and appropriately imply the above statement? (a) Article 14 and the provisions under the 42nd Amendment to the Constitution. (b) Article 17 and the Directive Principles of State Policy in Part IV. (c) Article 21 and the freedoms guaranteed in Part III. (d) Article 24 and the provisions under the 44th Amendment to the Constitution. |
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
SC to examine acquitted man’s ‘Right to be Forgotten’: What is this right, and how have courts ruled earlier?
From UPSC perspective, the following things are important :
Prelims level: Right to be Forgotten
Mains level: Key judgments related to the Right to be forgotten
Why in the News?
Last week, the Supreme Court agreed to hear a case that could define the scope of the “Right to be Forgotten” referred to in European privacy law as the “Right to Erasure” in India.
What is the ‘Right to be Forgotten’?
- The right to be forgotten allows individuals to remove or de-index their personal information from the internet if it infringes on their right to privacy. It is based on the principle that personal data should be removed when it is outdated, irrelevant, or no longer necessary.
- Affirmed by the Court of Justice of the European Union (CJEU) in the “Google Spain case” (2014), which ruled that search engines must remove data if it is inadequate, irrelevant, or excessive in light of the time elapsed.
- Under the EU’s General Data Protection Regulation (GDPR), Article 17 describes the right to erasure, reflecting the concept of informational self-determination.
How is this ‘Right’ interpreted in India?
- Absence of Statutory Framework: India lacks specific legislation explicitly addressing the right to be forgotten.
- Judicial Interpretation: The 2017 Supreme Court ruling in Justice K.S. Puttaswamy v. Union of India recognized the right to privacy as a fundamental right. Justice S.K. Kaul’s concurring opinion suggested that the right to be forgotten involves removing personal data that is no longer necessary or relevant.
- Judicial Guidelines: Justice Kaul outlined valid justifications for overriding this right, including freedom of expression, legal compliance, public interest, and research purposes.
How have Courts ruled on the Issue?
- Rajagopal vs. State of Tamil Nadu (1994): The Supreme Court recognized a “right to be let alone” but differentiated it from public records, including court decisions. Once something becomes public, privacy rights are diminished.
- Dharamraj Bhanushankar Dave vs. State of Gujarat (2017): Gujarat HC refused to remove details of an acquittal, asserting that court orders should remain public.
- The Registrar General (2017): Karnataka HC protected the name of a petitioner in a sensitive annulment case, aligning with trends in Western jurisdictions.
- Delhi HC (2021): Extended the right to be forgotten to criminal cases, allowing details of an acquittal to be removed from search results to protect the petitioner’s career prospects.
- Orissa HC (2020): Noted the need for a broader debate on the right to be forgotten, particularly concerning “revenge porn” and online content.
Way forward:
- Legislative Framework Development: India should consider drafting comprehensive legislation that explicitly addresses the right to be forgotten, aligning with international standards while balancing privacy, freedom of expression, and public interest.
- Judicial and Policy Clarity: The Supreme Court’s upcoming ruling should aim to establish a clear legal precedent on the right to be forgotten, ensuring consistency across lower courts and aligning with global practices.
Mains PYQ:
Q Examine the scope of Fundamental Rights in the light of the latest judgement of the Supreme Court on the Right to Privacy. (2017)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Living wills implementation lags in India
From UPSC perspective, the following things are important :
Prelims level: Article 21; Right to die with dignity; Right to will;
Mains level: Supreme Court;
Why in the news?
In early March this year, 30 people in Thrissur in Kerala executed living wills.
Context:
- The Supreme Court’s 2018 order on Passive Euthanasia, wherein it recognized the ‘Right to die with dignity’ as a fundamental right and an aspect of Article 21 (right to life) of the Constitution.
- However, the people wanting to get a “living will” registered were facing problems due to cumbersome guidelines, prompting a reconsideration by the apex court.
- A Constitution Bench, led by Chief Justice of India Dipak Misra, in three concurring opinions, upheld that the fundamental right to life and dignity includes the ‘Right to Refuse Treatment and Die with dignity’.
What is a Living Will?A Living Will is a healthcare directive, in which people can state their wishes for their end-of-life care, in case they are not in a position to make that decision. The Court’s procedure:
|
Challenges in Implementation :
- Decision-Making Process: Even if a living will is created, its implementation is not automatic. Decisions on withholding or withdrawing treatment require certification by primary and secondary medical boards, posing logistical challenges, especially in hospitals without designated boards.
- Ambiguities and Discomfort: Ambiguities in guidelines, discomfort with end-of-life care topics, and unclear legal definitions contribute to the hesitancy among officials to implement the Court’s directives without clear instructions from higher authorities.
- Legal Ambiguity: Indian law lacks a clear definition of ‘next of kin’, leading to potential disputes among family members about medical decisions for terminally ill patients.
- Barriers to End-of-Life Decisions: A survey of intensive care doctors reveals a general belief that end-of-life decisions are fraught with legal implications, serving as a significant barrier to making such decisions in the ICU.
- Regional Disparities in India:
- Haryana: While some states like Haryana have issued directions to follow the judgment, they have not provided essential guidance or protocols for implementation.
- Odisha: In contrast, Odisha has taken a more thorough approach by forming a committee of experts to develop detailed draft orders for implementing the judgment, setting a potential example for other states.
Conclusion: The central government could help bridge the gap in expertise by developing and publishing model orders and protocols to provide states with confidence and guidance in effectively implementing the judgment.
Mains question for practice
Q Discuss the challenges surrounding the implementation of living wills in India, as established by the Supreme Court’s landmark judgment in 2018.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Internet Shutdowns in India: Upholding Constitutional Rights
From UPSC perspective, the following things are important :
Prelims level: Right to Internet
Mains level: Not Much
Introduction
- The Internet serves as a vital source of information, entertainment, healthcare, education, and livelihood.
- However, the rampant instances of Internet suspension in India, often without public disclosure, raise concerns about constitutional rights and economic losses.
Constitutional Provisions for Right to Internet
| Landmark Case | Constitutional Provision | Explanation |
| Anuradha Bhasin vs. Union of India and Ors. (2020) | Right to Freedom of Speech and Expression under Article 19(1)(a) | Grants the right to freedom of speech and expression, which encompasses access to information and the Internet. |
| Faheema Shirin RK vs. State of Kerala and others (2019) | Right to Education under Article 21A | Guarantees the right to education for children aged 6 to 14;
Internet access is crucial for modern education. |
| K.S. Puttaswamy (Privacy) vs. Union of India (2017) | Right to Privacy under Article 21 | Protects the fundamental right to privacy, and Internet access is often used for secure communication. |
| Anuradha Bhasin vs. Union of India and Ors. | Freedom to Practice Any Profession or Carry on Any Trade, Business, or Occupation under Article 19(1)(g) | Ensures the freedom to conduct various trades, businesses, and professions, often requiring Internet access. |
Mechanisms allowing Internet Shut-downs
| Mechanism | Authorities | Purpose |
| Temporary Suspension of Telecom Services (Public Emergency or Public Safety) Rules, 2017 | Home Departments in the states, state government review committee, central government (under this law, but rarely used) | Enforces shutdowns for public emergency or safety reasons. |
| Section 144 of the CrPC | Local law enforcement authorities | Enables shutdowns, particularly before 2017, to maintain public order and safety. |
| The Indian Telegraph Act, 1885, Section 5(2) | Home Secretary of the Union or state governments | Allows blocking of messaging during a public emergency, safeguarding public safety, or protecting sovereignty and integrity. |
Landmark Precedence: Anuradha Bhasin Judgment (2020)
- Supreme Court’s Ruling: In January 2020, the Supreme Court of India recognized access to the Internet as a fundamental right under the Indian Constitution.
- Restrictions Guidelines: The Court mandated that any government-imposed Internet restrictions must be temporary, limited, lawful, necessary, and proportionate. It also emphasized judicial review.
Unfulfilled Promises and Ongoing Restrictions
- Broken Promises: Despite the Anuradha Bhasin judgment, Internet shutdowns increased in India, making it the leader in global Internet suspensions.
- Recent Examples: The Union Territory of Jammu and Kashmir (J&K) and Haryana have imposed Internet restrictions without timely publication of orders.
- Compliance Issues: Lack of publication erodes public trust and limits the ability to challenge the legality of restrictions.
Need for Transparency
- Publication’s Significance: Non-disclosure of orders hinders legal challenges and perpetuates illegal restrictions.
- Statutory Recognition: The government’s failure to give statutory recognition to the Supreme Court’s directions creates awareness issues.
- Economic Impact: In 2020, India suffered $2.8 billion in losses due to 129 Internet shutdowns affecting 10.3 million individuals.
Widespread Impact
- Economic, Psychological, and Social Harm: Internet suspensions harm the economy and disrupt daily life, education, healthcare, and communication.
- Democratic Right to Protest: Restrictions on Internet access hinder the democratic exercise of the right to protest.
- Verifying Information: The Internet helps verify rumors and disseminate the truth during emergencies.
Socio-economic Disparities
- Mobile-Dependent Users: The majority of Internet users rely on mobile data services, making Internet restrictions detrimental to lower socio-economic groups.
- Broadband Accessibility: Limited access to broadband Internet exacerbates the impact of shutdowns.
Conclusion
- To uphold constitutional rights and unlock the full potential of Digital India, the government must adhere to the Supreme Court’s guidelines, ensuring transparency and legality in Internet shutdowns.
- Addressing compliance issues and minimizing restrictions can benefit the nation’s economic and social well-being.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
A colonial discourse on the veil
From UPSC perspective, the following things are important :
Prelims level: Na
Mains level: Historical evolution of the purdah system in various parts of the world, including India

Central Idea:
The article focus into the ongoing discourse around the hijab/veil, examining recent political events in India and the global conversation on the subject. It raises questions about the right of Muslim women to choose their attire, the role of the state in regulating religious clothing, and the intersection of Islamic principles with government policies. The central argument posits that criticisms of the hijab often lack genuine concern for gender equality, being influenced by historical Western colonial biases, and mirroring the majoritarian agenda of Hindutva.
Key Highlights:
- Karnataka Chief Minister’s stance on the hijab issue is presented as a case of vote bank politics by the Congress, reinforcing BJP’s accusations.
- The global debate involves Western leaders advocating for bans, while Muslim women protest against enforced veiling in countries like Iran.
- The article questions the Western perception of Islam’s treatment of women, attributing bias to a colonial mindset.
Key Challenges:
- Balancing individual freedom of choice with state regulations on religious attire.
- Navigating the intersection between Islamic provisions and state policies.
- Addressing the influence of Western colonial perceptions on the discourse around Muslim women’s rights.
Key Terms:
- Hijab/Veil: Islamic head covering worn by some Muslim women.
- Hindutva: Ideology advocating the cultural and political dominance of Hindus in India.
- Vote Bank Politics: Political strategy to gain support from specific religious or ethnic groups.
- Colonial Mindset: Biased perspectives influenced by historical colonial experiences.
Key Phrases:
- “Vote bank politics” – Refers to the alleged manipulation of Muslim sentiments for political gain.
- “Western colonial project” – Describes historical biases influencing perceptions of Islam.
- “Gender freedom” – The concept of freedom regarding gender roles and choices.
Key Quotes:
- “For Europe, Islam was a lasting trauma.” – Edward Said, highlighting the historical impact of colonialism on Western perceptions of Islam.
- “There is no inherent value placed on man and woman…no pre-ordained system of hierarchy.” – Amina Wudud, on interpreting Islamic provisions for gender equality.
Key Statements:
- The Congress government’s indecision on the hijab issue is portrayed as an example of vote bank politics.
- The author suggests a parallel between the Hindutva majoritarian agenda and Western colonial objectives in their disregard for equal rights.
Key Examples and References:
- French President Nicolas Sarkozy’s push for a total ban on the Islamic veil in 2010.
- British Prime Minister Boris Johnson’s controversial remarks on Muslim women wearing burqas in 2019.
- Examples of successful Muslim women in India, such as Parveen Babi and Zeenat Aman, who did not conform to hijab norms.
Key Facts and Data:
- Historical evolution of the purdah system in various parts of the world, including India.
- Instances of Western leaders advocating for bans on the Islamic veil.
Critical Analysis:
- The author critiques the perceived bias in Western views on Islam, attributing it to a colonial mindset.
- The alignment of Hindutva’s majoritarian ideology and Western colonial objectives is questioned.
- The article challenges the sincerity of concerns about gender equality by highlighting selective concerns based on political agendas.
Way Forward:
- Advocate for a nuanced understanding of cultural practices and religious choices.
- Encourage open dialogue between religious communities and policymakers to address concerns.
- Emphasize the importance of respecting individual choices while ensuring a balance with societal norms.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Personality rights: What they are, how have courts ruled
From UPSC perspective, the following things are important :
Prelims level: Judicial device of Injunction and related provisions
Mains level: Personality rights, debate its significance
What’s the news?
- The Delhi High Court this week allowed Kapoor’s pleas for protection of his personality rights from misuse by third parties. Rajinikanth’s name, Amitabh Bachchan’s baritone, and now Anil Kapoor’s style These are some of the personality rights that celebrities are trying to protect.
Central idea
- In recent times, celebrities have been increasingly vigilant about safeguarding their personality rights, which encompass elements such as their name, voice, signature, images, and distinctive features. The Delhi High Court’s recent decision to grant protection to Anil Kapoor’s personality rights from misuse by third parties has brought this issue into the limelight.
About personality rights
- Personality rights, often loosely referred to as the rights over one’s name, image, and unique characteristics, are crucial for celebrities.
- Many celebrities take proactive measures to protect their personality rights, including registering some of these distinctive aspects as trademarks.
- For example, Usain Bolt’s iconic bolting or lightning pose has been registered as a trademark, ensuring that only he or authorized parties can use it for commercial gain.
- The primary idea behind personality rights is to grant the individual the exclusive right to derive economic benefits from these distinctive features.
- Exclusivity is a critical factor in attracting commercial opportunities for celebrities, so unauthorized use by third parties can result in tangible financial losses.
Legal Protection for Personality Rights
- The law protects personality rights in India, although these rights are not explicitly mentioned in statutes. Instead, they are derived from related legal principles, primarily the right to privacy and the right to property.
- How the law safeguards personality rights in the absence of specific legislation?
- Right to Privacy and Right to Property: Personality rights are rooted in the broader concepts of the right to privacy and the right to property. These foundational rights form the basis for protecting an individual’s control over their personal identity and commercial interests.
- Application of Intellectual Property Concepts: Intellectual property principles, often used to protect trademarks, can be applied to safeguard personality rights. This includes preventing the unauthorized use of a celebrity’s identity or distinctive attributes for commercial purposes.
- Deterrence: Injunctions serve as a legal deterrent against the unauthorized commercial exploitation of a celebrity’s identity. They prohibit specific activities or uses of the celebrity’s persona, helping protect their financial interests.
- Challenges in Enforcement: While injunctions provide legal protection, enforcing them can be challenging. Celebrities often need to issue takedown orders to online intermediaries like Google to remove unauthorized content. These legal processes can incur significant costs but may still be beneficial compared to the financial losses resulting from unauthorized use.
Precedents in Indian Courts
- Indian courts have established important precedents in cases involving the protection of personality rights, particularly in the absence of specific legislation explicitly addressing these rights. Here are some notable precedents set by Indian courts:
- Amitabh Bachchan’s Case (November 2022):
- The Delhi High Court issued an injunction against the unauthorized use of Amitabh Bachchan’s personality rights. These included variations of his name, such as Big B, and his distinctive style, like addressing a computer as Computer ji and lock kiya jaye.
- The court relied on a 2012 order involving Bachchan, where Titan Industries had taken legal action against a jewelry store for using Bachchan’s images from a Tanishq advertisement. This precedent established the principle that personality rights can be protected in India.
- Rajnikanth’s Case (2015):
- The Madras High Court’s judgment in a case involving actor Rajnikanth established that personality rights apply to individuals who have attained celebrity status.
- Rajnikanth had filed a lawsuit against the producers of the movie Main Hoon Rajnikanth, claiming that the film’s use of his name, image, and style of delivering dialogue infringed on his personality rights.
- The court’s observation that personality rights vest in those who have become celebrities has been cited as an important precedent in subsequent cases.
What is an injunction?
- An injunction is a legal remedy issued by a court that orders a person or entity to either perform a specific action or refrain from doing a particular act.
- In the given content, when unauthorized third parties exploit a celebrity’s personality rights for commercial purposes, celebrities have the option to seek legal recourse by moving to court and requesting an injunction. An injunction is a court order that restrains or prevents the unauthorized use of these rights.
- It serves as a legal deterrent against the unauthorized commercial exploitation of a celebrity’s identity, helping to protect their financial interests.
Anil Kapoor’s Case
- Anil Kapoor’s recent case before the Delhi High Court resulted in an ex-parte, omnibus injunction against 16 entities using his name, likeness, image, and even deploying technological tools like artificial intelligence for commercial gain.
- An ex-parte injunction, issued without hearing the opposing party, and an omnibus injunction, which covers unauthorized uses not explicitly mentioned in the plea, serve as deterrents against misuse.
Challenges in enforcing injunctions
- Tracking Misuse: Even with an injunction in place, it is not easy to monitor and track all instances of unauthorized use of a celebrity’s personality rights. This is especially challenging in the digital age, where content can spread quickly across various platforms.
- Online Content: Unauthorized content can proliferate rapidly on the internet and social media platforms. Identifying and taking action against each instance of infringement can be a time-consuming and resource-intensive process.
- Global Reach: The internet allows content to be accessible globally. Celebrities may need to address unauthorized use not only within their own jurisdiction but also in other countries where their image and likeness are being exploited.
- Costs: Enforcing injunctions often involves legal expenses, including attorney fees and court costs. Pursuing legal action against multiple infringing parties can be financially burdensome, particularly for individuals.
- Response from Online Intermediaries: When unauthorized content is hosted or distributed through online intermediaries like search engines or social media platforms, getting these platforms to comply with takedown requests can be challenging. It may require legal processes and negotiations.
Criteria for Granting Injunctions
- In the Titan case, the HC, in its order, listed out the basic elements comprising the liability for infringement of the right of publicity.
- Validity of the right: The plaintiff must possess an enforceable right in their identity or persona.
- Identifiability of the celebrity: The defendant’s unauthorized use must make the celebrity easily identifiable.
- Intent to trade upon the celebrity’s identity: Evidence of the defendant’s intent to profit from the celebrity’s identity is crucial.
Conclusion
- The Delhi High Court’s decision in Anil Kapoor’s case highlights the evolving legal landscape surrounding personality rights in India. Celebrities are increasingly turning to the courts to protect their unique identities and the financial interests associated with them. As these cases continue to shape the legal framework, celebrities can seek redress against those who seek to exploit their personality rights for commercial gain.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Data Protection Bill 2023: What the law must do for children online
From UPSC perspective, the following things are important :
Prelims level: DPDP bill and provisions
Mains level: Vulnerability of children online and Data Protection
What’s the news?
- As a reworked version of the Digital Personal Data Protection Bill, 2022 (DPDP Bill) reaches Parliament, it is prudent to talk about one demographic that often receives less attention in the conversation on data privacy — children
Central idea
- With children constituting over 15 per cent of active internet users in the country and their online activities evolving rapidly, protecting their safety and privacy online has become a critical concern.
Vulnerability of children online
- Limited Understanding: Children often have limited understanding of the potential risks and consequences associated with sharing personal information online. They may not fully grasp the permanence and public nature of their digital footprint.
- Trust and Naivety: Due to their trusting nature, children can be easily deceived by online predators or malicious individuals who take advantage of their naivety.
- Lack of Experience: Many children lack the experience to recognize scams, phishing attempts, or deceptive content, making them more susceptible to online fraud and misinformation.
- Cyberbullying and Harassment: Children can become victims of cyberbullying, harassment, or online abuse, which can have severe psychological and emotional effects on their well-being.
- Inappropriate Content Exposure: Without proper supervision, children may stumble upon inappropriate or harmful content online, impacting their mental health and development.
- Social Media Pressure: Children may face pressure to conform to certain social media standards, leading to self-esteem issues and the desire to share personal information or engage in risky behaviors to fit in.
- Data Privacy Concerns: Children may unknowingly share sensitive data, such as location information, contact details, or pictures, making them potential targets for privacy breaches or data misuse.
- Lack of Parental Guidance: In some cases, parents may be less tech-savvy or unaware of their children’s online activities, leaving them exposed to online risks without proper guidance
How DPDP Bill ensures online safety for children?
- Definition of Minors: The DPDP Bill defines individuals under the age of 18 as minors. This definition acknowledges that children are particularly vulnerable and deserve additional safeguards for their personal data.
- Data Processing Obligations: The bill places three specific conditions on data processing entities when handling children’s data:
- Obtaining verifiable parental consent: As mentioned above, entities must ensure they have proper consent from a parent or guardian before processing a child’s data.
- Not causing harm to children: Data processing activities should not harm or exploit children in any way.
- Not tracking or targeting ads at children: Entities are prohibited from tracking children’s online behavior for targeted advertising purposes.
- Exemptions: The bill allows the government to exempt certain entities from the requirement of parental consent and tracking and targeting ads for specific purposes. However, such exemptions must be for the best interests of a child.
Why a graded approach is necessary?
- Age Diversity and Developmental Stages: Children’s maturity levels vary across different age groups. A rigid age requirement may not consider the developmental stages of children, leading to over- or under-protection of their data.
- Balancing Access and Protection: A graded approach allows for a balance between age-appropriate access to digital services and data protection. It enables children to access educational platforms while imposing stricter age-gating for services with higher privacy risks.
- Promoting Digital Literacy: Gradually exposing children to digital platforms with age-appropriate content fosters digital literacy and responsible online behavior from an early age.
- Preventing Misrepresentation: A strict age-gating requirement might encourage children to misrepresent their age to access certain services, defeating the purpose of data protection measures.
- Adapting to Technological Advancements: The digital landscape is dynamic, with new services constantly emerging. A graded approach allows for flexibility in adjusting age requirements as technology evolves.
Way forward
- Graded Approach Implementation: Adopt a graded and risk-based approach to age-gating for accessing different digital services. This approach allows the government to set varied age thresholds based on privacy risks, ensuring age-appropriate access while protecting children’s data.
- Clear Guidelines for Age Verification and Consent: Provide clear and reliable mechanisms for age verification and obtaining parental consent. Ensure that these mechanisms adhere to data protection principles like data minimization and purpose limitation to prevent unintended data collection.
- Defining Verifiably Safe Manner: Articulate core principles of what qualifies as a verifiably safe manner for processing children’s data to avoid ambiguity. This will guide data processing entities in ensuring children’s safety and privacy.
- Promoting Digital Literacy: Develop and implement digital literacy programs that educate children about online risks and responsible behavior. These initiatives should be integrated into school curricula, and awareness campaigns for parents and guardians should be conducted.
- Parental Guidance and Involvement: Encourage active parental involvement in their children’s online activities. Provide resources and workshops to help parents understand the digital world and support their children in using digital services safely.
- Collaboration with Tech Companies: Engage with technology companies to develop age-appropriate interfaces, privacy settings, and content filters. Prioritize child safety in the design and features of digital platforms.
- Robust Reporting Mechanisms: Establish accessible and user-friendly reporting mechanisms for inappropriate content, cyberbullying, or any other online harm targeting children. Promptly address reported issues and take appropriate actions.
Conclusion
- As India deliberates on various laws and policies to regulate the internet, it is crucial to prioritize the needs and interests of children. Protecting children’s data privacy will not only secure their online experiences but also foster responsible digital citizenship from an early age
Also read:
[Sureshot]Digital Personal Data Protection (DPDP) Bill, 2022
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Centre withdraws DNA Bill
From UPSC perspective, the following things are important :
Prelims level: DNA
Mains level: Genetic Profiling, Issues

Central Idea
- The Union government recently withdrew the DNA Technology (Use and Application) Regulation Bill, 2019, from the Lok Sabha.
DNA Bill, 2019: Highlights
- The Bill, first proposed in 2003, aims to establish a regulatory framework for obtaining, storing, and testing DNA samples of individuals, primarily for criminal investigations and establishing identity.
- Over the years, the Bill has undergone changes and was referred to the Parliamentary Standing Committee in 2019.
- The committee raised concerns about potential misuse based on religion, caste, or political views.
Key Features
- Objective: The Bill sought to create a regulatory framework for DNA sample collection, testing, and storage, primarily for criminal investigations and establishing a person’s identity.
- Existing Uses of DNA Technology: DNA testing is already employed for criminal investigations, parentage establishment, and locating missing individuals.
- Proposed Institutional Structures: The Bill aimed to establish a DNA regulatory board and a DNA data bank at the national level, with the possibility of regional centers at the state level.
- Role of the DNA Regulatory Board: The board would frame guidelines and rules for DNA collection, testing, and storage.
- DNA Data Bank: The data bank would store all DNA samples collected under specified rules.
- Restricted Testing: DNA sample testing would be allowed only at laboratories authorized by the regulatory board.
- Handling of DNA Samples: The Bill specified the circumstances under which individuals could be asked to submit DNA samples, the purposes for such requests, and the exact procedures for handling, storing, and accessing these samples.
Controversies and Objections against the Bill:
- Reliability of DNA Technology: Critics raised concerns about the foolproof nature of DNA technology and its potential for error.
- Risk of Misuse: The main debate centered on the possibility of abuse of DNA information. Detractors feared that intrusive DNA data collection and storage could lead to misuse and violations of individual privacy.
- Privacy Concerns: DNA information reveals not only a person’s identity but also physical and biological attributes such as eye, hair, or skin color, susceptibility to diseases, and possible medical history. Critics argued that storing such personal information could compromise privacy rights.
Standing Committee’s Concerns
- Technical and Sensitive Nature: The Standing Committee’s report acknowledged that the Bill was technical, complex, and sensitive.
- Addressing Fears: The report recognized and addressed concerns expressed by several members about the potential misuse of DNA technology based on factors like religion, caste, or political views.
Government’s Defense of the Bill
- International Precedents: The government argued that nearly 60 countries have enacted similar legislation, justifying the need for such a law in India.
- Limited Information Storage: The government contended that only a limited set of numbers, just 17 out of the billions that DNA samples can reveal, would be stored in the indices. This information would act as a unique identifier and not reveal any personal details.
Conclusion
- The withdrawal of the Bill marks a pause in the government’s efforts to create a regulatory framework for DNA technology usage.
- The controversies and objections raised highlight the need for a balanced approach.
- The Centre must address concerns over misuse and privacy while harnessing the potential benefits of DNA technology for criminal investigations and other purposes.
Back2Basics: DNA
- DNA, or deoxyribonucleic acid, is a molecule that carries the genetic instructions necessary for the growth, development, functioning, and reproduction of all known living organisms and many viruses.
- It is often referred to as the “building blocks of life.”
Key features of DNA include:
- Molecular Structure: DNA is a double-stranded molecule, consisting of two long chains of nucleotides that form a double helix. Each nucleotide consists of a sugar molecule (deoxyribose), a phosphate group, and one of four nitrogenous bases: adenine (A), thymine (T), cytosine (C), and guanine (G).
- Base Pairing: The two DNA strands are held together by hydrogen bonds between complementary base pairs. Adenine (A) always pairs with thymine (T), and cytosine (C) always pairs with guanine (G).
- Genetic Code: The sequence of nucleotide bases along the DNA strand constitutes the genetic code, which determines the specific traits and characteristics of an organism.
- Genes: DNA is organized into specific segments called genes, which are responsible for encoding proteins or functional RNA molecules. Proteins play a crucial role in various biological processes, while RNA molecules contribute to gene expression and protein synthesis.
- Replication: DNA has the unique ability to replicate itself through a process called DNA replication. During cell division, the DNA unwinds, and each strand serves as a template for the synthesis of a new complementary strand, resulting in two identical DNA molecules.
- Inheritance: DNA is passed from one generation to the next through reproduction, ensuring the transmission of genetic information from parents to offspring.
- Role in Protein Synthesis: DNA provides the instructions for protein synthesis through a two-step process. First, the information in a gene is transcribed into a messenger RNA (mRNA) molecule. Then, the mRNA is translated by ribosomes in the cell to produce specific proteins.
- Genetic Variation: Mutations, or changes in the DNA sequence, can lead to genetic variation within a species. These variations are essential for evolution and adaptation to changing environments.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
An unacceptable verdict in the constitutional sense
From UPSC perspective, the following things are important :
Prelims level: Related Constitutional provisions
Mains level: Significance of constitutional tenets in safeguarding individual rights and personal choice, Constitutional morality and personal liberty and various Supreme court Judgment's in this regard
What is the news?
- A recent judgment by the Allahabad High Court in the case of Kiran Rawat vs State of UP.
- The court declined the prayer of an inter-faith couple in a live-in relationship for protection from police harassment.
- The court deemed the live-in relationship as a “social problem” and relied on personal laws on marriage
Central Idea
- A recent judgment by the Allahabad High Court has garnered significant national attention. The ruling in Kiran Rawat vs State of UP undermines the principles of constitutional morality in personal relationships, a notion repeatedly affirmed by the Supreme Court of India. The judgment, has been criticised for its departure from constitutional principles, disregard for precedent, and reliance on irrelevant personal laws.
What is the case?
- The case of the petitioners, a Muslim man and a Hindu woman, was short and simple. They are around 30 years of age, living together and their relation is based on mutual love and affection.
- They alleged that the local police have been torturing them while living in a rented house, and sought protection from police harassment, allegedly done on the basis of a complaint made by a family member
What is mean by constitutional morality?
- Constitutional morality refers to the principles and values embedded in a constitution that guide the interpretation and application of its provisions.
- It encompasses the spirit and objectives of the constitution, promoting justice, equality, freedom, and the protection of fundamental rights.
- Constitutional morality goes beyond conventional social norms and customs, emphasizing the adherence to constitutional principles even in the face of opposition or prevailing societal beliefs.
What is personal liberty?
- Personal liberty refers to the individual’s freedom to make choices, decisions, and actions without undue interference or coercion from external forces, including the state or other individuals.
- It is a fundamental right that is protected by various legal frameworks, including constitutions and human rights declarations.
- Personal liberty encompasses various aspects of an individual’s life, including physical, mental, and emotional well-being, as well as their autonomy and privacy.
- However, personal liberty is not an absolute right and may be limited in certain circumstances,
Main factors that make the judgment unacceptable in the constitutional sense
- Prioritizing Conventional Social Morality: The High Court is accused of being influenced by conventional social morality rather than upholding constitutional principles. This undermines individual autonomy and personal liberty, which are essential components of constitutional morality.
- Disregard for Supreme Court Judgments: Despite citing Supreme Court judgments on live-in relationships, the High Court rejects their intended purpose without providing sound reasons. This undermines the binding nature of Supreme Court judgments and the consistency of legal interpretation.
- Irrelevant Reliance on Personal Laws: The judgment relies on personal laws related to marriage that are deemed irrelevant to the case. By doing so, the High Court deviates from the constitutional framework and fails to prioritize the fundamental rights of individuals.
How the judgement shows an inclination towards orthodoxy?
- Assuming Marriage as a Condition Precedent: Though there were many deficits in the petition, the High Court could not have assumed that marriage is a condition precedent for constitutional protection and the exercise of fundamental rights.
- Acting as a Theological Court: In effect, The High Court acted as a theological court, as if the very idea of individual liberty and autonomy are alien to the writ jurisdiction. The verdict shows a clear inclination towards social orthodoxy and religious revivalism.
- Reiteration of Traditional Beliefs:
- The court tried to reiterating traditional beliefs on marriage and morals, rather than embracing a progressive and inclusive approach. By relying on and reinforcing traditional views, the court fails to accommodate changing societal norms and the importance of personal choices and freedoms
- Rejection of Supreme Court Precedents: The law laid down by the Supreme Court is binding on all the courts in the country, as in Article 141 of the Constitution. The judgment of the Allahabad High Court rejects the precedential value of Supreme Court verdicts on live-in relationships, such as D. Velusamy (2010), Indra Sarma (2013), and Dhanu Lal (2015). By doing so, the High Court disregards the guidance provided by the apex court, which has recognized and protected the rights of individuals in live-in relationships.
The Judgements by the Supreme Court which upholds personal liberty
- Decriminalization of Adultery in Joseph Shine vs Union of India (2018): In the case of Joseph Shine vs Union of India (2018), the Supreme Court decriminalized adultery defined under Section 497 of the Indian Penal Code (IPC). The court held that individual moral aberrations should not be punished by the state’s police power. The judgment emphasized that fidelity is a value, but not one that the state should police.
- Striking Down of Section 377: In the case of Navtej Singh Johar (2018), the Supreme Court substantially struck down Section 377 of the IPC, which dealt with same-sex relations. The court’s judgment was a constitutional adjudication rather than a mere moral judgment. It recognized the importance of personal choices and limited the state’s power in the realm of personal relationships.
- In Lata Singh (2006) case: The SC t directed police authorities throughout the country to see to it that any adult undergoing inter caste or inter religious marriage is not harassed by anyone.
- Khushboo vs Kanniammal & Anr. (2010): The Supreme Court held, while it is true that the mainstream view in our society is that sexual contact should take place only between marital partners, there is no statutory offence that takes place when adults willingly engage in sexual relations outside the marital setting.
Note: Note down these judgements to support your argument when question asks you to critically analyse
Way forward
- Clear Guidance on Live-in Relationships: The Supreme Court should provide clear guidelines and legal recognition for live-in relationships, emphasizing the protection of individuals’ rights and dignity. This would prevent confusion and inconsistent interpretations by lower courts in the future.
- Judicial Training and Sensitization: There is a need to conduct training programs and sensitization workshops for judges at all levels. This would ensure a better understanding of constitutional principles, fundamental rights, and the evolving nature of societal norms, enabling judges to make informed and unbiased decisions.
- Public Awareness Campaigns: Public awareness campaigns should be conducted to educate people about the rights and legal protections available to individuals in live-in relationships. This would help dispel social stigmas and promote acceptance of diverse personal choices.
- Legislative Reforms: The legislature should consider enacting specific laws or amending existing ones to address the legal rights and responsibilities of individuals in live-in relationships. This would provide clarity and protection to couples in such relationships and ensure equal treatment under the law.
- Strengthening Precedent: It is crucial to emphasize the binding nature of Supreme Court judgments on all courts in the country. Lower courts should be vigilant in adhering to established precedents, respecting the hierarchy of judicial decisions, and avoiding interpretations that deviate from constitutional principles.
- Dialogue and Engagement: Societal dialogue and engagement with stakeholders, including legal experts, activists, and religious leaders, can help promote a better understanding of individual rights, personal choices, and the importance of constitutional values in a diverse society
Conclusion
- The Allahabad High Court’s judgment in Kiran Rawat vs State of UP reflects a regressive view on personal relationships and disregards constitutional morality. By neglecting Supreme Court judgments, relying on irrelevant personal laws, and failing to uphold personal liberties, the High Court has erred in its duty to provide justice. It is crucial that the Supreme Court rectifies this judicial indiscipline and reaffirms the significance of constitutional tenets in safeguarding individual rights and personal choice
Also read:
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Age of Consent for Data Protection
From UPSC perspective, the following things are important :
Prelims level: Age of Consent
Mains level: Read the attached story

Central Idea
- Empowering the Central Government: The upcoming data protection Bill in India could grant the Centre the authority to lower the age of consent from 18 for accessing Internet services without parental oversight.
- Exemptions for Certain Companies: The Bill may exempt specific companies from additional obligations in protecting children’s privacy if they can process data in a “verifiably safe” manner.
Must read:
Why in news?
- Departure from Previous Bill: This marks a departure from the previous data protection Bill, where the age threshold was hard-coded at 18 years.
- Aligning with global laws: The change aligns with data protection regulations in the Western world, such as the EU and US.
Journey of a Clause: Changing Definition of a Child
- Justice BN Srikrishna Committee Report: The committee’s 2018 report recommended seeking parental consent for individuals under 18 years but suggested that the age of consent could be reduced if amendments were made.
- Personal Data Protection Bill, 2019: The PDP Bill, 2019 retained the recommendation and defined a child as an individual under the age of 18.
- Joint Committee of Parliament Recommendations: The Joint Committee proposed reducing the age of consent to 13/14/16 years in its final recommendations in late 2021.
- Digital Personal Data Protection Bill, 2022: The draft Bill defined children as those under 18 years of age, leading to dissatisfaction among social media companies.
- Final Change: The data protection Bill headed to Parliament’s Monsoon session reportedly changed the definition of a child to an individual who has not completed the age of eighteen years or a lower age notified by the Central Government.
Global Definitions of Children for Data Regulations
- EU’s General Data Protection Regulation (GDPR): The age of consent is set at 16 but allows member states to lower it to as low as 13. Specific protections for children’s personal data exist.
- USA’s Children’s Online Privacy Protection Act (COPPA): Children are defined as under 13 years, and parental consent is required for processing their personal data.
- Australia’s Privacy Act, 1988: The Act protects personal information regardless of age but requires organizations to assess an individual’s capacity to consent on a case-by-case basis.
- China’s Personal Information Protection Law (PIPL): Entities handling personal data of individuals under 14 years must obtain parental consent, and children’s data is categorized as sensitive.
Conclusion
- Lowering the age of consent in India’s data protection Bill reflects global trends seen in data protection regulations.
- Countries have different age thresholds for defining children and varying requirements for obtaining parental consent.
- The final change in the Bill represents a series of discussions and deliberations on determining the age of children in India’s data protection law, addressing concerns of industry stakeholders and aligning with international standards.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Cabinet clears Data Protection Bill
From UPSC perspective, the following things are important :
Prelims level: NA
Mains level: DPDP Bill
Central Idea
- The Union Cabinet has granted clearance for the Digital Personal Data Protection (DPDP) Bill, which is set to be introduced in the upcoming Monsoon Session of Parliament.
- This legislation aims to regulate the management of personal data of Indian residents, emphasizing explicit consent for data collection and usage.
DPDP, Bill: Key Features and Concerns
(A) Data Protection Norms and Consent
- Data Protection Law: The DPDP Bill establishes norms for the management of personal data and mandates explicit consent from individuals whose data is collected and used.
- Limited Transparency: More than 20,000 comments were received during the public consultation on the draft Bill, but these comments have not been made publicly available.
- Minimal Changes: The final Bill, to be presented in Parliament, reportedly shows little deviation from the initial draft circulated for public consultation.
(B) Data Protection Board and Grievance Redressal
- Role of the Data Protection Board: The DPDP Bill enables individuals to lodge complaints with the Data Protection Board of India, consisting of government-appointed technical experts, in case of unauthorized data usage.
- Investigation of Breaches: The Board will initiate an investigation into reported breaches of personal data.
(C) Provisions and Penalties
- EU Influence: The DPDP Bill draws inspiration from the EU’s General Data Protection Regulation, outlining practices for entities collecting personal data, storage, processing, and the rights of data subjects.
- Voluntary Undertaking: Entities can admit a breach and pay a penalty as a mitigation measure to avoid court litigation.
- Penalties and Fines: Penalties for breaches can reach up to ₹250 crore, with a possibility of upward revision to ₹500 crore. Individual offenses may attract fines starting from ₹10,000.
- Data Protection Board’s Role: The Board will levy fines and penalties for breaches, with a maximum penalty of ₹500 crore for data breaches.
(D) Exemptions and Concerns
- Exemptions for Courts and Law Enforcement: The Bill exempts courts and law enforcement agencies from certain requirements when processing personal data for the prevention, detection, investigation, or prosecution of offenses.
- Concerns over RTI Amendment: An amendment in the DPDP Bill raises concerns among Right to Information activists, as it may restrict the sharing of “personal information” by government departments, potentially impeding transparency and accountability.
Potential Changes in the Final Draft
- Cross-Border Data Flows: The approach to cross-border data transfers may shift from a ‘whitelisting’ approach to a ‘blacklisting’ mechanism.
- Stricter Deemed Consent: The provision on “deemed consent” for private entities could be reworded to be more stringent, while government departments may assume consent for processing personal data in the interest of national security and public interest.
International Comparisons

- Global Data Protection Laws: A significant number of countries have enacted data protection and privacy legislation, with the GDPR serving as a template for many jurisdictions.
- EU, US, and China Models: The EU focuses on comprehensive data protection, the US emphasizes privacy as “liberty protection,” and China has introduced new laws on data privacy and security.
Why discuss this yet again?
- Previous Withdrawal: An earlier version of the data protection Bill was withdrawn from Parliament in 2021 due to pushback from various stakeholders.
- International Relevance: The DPDP Bill’s implementation is crucial for India’s trade negotiations, particularly with regions like the European Union, which has comprehensive privacy laws under the General Data Protection Regulation (GDPR).
Conclusion
- The Bill marks a significant step toward safeguarding personal data in India.
- The legislation introduces stricter norms for data collection and usage, emphasizing explicit consent and establishing penalties for breaches.
- However, concerns have been raised regarding the limited transparency of the consultation process and potential exemptions that may impact transparency and accountability.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
CoWIN Data Breach: Data Privacy and Security Concerns in India’s Digitalization Journey
From UPSC perspective, the following things are important :
Prelims level: Personal Data Security in India
Mains level: Digital India mission and concerns over the data breach and cyber security laws
Central Idea
- The recent CoWin data leak has raised significant concerns about data privacy and security in India. While the leak itself is disconcerting, what is more troubling is the government’s response to the issue. Mere assurances that the back-end database is still secure do little to alleviate the concerns of citizens.
CoWIN Data Breach and Government Denials
- Data Breach: On June 12, a data breach on the CoWIN platform was reported by the Malayala Manorama and online portal “The Fourth.” Personal details, including vaccination information and identification numbers, were found circulating on the messaging platform Telegram.
- Government Denials: Despite the mounting evidence of the data breach, the Ministry of Health and Family Welfare and Minister of State, Ministry of Electronics and IT (MEITY), responded with denials. The Ministry of Health and Family Welfare labeled the reports as “mischievous,” while the Minister of State, MEITY, claimed that the sensitive information had emerged from previously stolen data.
- Press Information Bureau Statement: Later in the day, the PIB issued a statement asserting the complete safety of the Co-WIN portal and its adequate safeguards for data privacy. However, the credibility of this statement was questionable, given the initial denials and the substantial evidence of the breach.
- Lack of Transparency: The government’s response to the CoWIN data breach exemplifies a recurring pattern of denial and opacity in addressing data breaches in the public sector. Previous incidents, such as the Employees’ Provident Fund Organisation breach and the ransomware attack on AIIMS, have been met with similar denials and lack of transparency.
- Erosion of Trust: The consistent lack of transparency, coupled with the absence of a National Cyber Security Strategy and data protection laws requiring breach notifications to affected users, has eroded citizens’ trust in the government’s ability to secure their personal information. T
Articulating Threat Models for Robust Security
- Adversaries Corrupting Insiders: The threat model assumes that adversaries can corrupt all insiders, including system administrators and personnel with authorized access.
- Compromised Custody Chains: The threat model includes the possibility of adversaries compromising the custody chains of data, which may involve unauthorized access or tampering with data during its lifecycle.
- Compromised Hardware and Software: The threat model assumes that adversaries can compromise both hardware and software components, potentially exploiting vulnerabilities in these systems.
Challenges in Indian Digitalization Initiatives
- Limited Infrastructure: One of the significant challenges in Indian digitalization initiatives is the limited infrastructure, especially in rural areas. Inadequate internet connectivity, lack of reliable power supply, and limited access to digital devices pose obstacles to the effective implementation of digital services.
- Digital Divide: India faces a significant digital divide, with a large section of the population having limited or no access to digital technologies. This divide is often along socio-economic lines, with marginalized communities and rural areas facing more significant barriers to digital inclusion.
- Data Security and Privacy: Ensuring data security and privacy is a persistent challenge in Indian digitalization efforts. Incidents of data breaches, leaks, and unauthorized access to personal information highlight the need for robust data protection frameworks and stringent security measures.
- Cybersecurity Threats: With the expansion of digital services, the risk of cybersecurity threats such as hacking, phishing, malware attacks, and ransomware has increased. The government and relevant stakeholders need to invest in cybersecurity infrastructure and raise awareness about safe digital practices.
- Skill Gaps and Digital Literacy: Many individuals, particularly in rural areas, lack the necessary digital skills and literacy to effectively utilize digital services. Bridging the digital skills gap and promoting digital literacy are essential for the successful adoption of digitalization initiatives.
- Interoperability and Standardization: The lack of interoperability and standardization among different digital systems and platforms hampers the seamless integration of services. It creates complexities in data sharing, collaboration, and the overall user experience.
- Legal and Regulatory Frameworks: Developing comprehensive and up-to-date legal and regulatory frameworks for digitalization is crucial. It includes laws related to data protection, privacy, electronic signatures, cybercrime, and digital transactions. Ensuring these frameworks are robust and aligned with international best practices is necessary for building trust and confidence in digital services.
Consequences of Inadequate Privacy Risk Assessment
- Data Breaches and Leaks: Inadequate privacy risk assessment can lead to data breaches and leaks, exposing sensitive personal information to unauthorized access. This can result in identity theft, financial fraud, and other forms of misuse of personal data.
- Privacy Violations: Insufficient assessment of privacy risks can result in privacy violations, where individuals’ personal information is used or disclosed without their consent or in ways that infringe upon their privacy rights. This can erode trust in digital services and undermine individuals’ confidence in sharing their data.
- Loss of Control over Personal Information: Without proper risk assessment, individuals may lose control over their personal information. This can lead to the unauthorized collection, storage, and use of their data by both private and public entities, potentially exposing them to various risks and harms.
- Discriminatory Practices: Inadequate privacy risk assessment can contribute to discriminatory practices, where personal data is used to profile individuals based on sensitive attributes such as race, religion, gender, or political beliefs. This can lead to unfair treatment, exclusion, and perpetuation of bias in decision-making processes.
- Societal Harms: Privacy breaches resulting from inadequate risk assessment can have broader societal impacts. For example, leaked personal information can be exploited for political manipulation, voter profiling, or predatory advertising, potentially influencing elections, public opinions, and individual choices.
- Erosion of Trust: When privacy risks are not adequately assessed and addressed, it can erode public trust in digital services, government initiatives, and the overall data ecosystem. Lack of trust can hinder the adoption of digital technologies, impede economic growth, and undermine the potential benefits of digitalization.
- Legal and Regulatory Consequences: Inadequate privacy risk assessment may lead to non-compliance with data protection laws and regulations, potentially resulting in legal consequences, penalties, or lawsuits. Failure to protect individuals’ privacy rights can attract regulatory scrutiny and damage the reputation of organizations or government entities involved.
Way ahead: The Need for Standardized Grammar in Security and Privacy Discourse
- Defining Threat Models: Establishing well-articulated threat models is crucial. This involves identifying potential risks, vulnerabilities, and capabilities of adversaries. It provides a common starting point for discussions and allows stakeholders to align their understanding of security and privacy concerns.
- Promoting Best Practices: Encourage the adoption of best practices in security and privacy. This includes following internationally recognized standards and frameworks, such as those provided by organizations like the National Institute of Standards and Technology (NIST) or the International Organization for Standardization (ISO).
- Clear Communication of Security Measures: System designers and administrators should precisely articulate the security measures implemented to address specific threats. It is important to go beyond vague claims of “state-of-the-art best practices” and provide concrete details on how security and privacy issues are being tackled.
- Publicly Articulating Threat Models: Digital service providers and government agencies should publicly articulate their threat models. By doing so, they demonstrate transparency, foster trust, and allow stakeholders to assess the adequacy of security measures in place.
- Collaboration and Knowledge Sharing: Encourage collaboration and knowledge sharing among stakeholders involved in security and privacy discourse. This can be done through forums, conferences, and working groups where experts can share experiences, insights, and best practices.
- Developing Common Terminology: Establish a common terminology and vocabulary for discussing security and privacy concepts. This helps to avoid misunderstandings and ensures that stakeholders are on the same page when discussing security risks and mitigation strategies.
- Education and Training: Invest in education and training programs to enhance the understanding of security and privacy concepts among professionals, policymakers, and end-users. This includes promoting cybersecurity awareness and digital literacy to empower individuals to make informed decisions about their privacy.
- Regulatory Frameworks: Develop comprehensive and up-to-date regulatory frameworks that incorporate standardized security and privacy measures. These frameworks should address specific threat models, outline data protection requirements, and establish accountability mechanisms for organizations handling personal data.
- Independent Audits and Certifications: Encourage independent audits and certifications of digital systems to verify their adherence to standardized security and privacy practices. This helps build trust and provides assurance to users that appropriate measures are in place to protect their data.
Conclusion
- India’s digitalization journey has been remarkable in its scale and scope, but there is a pressing need to reinforce it with computer science rigor. Strengthening data security and privacy practices is paramount to ensure public trust and the success of digital public services. With a well-structured approach, India can leverage the benefits of digitalization while safeguarding the privacy and security of its citizens’ data.
Also read:
| CoWIN Vaccination Data Breached |
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
HC Observations over Right to Change Name
From UPSC perspective, the following things are important :
Prelims level: Change of Name under Article 21
Mains level: Not Much
Central Idea
- Allahabad High Court has allowed a man to change his name citing fundamental rights under Articles 19(1) (a), 21, and 14.
- Delhi High Court permitted two brothers to reflect their father’s changed surname on their Board certificates, asserting the right to identity as an intrinsic part of the right to life under Article 21.
| Article | Summary |
| Article 19(1)(a) | Freedom of speech and expression: Citizens have the right to express their opinions and ideas freely, with reasonable restrictions to safeguard national interests and public order. |
| Article 21 | Right to life and personal liberty: Individuals are protected from arbitrary deprivation of life or liberty and have the right to live with dignity. It includes the right to privacy and encompasses various aspects of human rights. |
| Article 14 | Right to equality: All individuals are entitled to equal protection under the law, ensuring fairness and prohibiting discrimination based on religion, race, caste, sex, or place of birth. It promotes equality before the law for all citizens. |
Right to Change Name
- The right to change one’s name is recognized as a fundamental right under Article 21 of the Constitution, which guarantees the right to life and personal liberty.
- It is often exercised for various reasons, including personal preferences, religious conversions, marriage or divorce, or to overcome social or cultural barriers.
- Individuals may choose to change their names to reflect their gender identity, religious beliefs, or to align with their professional or artistic pursuits.
Process to change the name
- Prepare a petition stating the desire to change the name and reasons for the change.
- Prepare an affidavit affirming the intention to change the name and get it notarized.
- Publish a notice in two local newspapers announcing the name change.
- Apply for Gazette notification through the Department of Publication.
- Gather supporting documents like identity and address proof.
- File the petition, affidavit, and supporting documents in the appropriate court.
- Attend the court hearing and provide necessary explanations.
- Obtain a court order approving the name change.
- Update official documents with the new name.
Observations by the HCs
- Allahabad High Court ruled that the rejection of the name-change applications by the authorities violates fundamental rights guaranteed under Articles 19(1)(a), 21, and 14.
- It emphasized the need for congruence in all identity-related documents and the prevention of confusion and potential misuse.
- Delhi High Court asserted the right to identity as an intrinsic part of the right to life under Article 21.
Restrictions on the Right to Change Names
- Although the right to change names is a fundamental right, it is subject to reasonable restrictions.
- Restrictions imposed by law must be fair, just, and reasonable.
- Principle of proportionality and the value of human dignity play important roles in determining the reasonableness of restrictions (Jeeja Ghosh vs. Union of India, 2016).
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
CoWIN Vaccination Data Breached
From UPSC perspective, the following things are important :
Prelims level: CoWIN
Mains level: Personal Data Security in India

Central Idea
- Data breach reports: The Health Ministry, on Monday, refuted claims of a data breach of COVID vaccination beneficiaries, stating that such reports were baseless and mischievous in nature.
- Investigation by CERT-In: The Indian Computer Emergency Response Team (CERT-In) has been asked to investigate the alleged data breach issue and submit a report to ascertain the facts.
- Assurance of data safety: The Ministry maintains that the CoWIN (Covid Vaccine Intelligence Network) portal is completely safe, equipped with adequate safeguards to protect data privacy.
About CoWIN
- Development: CoWIN was developed and is owned and managed by the Ministry of Health.
- Policy decisions: The Empowered Group on Vaccine Administration (EGVAC), chaired by the former CEO of the National Health Authority, oversees this. It includes members from the Health Ministry and MeitY (Ministry of Electronics and Information Technology).
Evaluation of Alleged Breach
- CERT-In review results: The review conducted by CERT-In concludes that there was no direct breach of the CoWIN app or database.
- Data source of Telegram bot: The data accessed by the Telegram bot was sourced from a separate threat actor database, which contained previously breached or stolen data.
- No direct breach of CoWIN: The Ministry states that it does not appear that the CoWIN app or database itself was directly breached.
Clarification on CoWIN Data Access
- Three methods of data access: The Ministry outlines the three ways in which data can be accessed on the CoWIN portal: user access, vaccinator access, and authorized third-party applications.
- Data sharing with Telegram bot: The Ministry clarifies that data cannot be shared with the Telegram bot without undergoing the one-time password (OTP) authentication process.
- Limited data collection: CoWIN only collects the year of birth and does not capture a person’s address.
Unanswered Questions and API Access
- Uncertainty regarding recent breaches: The Ministry has not explicitly clarified whether the CoWIN database was breached recently or in the past.
- Lack of insights on bot accuracy: The Ministry’s statement does not offer insight into the accuracy of the Telegram bot’s retrieval of citizens’ data from the CoWIN database.
- API access without OTP: The Ministry admits the existence of an API that allows data sharing without OTP, but emphasizes that requests are accepted only from trusted whitelisted APIs.
Concerns and Aadhaar Data
- Accuracy of Aadhaar details: The accuracy of displaying Aadhaar numbers corresponding to mobile numbers raises concerns, as the government has never publicly acknowledged any breaches of Aadhaar data.
- Need for clarity: The Ministry’s statement does not provide clarity on how the Telegram bot accurately displayed Aadhaar numbers.
- Addressing security concerns: The Ministry should address concerns regarding the security of Aadhaar data and provide transparency on its safety measures.
Future Steps and Data Governance Policy
- Empowering CERT-In: The Health Ministry has requested a final report from CERT-In to investigate the alleged data breach incident thoroughly.
- National Data Governance policy: The Ministry highlights the finalization of the National Data Governance policy, which aims to establish a common framework for data storage, access, and security standards across the government.
- Awaited response from CERT-In: The Ministry is awaiting a response from CERT-In regarding the issue, which will provide further insights into the nature of the breach.
Assurance and Previous Leaks
- Assurances of secure infrastructure: Health authorities maintain that CoWIN has state-of-the-art secure infrastructure and has never experienced a security breach.
- Dismissal of previous claims: Previous claims of data leaks, such as the ‘Dark Leak Market’ incident, were dismissed by health authorities, emphasizing the safety of citizen data.
- Security measures in place: CoWIN has implemented security measures such as web application firewall, regular vulnerability assessments, and OTP authentication to ensure the protection of data.
Implications of this data leak
- Identity theft risks: The leaked data exposes individuals to the risk of identity theft, as sensitive information can be misused for fraudulent activities.
- Targeted scams and phishing attacks: With access to personal details, scammers may attempt targeted scams and phishing attacks, leading to financial loss and potential harm to individuals.
- Loss of trust in government systems: The data breach undermines public trust in the government’s ability to safeguard sensitive information, affecting confidence in the vaccination program and other government initiatives.
- Reputational damage: The incident could tarnish the reputation of the CoWIN platform and associated government agencies, affecting their credibility in managing sensitive data.
- Impact on future vaccination drive: Concerns about data security may deter individuals from participating in the vaccination program, slowing down efforts to control the spread of COVID-19.
- Calls for accountability: The data leak prompts demands for accountability from the responsible government agencies and the implementation of stricter measures to protect citizen data.
Conclusion
- The data leak incident related to the CoWIN portal raises serious concerns about the privacy and security of individuals’ personal information.
- While the Ministry of Health maintains that the CoWIN app and database were not directly breached, the access to sensitive data through a Telegram bot raises questions about the integrity of the system.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Data Protection Bill in Monsoon Session
From UPSC perspective, the following things are important :
Prelims level: Read the attached story
Mains level: Data Privacy and Protection

The Union government informed the Supreme Court that a new law, namely the Digital Personal Data Protection Bill, 2022, to enforce individual privacy in online space was “ready”.
Legislation on ‘Data’: A Backgrounder
- The personal data protection bill has been in the works for about five years.
- The first draft of the Bill was presented by an expert panel headed by Justice B.N. Srikrishna in July 2018, after a year-long consultation process.
Timeline of key events

- July 2018: After a year of consultations and deliberations, the PDP Bill, 2018, drafted by an expert committee headed by Justice BN Srikrishna, is presented to MeitY. Subsequently, MeitY begins drafting the next iteration of the Bill.
- December 2019: The PDP Bill, 2019, prepared by MeitY, is referred to a Joint Parliamentary Committee (JPC) for review.
- December 2021: After multiple extensions, and a leadership change, JPC Chairperson tabled the report of the JPC on the PDP Bill, 2019, as well as the draft Data Protection Bill 2021, in the parliament.
- August 2022: On August 3 this year, MeitY withdrew the 2021 Bill, stating that a more “comprehensive legal framework” will be presented soon.
DPDP Bill, 2022 is based on seven principles
According to an explanatory note for the bill, it is based on seven principles-
- Lawful use: The first is that “usage of personal data by organisations must be done in a manner that is lawful, fair to the individuals concerned and transparent to individuals.”
- Purposeful dissemination: The second principle states that personal data must only be used for the purposes for which it was collected.
- Data minimisation: Bare minimum and only necessary data should be collected to fulfill a purpose.
- Data accuracy: At the point of collection. There should not be any duplication.
- Duration of storage: The fifth principle talks of how personal data that is collected cannot be “stored perpetually by default,” and storage should be limited to a fixed duration.
- Authorized collection and processing: There should be reasonable safeguards to ensure there is “no unauthorised collection or processing of personal data.”
- Accountability of users: The person who decides the purpose and means of the processing of personal data should be accountable for such processing.
Key features of the bill
(1) Data Principal and Data Fiduciary
- The bill uses the term “Data Principal” to denote the individual whose data is being collected.
- The term “Data Fiduciary” the entity (can be an individual, company, firm, state etc.), which decides the “purpose and means of the processing of an individual’s personal data.”
- The law also makes a recognition that in the case of children –defined as all users under the age of 18— their parents or lawful guardians will be considered their ‘Data Principals.’
(2) Defining personal data and its processing
- Under the law, personal data is “any data by which or in relation to which an individual can be identified.”
- Processing means “the entire cycle of operations that can be carried out in respect of personal data.”
- So right from collection to storage of data would come under processing of data as per the bill.
(3) Individual’s informed consent
- The bill also makes it clear that individual needs to give consent before their data is processed.
- Every individual should know what items of personal data a Data Fiduciary wants to collect and the purpose of such collection and further processing.
- Individuals also have the right to withdraw consent from a Data Fiduciary.
- The bill also gives consumers the right to file a complaint against a ‘Data Fiduciary’ with the Data Protection Board in case they do not get a satisfactory response from the company.
(4) Language of information
- The bill also ensures that individuals should be able to “access basic information” in languages specified in the eighth schedule of the Indian Constitution.
- Further, the notice of data collection needs to be in clear and easy-to-understand language.
(5) Significant Data Fiduciaries
- The bill also talks of ‘Significant Data Fiduciaries, who deal with a high volume of personal data.
- The Central government will define who is designated under this category based on a number of factors ranging from the volume of personal data processed to the risk of harm to the potential impact on the sovereignty and integrity of India.
(6) Data protection officer & Data auditor
- Such entities will have to appoint a ‘Data protection officer’ who will represent them.
- They will be the point of contact for grievance redressal.
- They will also have to appoint an independent Data auditor who shall evaluate their compliance with the act.
(7) Right to erase data, right to nominate
- Data principals will have the right to demand the erasure and correction of data collected by the data fiduciary.
- They will also have the right to nominate an individual who will exercise these rights in the event of death or incapacity of the data principal.
(8) Cross-border data transfer
- The bill also allows for cross-border storage and transfer of data to “certain notified countries and territories.”
- However an assessment of relevant factors by the Central Government would precede such a notification.
(9) Financial penalties
- The draft also proposes to impose significant penalties on businesses that undergo data breaches or fail to notify users when breaches happen.
- Entities that fail to take “reasonable security safeguards” to prevent personal data breaches will be fined as high as Rs 250 crore.
- As per the draft, the Data Protection Board — a new regulatory body to be set up by the government — can impose a penalty of up to ₹500 crore if non-compliance by a person is found to be significant.
What distinguishes this bill from its earlier versions?
- Gender neutrality: Significantly, and for the first time in the country’s legislative history, the terms ‘her’ and ‘she’ have been used irrespective of an individual’s gender. This, as per the draft, is in line with the government’s philosophy of empowering women.
- Imbibes best global practices: To prepare it, best global practices were considered, including review of data protection legislations of Australia, European Union (EU), Singapore, and a prospective one of the USA.
- Comprehensiveness: The draft has outlined six ‘Chapters’ and a total of twenty-five points. The ‘Chapters’ are: ‘Preliminary,’ ‘Obligations of Data Fiduciary,’ ‘Rights and Duties of Data Principal,’ ‘Special Provisions,’ ‘Compliance Framework,’ and ‘Miscellaneous.’
- Special emphasis for child protection: If personal data is likely to cause harm to a child, its processing will not be allowed.
Hits of the bills
- Widening the scope of data: Narrowing the scope of the data protection regime to personal data protection is a welcome move, as it resonates with the concerns of various stakeholders.
- Harnessing economic potential: Now non-personal data could be used to unlock social and economic value to benefit citizens, businesses, and communities in India with appropriate safeguards in place.
- Doing away with aggressive push for Data localisation: Relaxing data localisation provisions to notify countries to which data can flow, could aid India in unlocking the comparative advantage of accessing innovative technological solutions from across the globe, which in turn helps domestic companies.
- Free flow of data: In addition, the free flow of data will help startups access cost-effective technology and storage solutions, as our research shows.
- Allowing data transfers: This will also ensure that India is not isolated from the global value chain, helping businesses stay resilient in production and supply chain management and fostering overseas collaboration.
Some criticisms of the bill
- Wordplay: There had been use of open-ended language such as “as necessary” or “as may be prescribed”.
- Govt monopoly: The Bill did not seem to work towards protecting people, but ensures that the government retains all power without any checks or balances.
- Exemption provisions: The government has been given the power to exempt not only government agencies but any entity that is collecting user data, from having to comply with the provisions of this bill when it is signed into law.
- No protection against data breach: The Executive in India has a track record of exploiting to expand its powers. There is no right for compensation to individuals in case of a data breach. They have no right to data portability.
Conclusion
- Crafting such crucial legislation is no mean task. It may require some more trial and error to succeed.
- Definitely, it will involve some time and deliberation to arrive at a comprehensive legal framework.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
DPDP Bill 2022: Need for Sector-Specific Safeguards
From UPSC perspective, the following things are important :
Prelims level: DPDP Bill 2022
Mains level: DPDP Bill 2022, Data Privacy and Protection
Central Idea
- India’s digital economy is growing rapidly and generating massive amounts of personal data. As citizens embrace convenience, understanding how this data is handled and protected has become critical. The Digital Personal Data Protection (DPDP) Bill 2022 aims to safeguard citizens’ information from misuse and unauthorised access but lacks specificity in certain clauses such as the interaction with sectoral data protection regulations.
The Digital Personal Data Protection (DPDP) Bill 2022
- The Digital Personal Data Protection (DPDP) Bill 2022 is a proposed legislation aimed at safeguarding the personal data of Indian citizens from misuse and unauthorized access.
- The bill aims to regulate the handling of personal data in the rapidly growing digital economy of India.
Seven principles of DPDP Bill, 2022
According to an explanatory note for the bill, it is based on seven principles-
- Lawful use: The first is that usage of personal data by organisations must be done in a manner that is lawful, fair to the individuals concerned and transparent to individuals.
- Purposeful dissemination: The second principle states that personal data must only be used for the purposes for which it was collected.
- Data minimisation: Bare minimum and only necessary data should be collected to fulfill a purpose.
- Data accuracy: At the point of collection. There should not be any duplication.
- Duration of storage: The fifth principle talks of how personal data that is collected cannot be stored perpetually by default, and storage should be limited to a fixed duration.
- Authorized collection and processing: There should be reasonable safeguards to ensure there is no unauthorised collection or processing of personal data.
- Accountability of users: The person who decides the purpose and means of the processing of personal data should be accountable for such processing
Challenges regarding conflicting sectoral regulations in India
- The DPDP Bill 2022 lacks specificity in certain clauses regarding the interaction with sectoral data protection regulations.
- While the Bill allows for filling regulatory gaps, conflicting sectoral regulations may create confusion.
- India already has sectoral regulations regarding data protection, such as the Reserve Bank of India’s directive on storage of payment data and the National Health Authority’s Health Data Management Policy. Any deviation from existing regulations will further require the industry to readjust their operations again at considerable cost.
Approach to regulate privacy and protect data
- The two major approaches to regulating privacy and protecting data is comprehensive legislation and sector-specific regulations
- The European Union’s General Data Protection Regulation (GDPR) as an example of comprehensive legislation with sector-specific provisions
- The American sectoral approach as a patchwork of regulations tailored to specific industries, with flaws in inconsistent protection, enforcement, and lack of federal regulation
Way ahead: Finding the right balance for India
- There is a need for greater clarity and specificity in the interaction between the DPDP Bill and sectoral regulations in India
- It is important to build on existing sectoral regulations to avoid undermining their efforts and require further costly adjustments
- The role of sectoral experts in ensuring a safer, more secure, and dynamic digital landscape for Indian citizens in the future is important.
Conclusion
- The DPDP Bill must serve as the minimum layer of protection, with sectoral regulators having the ability to build on these protections for a safer and more secure digital landscape.
Are you an IAS Worthy Aspirant? Get a reality check with the All India Smash UPSC Scholarship Test
Get upto 100% Scholarship | 900 Registration till now | Only 100 Slots Left
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
What is the ‘Right to be Forgotten’?
From UPSC perspective, the following things are important :
Prelims level: Article 21
Mains level: Right to be forgotten

A doctor has requested the Delhi High Court to enforce his ‘Right to Be Forgotten,’ which includes removing news articles and other content related to his “wrongful arrest.”
What is the “Right to Be Forgotten” Law?
- The “Right to Be Forgotten” law is a legal concept that allows individuals to request the removal of their personal information from the internet.
- It is based on the idea that individuals have a right to privacy and control over their personal data.
- The law has been implemented in various forms in different countries, including the European Union, Argentina, and South Korea.
What are the origins of this Right?
- The Right to be Forgotten was first established by the European Court of Justice in 2014 in the case of “Google Spain SL, Google Inc v Agencia Española de Protección de Datos, Mario Costeja González”.
- The case was about a Spanish man who wanted to remove a 1998 advertisement about his home being repossessed.
- The Right to be Forgotten was later included in the EU’s General Data Protection Regulation (GDPR), along with the right to erasure.
- Article 17 of the GDPR outlines the right to erasure and provides certain conditions when the right can be restricted.
How does it work?
- The “Right to Be Forgotten” law allows individuals to request the removal of their personal information from search engine results, social media platforms, and other websites.
- The request must be made to the data controller, who is responsible for managing the personal data.
- The data controller then evaluates the request and decides whether to remove the information or not.
- If the request is denied, the individual can appeal the decision to the relevant regulatory authority.
Criticisms of the law
- Critics argue that the law undermines freedom of expression and the public’s right to access information.
- They also claim that the law is difficult to enforce and can lead to the censorship of legitimate information.
- Others argue that the law is too narrow in scope and does not provide adequate protection for individuals’ privacy.
Future of the law
- The “Right to Be Forgotten” law is still a relatively new legal concept, and its future is uncertain.
- It is likely that the law will continue to evolve as courts and regulators grapple with its complexities.
- In the meantime, individuals should be aware of their rights and take steps to protect their personal data online.
What is the law on the Right to be Forgotten?
- Section 43A of the IT Act, 2000 says that organizations who possess sensitive personal data and fail to maintain appropriate security to safeguard such data, resulting in wrongful loss or wrongful gain to anyone, may be obligated to pay damages to the affected person.
- IT Rules, 2021 do not include this right, they do however, lay down the procedure for filing complaints with the designated Grievance Officer so as to have content exposing personal information about a complainant removed from the internet.
Judicial precursor to the issue
- The Right to be Forgotten is not explicitly recognized by Indian law, but it has been considered part of an individual’s Right to Privacy under Article 21 by Indian courts since the 2017 ruling in “K.S.Puttaswamy vs Union of India“.
- The court acknowledged that this right may be restricted by the right to freedom of expression and information or legal obligations.
- In 2021, the Delhi High Court directed online platforms to remove publicly available records of a case against an American citizen under the Narcotics Drugs and Psychotropic Substances Act, 1985, who argued that it was affecting his employment prospects.
Attempt UPSC 2024 Smash Scholarship Test | FLAT* 100% OFF on UPSC Foundation & Mentorship programs
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Children have a Right to protect their Genetic Information from DNA tests: SC
From UPSC perspective, the following things are important :
Prelims level: Right to Privacy
Mains level: Read the attached story

Central idea: The Supreme Court of India has ruled that children have the right to protect their genetic information from being revealed in DNA tests without their consent.
Right to protect Genetic Information
- The right to protect genetic information is a fundamental right that recognizes an individual’s autonomy and control over their own personal and intimate genetic data.
- It allows individuals to make informed decisions about their health, privacy, and identity.
- In India, the Supreme Court has also held that children have the right to protect their genetic information from DNA testing in divorce proceedings, as it is part of their fundamental right to privacy.
- This is guaranteed under Article 21 of Indian Constitution.
- This right is recognized under various international human rights instruments, including the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights.
Key takeaways from the Judgment
- The court ruled that-
- Genetic information is personal and intimate
- Children have the right to privacy and bodily integrity
- Children are not to be regarded like material objects and should not become the focal point of the battle between spouses
- Allowing DNA tests would also harm the reputation and dignity of the mother
Basis of this judgment
- The court drew attention to the rights of privacy, autonomy and identity recognised under the United Nations’ Convention on the Rights of the Child.
- It acknowledged the control that individuals, including children, have over their own personal boundaries and the means by which they define who they are in relation to other people.
- Children are not to be deprived of this entitlement to influence and understand their sense of self simply by virtue of being children.
How can one get the tests done?
- Family courts should direct for a DNA test only in expedient situations and in the interest of justice, as a last resort, said the judgment.
- This should be practised as the option of last resort.
Attempt UPSC 2024 Smash Scholarship Test | FLAT* 100% OFF on UPSC Foundation & Mentorship programs
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Digital Personal Data Protection Bill: Need A Pre-legislative Consultation
From UPSC perspective, the following things are important :
Prelims level: NA
Mains level: Digital Personal Data Protection Bill and the concerns
Central Idea
- The Ministry of Electronics and Information Technology has drafted a Digital Personal Data Protection (DPDP) Bill. A data protection law must safeguard and balance peoples’ right to privacy and their right to information, which are fundamental rights flowing from the Constitution. Unfortunately, this Bill fails on both counts.
Crack Prelims 2023! Talk to our Rankers
Why do we need data protection?
- Increasing internet use: India currently has over 750 million Internet users, with the number only expected to increase in the future.
- Data breaches: At the same time, India has among the highest data breaches in the world. Without a data protection law in place, the data of millions of Indians continue to be at risk of being exploited, sold, and misused without their consent.
- Individual privacy: Data monetization may happen at cost of individual privacy. The most sought-after datasets are those that contain sensitive personal data of individuals, ex. medical history, and financial data.
- Lack of writ proceedings against corporate action: Unlike state action, corporate action or misconduct is not subject to writ proceedings in India. This is because fundamental rights are, by and large, not enforceable against private non-state entities. This leaves individuals with limited remedies against private.
DPDP Bill, 2022 is based on seven principles
According to an explanatory note for the bill, it is based on seven principles-
- Lawful use: The first is that “usage of personal data by organisations must be done in a manner that is lawful, fair to the individuals concerned and transparent to individuals.”
- Purposeful dissemination: The second principle states that personal data must only be used for the purposes for which it was collected.
- Data minimisation: Bare minimum and only necessary data should be collected to fulfill a purpose.
- Data accuracy: At the point of collection. There should not be any duplication.
- Duration of storage: The fifth principle talks of how personal data that is collected cannot be “stored perpetually by default,” and storage should be limited to a fixed duration.
- Authorized collection and processing: There should be reasonable safeguards to ensure there is “no unauthorised collection or processing of personal data.”
- Accountability of users: The person who decides the purpose and means of the processing of personal data should be accountable for such processing.
Why the Bill must be put through a process of rigorous pre-legislative consultation?
- Dilutes the provisions of the Right to Information (RTI) Act: The Bill seeks to dilute the provisions of the Right to Information (RTI) Act, which has empowered citizens to access information and hold governments accountable. It is behind the cloak of secrecy that the rights of individuals are most frequently abrogated, and corruption thrives.
- Fails to safeguard right to privacy: Proposed Bill creates wide discretionary powers for the Central government and thus fails to safeguard people’s right to privacy.
- For instance: Under Section 18, it empowers the Central government to exempt any government, or even private sector entities, from the provisions of the Bill by merely issuing a notification.
- The Bill does not ensure autonomy of the Data Protection Board: Given that the government is the biggest data repository, it was imperative that the oversight body set up under the law be adequately independent to act on violations of the law by government entities. The Bill does not ensure autonomy of the Data Protection Board, the institution responsible for enforcement of provisions of the law.
- Government direct control over the Data Protection Board: The Central government is empowered to determine the strength and composition of the Board and the process of selection and removal of its chairperson and other members.
- Serious apprehensions of its misuse by the executive: The Central government is also empowered to assign the Board any functions under the provisions of this Act or under any other law.
- Going digital by design fails to those who do not have meaningful access: The Bill stipulates that the Data Protection Board shall be ‘digital by design’, including receipt and disposal of complaints. As per the latest National Family Health Survey, only 33% of women in India have ever used the Internet. The DPDP Bill, therefore, effectively fails millions of people who do not have meaningful access to the Internet.
Conclusion
- The government has been given the power to exempt not only government agencies but any entity that is collecting user data, from having to comply with the provisions of this bill when it is signed into law.
Mains question
Q. It is behind the cloak of secrecy that the rights of individuals are most frequently abrogated, and corruption thrives. Discuss.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Data protection bill in new Avatar: protecting privacy rights
From UPSC perspective, the following things are important :
Prelims level: NA
Mains level: Important aspects of the Data protection bill
Context
- On November 18th Government released the fourth iteration of the data privacy legislation: The Digital Personal Data Protection Bill, 2022 (Bill).
Click and get your FREE Copy of CURRENT AFFAIRS Micro Notes
Background: Evolution of Demand for the data protection
- The journey towards data protection legislation began in 2011 when the department of Personnel and Training initiated discussions on the Right to Privacy Bill, 2011.
- The major fillip to the data protection case was given by the K. Puttuswamy judgment, 2017 where the supreme court held the “Right to privacy” as a fundamental right under Article 21- right to life and personal liberty.
- After the Puttaswamy judgment, the government-appointed B.N Srikrishna committee the drafting of a law for data protection and privacy. This led to the Justice B.N. Srikrishna committee report which later on led to the Personal Data Protection Bill of 2019.
Two major stakeholders of the Legislation Data principles and data Fiduciary
- Data Principle: Data principles refers to the subject whose data is being processed. While the Bill lists the “duties” of the Data Principals, these have no bearing on the realisation of the rights provided by the Bill.
- Data Fiduciary: It is an entity that processes this data. The drafters of the Bill seem to be affirming that the Data Fiduciary is responsible for safeguarding the interests of Data Principals.
- What is Data Fiduciary: The use of the term, “fiduciary” whilst referring to a data processor is significant. In different spheres of the law, when one party owes a “fiduciary” duty towards another a trustee, beneficiary, guardian or ward, the relationship between the two is guided by trust, assurance and good faith.
- Obligations of data fiduciaries towards data principles: In line with this philosophy, the rest of the Bill describes the obligations of the Data Fiduciaries towards Data Principals, the rights and duties of the latter and the regulatory framework through which data will be processed.
Two noteworthy aspects of the Bill
- Bill outlined the category of Data fiduciaries: In addition to the general obligations to prevent the misuse of the personal data of individuals, the Bill has outlined a category of Significant Data Fiduciaries, entities that are required to comply with additional measures to safeguard the personal data of individuals.
- Why is this distinction being necessary: This distinction is essential as only companies that process vast amounts of data or have a potential impact on the country’s sovereignty and integrity need to take such stringent measures. Such measures reduce the compliance cost of companies that are at a nascent stage.
- Relaxing Data localisation norms: Onerous provisions on “data localisation” in the previous versions of the Bill, which mandated companies to store user data only within India, have been omitted.
- How this move will maintain balance: The reworked Bill permits the government to notify countries to which data transfers may be permitted. This is a major respite for several tech companies, who have long talked about the infeasibility of the data localisation provisions. A balance has now been struck between the legitimate concerns of businesses and the protection of personal data of individuals.
Where else does this bill need attention?
- Focus remains only on the nature and gravity of the violation: While the Bill is, by and large, comprehensive. Section 25 and Schedule I, that deal with penalties, require elaboration. Section 25 refers to the quantum of financial penalty that must be imposed on a person guilty of non-compliance in matters related to detail. The focus remains only on the nature and gravity of the violation. The proposed legislation does not consider the financial ranking of a company before imposing penalties.
- The bill must take financial ranking of the company in consideration: The Bill must ensure that the penalties imposed are proportionate to the size and operations of a company, to be effective, fines must not drive companies into economic loss.
- For instance: A leaf can be taken from the European Union’s General Data Protection Regulation (GDPR), amongst other similar regulations, which levies penalties in accordance with the total turnover of companies.
What makes this bill distinct and comprehensive?
- Promoting cooperation: The Bill safeguards individual data, whilst also promoting cooperation between data fiduciaries and the government.
- As per the India’s requirements: While it draws upon the best practices of foreign jurisdictions, such as Europe and Australia, it has been drafted in a manner that is tailor-made to India’s requirements.
- Exemptions are restrictive: Even the exemptions granted to the Centre are extremely restrictive and in sync with past judicial precedents and Article 19(2) of the Constitution.
- Significant shift in drafting legislation: The Bill marks a significant shift in the manner of drafting legislation. Historically, comprehending a piece of legislation in India has usually been akin to the membership of an exclusive club only legal practitioners, policy professionals and a handful of politicians are able to understand and interpret laws.
- Ensures simplification and accessibility to ordinary citizens: This Bill marks a transition from legalese to legal simplification, it realises that it is in our best interests to ensure that all laws especially legislation that have a significant impact on citizens are made accessible to all individuals irrespective of their professional or educational standing.
Conclusion
- The Bill safeguards individual data, whilst also promoting cooperation between data fiduciaries and the government. While it draws upon the best practices of foreign jurisdictions, it has been drafted in a manner that is tailor-made to India’s requirements. Exemptions granted to the Centre are extremely restrictive.
Mains Question
Q. What are the salient aspects of the Digital Personal Data Protection Bill? Discuss what makes it unique and inclusive.
(Click) FREE1-to-1 on-call Mentorship by IAS-IPS officers | Discuss doubts, strategy, sources, and more
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
End-to-end Encryption and related issues
From UPSC perspective, the following things are important :
Prelims level: End-to-end Encryption
Mains level: Read the attached story

Apple recently announced that it will be increasing the number of data points protected by end-to-end encryption on iCloud.
What is end-to-end encryption?

- End-to-end encryption is a communication process that encrypts data being shared between two devices.
- It prevents third parties like cloud service providers, internet service providers (ISPs) and cybercriminals from accessing data while it is being transferred.
- The process of end-to-end encryption uses an algorithm that transforms standard text into an unreadable format.
- This format can only be unscrambled and read by those with the decryption keys, which are only stored on endpoints and not with any third parties including companies providing the service.
- This encryption has long been used when transferring business documents, financial details, legal proceedings, and personal conversations.
- It can also be used to control users’ authorisation when accessing stored data, which seems to be what Apple intends to do.
Where is it used?
- End-to-end encryption is used to secure communications.
- Some of the popular instant-messaging apps that use it are Signal, WhatsApp, iMessage, and Google messages.
- However, instant messaging is not the only place where user data is protected using end-to-end encryption.
- It is also used to secure passwords, protect stored data and safeguard data on cloud storage.
Why are tech companies using it?
- Preventing data breach: Tech companies often cite data breach issue.
- Extra protection: Encryption puts extra layer of protection that would protect valuable digital information against hacking attacks.
- Prevent snooping: It is also seen as a technology that secures users’ data from snooping by government agencies, making it a sought-after feature by activists, journalists, and political opponents.
- Capital generation: It showcases any company’s position as a provider of secure data storage and transfer services.
What does it mean for users?
- End-to-end encryption ensures that user data is protected from unwarranted parties including service providers, cloud storage providers, and companies that handle encrypted data.
- Encrypted data can only be decrypted by trusted devices.
- No one else can access this data and it remains secure even in the case of a data breach in the cloud storage.
Why are government agencies unhappy with it?
- The FBI in a statement expressed displeasure at the idea of increasing use of end-to-end encryption by technology companies.
- It said that while it remains a strong advocate of encryption schemes that give “lawful access by design”, that would enable tech companies “served with a legal order” to decrypt data.
- Attempts by government agencies across the globe, in the past, to access encrypted data hosted and stored by tech companies have met with strong resistance.
- Law enforcement agencies seeks to weaken encryption with backdoors.
- Thus is considered ill-advised and could compromise the reliability of the internet.
Click and get your FREE Copy of CURRENT AFFAIRS Micro Notes
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Draft Digital Personal Data Protection Bill, 2022
From UPSC perspective, the following things are important :
Prelims level: Digital Personal Data Protection (DPDP) Bill, 2022
Mains level: Data surveillance and the concerns over the Digital Personal Data Protection (DPDP) Bill, 2022
Context
- Ministry of Electronics and Information Technology released the Digital Personal data Protection Bill, 2022, on November 18.
Click and get your FREE Copy of CURRENT AFFAIRS Micro Notes
Background: Demand for the data surveillance reforms
- The journey towards a data protection legislation began in 2011 when the department of Personnel and Training initiated discussions on the Right to Privacy Bill, 2011.
- As per an Office Memorandum dated September 29, 2011, the then attorney General, Goolam Vahanvati, opined that conditions under which the government can carry out “interception of communication” should be spelt out in the Bill.
- The report of the group emphasized the need to examine the impact of the increased collection of citizen information by the government on the right to privacy. Since then, civil society organizations, lawyers and politicians have consistently demanded surveillance reform, highlighting how personal data can only be protected when the government’s power to conduct surveillance of citizens is meaningfully regulated.
Revoked version of Digital Personal data Protection Bill, 2022
- Eases cross-border data flows but wide-ranging powers to state agencies: The reworked version of the data protection Bill, released three months after the Govt withdrew an earlier draft, eases cross-border data flows and increases penalties for breaches. But it gives the Centre wide-ranging powers and prescribes very few safeguards.
- Delicate balance on privacy and restrictions: Officials at the Ministry of Electronics and IT (MeitY) have said the new draft strikes a delicate balance and factors in learning from global approaches, while staying aligned to the Supreme Court’s ruling on privacy as a fundamental right, but within reasonable restrictions.
- Seven principles of the Bill: The explanatory note accompanying the Bill elaborates on the seven principles it seeks to promote, including transparency, purpose limitation, data minimization, and preventing the unauthorized collection of personal data.
The surveillance architecture In India
- Main components: The surveillance architecture in India comprises mainly of Section 5(2) of the Indian Telegraph Act, 1885; Section 69 of the Information Technology Act, 2000; and the procedural rules promulgated under them.
- No clearly defined ground: No But this architecture does not meaningfully define the grounds under which, or the manner in which, surveillance may be conducted.
- No safeguards: It also does not contain safeguards such as ex-ante or ex-post facto independent review of interception directions.
- Lack of accountability: The concentration of power with the executive thus creates a lack of accountability and enables abuse. Evidence for this emerges not only from instances of political surveillance, but also from the slivers of transparency that accidentally emerge from telecom companies.
- Excessive surveillance: For instance, submissions by Airtel to the Telecommunications Department, as part of the public consultation process for the Indian Telecommunication Bill, reveal that excessive data collection requests are already a reality. Airtel has asked the government to share the costs it incurs to comply with the increasing demands from law enforcement agencies to carry out surveillance.
- Concerns over citizen data processing: Apart from outright surveillance, unfettered collection and processing of citizen data for other purposes, such as digital governance, raise concerns.
What are the concerns over the revoked version of the bill?
- No proposals for surveillance reform: All iterations of the data protection legislation since the draft Personal Data Protection Bill, 2019, the draft Data Protection Bill, 2021 and the 2022 Bill have no proposals for surveillance reform.
- Data processing without consent: Personal data can be processed even without the person’s consent. Blanket exemptions Like previous iterations, Clause 18(2) of the 2022 Bill allows the Union government to provide blanket exemptions for selected government agencies.
- Permits exemption to private entities: However, this Bill is more egregious than previous iterations as it permits exemption to private sector entities that may include individual companies or a class of them, by assessing the volume and nature of personal data under Clause 18(3).
- Exemptions without the purview of data protection: Under the new Bill in India, exempted state agencies and private entities will not be within the purview of the Data Protection Board, the body responsible for imposing penalties in case fiduciaries infringe privacy.
Data processing in other countries
- Exemptions on case by case and the rationale behind it: While the existing or proposed legislations in the European Union and in the U.S. permit security agencies to claim exemptions on a case-by-case basis, depending on why they are collecting personal data, they do not contain blanket exemption powers to an entire government entity.
- Meaningful state surveillance: Other jurisdictions exercise meaningful oversight over state surveillance. For instance, the Investigatory Powers Tribunal in the U.K. is authorized to hear complaints against misuse of surveillance powers and can impose monetary penalties in case of a breach.
Conclusion
- The preamble to the 2022 Bill states that the purpose is to protect the personal data of individuals and to ensure that personal data is processed only for lawful purposes. However, blanket exemptions for state agencies alongside private entities raise untold concerns, which need to be addressed on a war footing.
Mains question
Q. What do you understand by data surveillance? It is said the Data surveillance architecture in India lacks accountability and transparency. Analyze.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Right to Privacy in an era of social media
From UPSC perspective, the following things are important :
Prelims level: Articles 21
Mains level: issues over the Right to Privacy, Social media and privacy
Context
- The recent outrage over the unauthorized video of cricketing superstar Virat Kohli’s hotel room in Perth including glimpses of his private spaces and objects is best viewed through an understanding of the changed landscape of the “private” and the “public” in our times. It is a topography shaped through our engagements with social media of different kinds.
What does the Constitution say?
- Fundamental right under Article.21: Article 21 is also known as the heart of the constitution; this right is granted to citizens of India as well as the non-citizens. This fundamental right not only talks about life and liberty but it also covers wide variety of rights.
- Interpretation of Maneka Gandhi v. Union of India and Anr (1978): The interpretation of the term Personal Liberty has been discussed in many cases and finally had a wider interpretation in the case of Maneka Gandhi v. Union of India and Anr (1978) here the Delhi Regional officer ordered the petitioner Maneka Gandhi to surrender her passport within 7 days without giving her proper reason for the same.
- Supreme court on Personal liberty: The Supreme Court held that ‘Personal Liberty’ covered variety of rights and that such right could only be taken away according to the procedure established by law which had to be just, fair and reasonable and not arbitrary in nature. Personal liberty means various rights that provide for personal liberty of a person.
- Right to privacy: In Article 21 the term Right to Life includes right to participate in activities, right to tradition, heritage, culture, livelihood and so on. One of the most important right to live also includes Right to Privacy. Each and every human being would want some privacy in their life. No one would want others to intrude in their private space and disturb the happiness and peace.
What is the Fight for right to Privacy?
- Not in the original constitution: This right of privacy was not granted to the citizens for a long time and there had been a lot of debate going on about the same, there is no explicit provision in the constitution which emphasizes about the right to privacy.
- Data is fundamental to the privacy: Even the data we save in our mobile phones and laptops are also our private data which needs to be protected, if the data is stolen our right to privacy is lost and fundamental right is infringed. Unprotected data causes a disturbance in the right to privacy.
Some of the Important cases related to right to privacy
- Kharak Singh V. The State of U.P.(1962): The discussion about the right to privacy first came up in the case of Kharak Singh V. The State of U.P.(1962) Kharak Singh’s house was visited by the police at strange hours, frequently waking him up from his sleep, it was held by the court that this infringed his ‘right to life’ but however court dismissed the petitioner’s allegation that the shadowing of chronic criminals infringed on his right to privacy as at that time the right to privacy was not recognised as the Fundamental Right.
- Rajagopal v. State of Tamil Nadu (1994): With the case of R. Rajagopal v. State of Tamil Nadu (1994) where this case prepared the way for subsequent decisions on the Right to Privacy, paving the way for it to be included in the Fundamental Rights given under Part III of the Constitution.
- X v. Hospital Z case (1998): There are reasonable restrictions for this right about which it was held by the Supreme Court in the case of Mr. X v. Hospital Z (1998) here the appellant Mr. X was tested positive for HIV about which the doctors informed someone else without his consent because of which marriage of Mr. X was called off, the appellant approached the court stating that his right to privacy was violated. The court here held that this fact has to been known to the person whom he marries as this fact would affect her life as well as it being a communicable disease and that there is no violation to the ‘Right of Privacy’ of Mr. X.
The landmark case of K.S. Puttaswamy v/s Union Of India 2017.
- Right to privacy is fundamental right: In the landmark case K.S. Puttaswamy V. Union of India which was passed in the year 2017, Right to Privacy was recognised as Fundamental Right and was then enshrined in Article 21 as a Right to life and personal liberty.
- Social media endangered the privacy: Judges held that because there is enormous technical advancement both state and non-state factors may be at risk of loss of privacy, also it was held that an Individual is very concerned with his / her personal Data, they control their data and what to be posted on social media what to be displayed to the public and what to hide from outsiders, so unauthorized use of such information by anyone else except to whom that information belongs to may lead to violation of individuals privacy.
- Privacy is integral to fundamental rights: On 24th August 2017 the nine-judge bench of India passed a unanimous historic Judgement with concurring opinions. Part III of the Indian constitution lays down different articles for the protection of one’s Fundamental Rights. The judgement stated privacy to be an integral component of Part III.
- Overturning the previous judgements: The bench recognized that the right to privacy should also be a key element of Fundamental Rights and should be included in Article 21 of right to life and personal liberty. In this judgement the decisions given in the case of Kharak Singh V. The State of U.P. (1962) and MP Sharma V. Satish Chandra (1954) were overruled.
Conclusion
- The great deal of hand wringing over the invasion of Virat Kohli’s privacy has been accompanied by seemingly endless circulation of the video clip. The line between outrage and enjoyment is as unclear as that between the alternating desire for publicity that ethereal frisson of celebrity-ness and revulsion over too much of it.
Mains Question
Q. How right to privacy is integral part of right to life? How social media affected the privacy of individual and enlist the solutions associated with it.
Click and Get your FREE copy of Current Affairs Micro notes
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
TN bans online ‘Games of chance’ and Gambling
From UPSC perspective, the following things are important :
Prelims level: Game of chance
Mains level: Online gaming and related issues
Online gambling and online games of chance have been banned in Tamil Nadu. At the same time, the other online games will be regulated.
What is Online Gaming?
- Online games refer to games that are played over some form of computer network, most often the Internet.
Types of gaming
- The types of online gaming include:
- E-sports (well-organized electronic sports which include professional players) ex. Chess
- Fantasy sports (choosing real-life sports players and winning points based on players’ performance) ex. MPL cricket
- Skill-based (mental skill) ex. Archery
- Gamble (based on random activity) ex. Playing Cards, Rummy
Online gaming sector in India
- In the past few years, India’s nascent online gaming industry witnessed an unprecedented rise, catapulting it to the top five mobile gaming markets in the world.
- Registering a growth rate of 38%, online gaming is the next sunrise industry.
- Currently, there are more than 400 gaming companies in India, and it is home to 420 million online gamers, second only to China, according to an analysis by KPMG.
Why is the gaming industry booming in India?
- Digital India boom in the gaming industry
- Narrowing of the digital divide
- IT boom
Other factors promoting the boom
- Growing younger population
- Higher disposable income
- Inexpensive internet data
- Introduction of new gaming genres, and
- Increasing number of smartphone and tablet users
Prospects of online gaming
- State List Subject: The state legislators are, vide Entry No. 34 of List II (State List) of the Seventh Schedule, given exclusive power to make laws relating to betting and gambling.
- Distinction in laws: Most Indian states regulate gaming on the basis of a distinction in law between ‘games of skill’ and ‘games of chance’.
- Classification on dominant element: As such, a ‘dominant element’ test is utilized to determine whether chance or skill is the dominating element in determining the result of the game.
- Linked economic activity: Staking money or property on the outcome of a ‘game of chance’ is prohibited and subjects the guilty parties to criminal sanctions.
- ‘Game of Skill’ debate: Placing any stakes on the outcome of a ‘game of skill’ is not illegal per se and may be permissible. It is important to note that the Supreme Court recognized that no game is purely a ‘game of skill’ and almost all games have an element of chance.
Need for regulation
- No comprehensive regulation: India currently has no comprehensive legislation with regards to the legality of online gaming or boundaries that specify applicable tax rates within the betting and gambling industry.
- Ambiguity of the sector: The gaming sector is nascent and is still evolving, and many states are bringing about legislation seeking to bring about some order in the online gaming sector.
- State list subject: Online gaming in India is allowed in most parts of the country. However, different states have their own legislation with regards to whether online gaming is permitted.
- Economic advantage: Well-regulated online gaming has its own advantages, such as economic growth and employment benefits.
Issues with online gaming
- Gaming addiction: Numerous people are developing an addiction to online gaming. This is destroying lives and devastating families.
- Compulsive gaming: Gaming by children is affecting their performance in schools and impacting their social lives & relationships with family members. Ex. PUBG
- Impact on psychological health: Online games like PUBG and the Blue Whale Challenge were banned after incidents of violence and suicide.
- Threat to Data privacy: Inadvertent sharing of personal information can lead to cases of cheating, privacy violations, abuse, and bullying.
- Betting and gambling: Online games based on the traditional ludo, arguably the most popular online game in India, have run into controversy, and allegations of betting and gambling.
Why hasn’t a comprehensive law yet materialized?
- Earlier, states like Tamil Nadu, Telangana, Andhra Pradesh, and Karnataka also passed laws banning online games.
- However, they were quashed by state High Courts on grounds that an outright ban was unfair to games of skill:
- Violation of fundamental rights of trade and commerce, liberty and privacy, speech and expression;
- Law being manifestly arbitrary and irrational insofar as it did not distinguish between two different categories of games, i.e. games of skill and chance;
- Lack of legislative Competence of State legislatures to enact laws on online skill-based games.
Way forward
- Censoring: Minors should be allowed to proceed only with the consent of their parents — OTP verification on Aadhaar could resolve this.
- Awareness: Gaming companies should proactively educate users about potential risks and how to identify likely situations of cheating and abuse.
- Regulating mechanism: A Gaming Authority in the central government should be created.
- Accountability of the gaming company: It could be made responsible for the online gaming industry, monitoring its operations, preventing societal issues, suitably classifying games of skill or chance, overseeing consumer protection, and combatting illegality and crime.
- All-encompassing legislation: the Centre should formulate an overarching regulatory framework for online games of skill. India must move beyond skill-versus-chance debates to keep up with the global gaming industry.
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Ensuring Internal Security by Securing Communication Networks
From UPSC perspective, the following things are important :
Prelims level: NA
Mains level: Cyber security,Right to privacy,Technology
Context
- In a bid to upgrade the Indian Telegraph Act 1885, a law that is more than a century old, the Department of Telecommunications, or DoT, issued the Draft Indian Telecommunications Bill 2022 on 21 September. Among other things, the proposed legislation brings digital communications applications like Signal and Telegram under telecommunications law and regulation and treats them like internet and telecom service providers and broadcasters.
What are the Current regulations of communication networks?
- Information Technology Act 2000: Digital communication applications are currently governed by the Ministry of Electronics and Information Technology (MeitY) and the Information Technology Act 2000 where there is no licensing requirement.
- Telecom Regulatory Authority of India (TRAI): The move has been debated for some years now, with the Telecom Regulatory Authority of India (TRAI) issuing multiple consultations on the matter, most recently in 2018.
- National Digital Communications Policy in 2018: DoT may have legitimate grounds for extending its jurisdiction over digital communications applications, including a policy mandate established by the National Digital Communications Policy in 2018. However, there is a conflict that must be resolved, namely the jurisdictional overlap between the prospective law and the existing information technology framework.
Why is security of communication networks important?
- National security: Communication networks are a part of our critical information infrastructure which was defined in the IT Act, 2000 as “the computer resource, the incapacitation or destruction of which, shall have debilitating impact on national security, economy, public health or safety.”
- Protecting critical Infrastructure: Communications networks are crucial to the connectivity of other critical infrastructure, viz. civil aviation, shipping, railways, power, nuclear, oil and gas, finance, banking, communication, information technology, law enforcement, intelligence agencies, space, defence, and government networks. Therefore, threats can be both through the networks as well as to the networks.
- Ready to Information Warfare (IW): Because of the increasing relevance of information technology (IT) to people’s lives, individuals who take part in IW are not all soldiers and that anybody who understands computers may become a fighter.
- To stop the adverse impact on information system: IW is inexpensive as the targeted party can be delivered a paralysing blow through the net and it may be difficult for the latter to discern where the attack originated. Large amount of useless information can be created to block or stop the functioning of an adversary’s information system.
- For Possible mass mobilisation: Thus, a People’s War in context of IW can be carried out by hundreds of millions of people, using open-type modern information systems. Even political mobilisation for war can be achieved via the internet, by sending patriotic e-mail messages and by setting up databases for education.
Why new law is necessary?
- No obligation on communication applications: A key reason for the DoT to bring such applications under telecommunications law is national security. Licensed telecom service providers must provide law enforcement authorities access to their networks and intercept messages in the course of investigations.Conversely, there is a contention that there is no corresponding obligation on digital communications applications, potentially leaving a gap in safeguarding national security interests.
- For increased Encryption and secrecy: A further assertion is that the encryption used by most digital communications apps hampers investigative efforts as it becomes difficult to ascertain user identity on these platforms and stop malfeasance.
- Necessary to Ensure security: The draft telecom bill attempts to address this gap by including a provision which enables the government to undertake measures in the name of national security, including issuing directions regarding the use of any telecommunication service.
- Licensing for more transparency: Presumably, licences issued for digital communications applications under the proposed legislation will prescribe conditions that would require these apps to give law enforcement authorities access to their systems for monitoring and intercepting communications.
What is the criticism over the new bill?
- Existing law is sufficient: the IT Act already has provisions to enable lawful interception and monitoring of messages sent through digital communications applications. Under Section 69 of the IT Act, the central or state government may issue directions to do so in the interest of preserving, among other things, national security and public order. Moreover, rule 4 of the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) 2021 requires digital communications applications with 50 lakh users or more to enable identification of those sending messages on their platforms.
- Possible mass surveillance by Government: The implication here is that digital communications apps would have to break encryption and create meaningful pathways for the surveillance of their services. Importantly, while rule 4 has been challenged, it has not been stayed by any court, meaning digital communications apps must comply with it.
- New laws will overlap with IT Act: It would appear, then, that the provisions regarding national security in the draft telecom bill and the IT Act overlap. So how would the situation be resolved, as both have clauses that give them the ability to override provisions in other laws? Specifically, both the Draft Telecom Bill, 2022 and the IT Act have a non-obstante clause, a provision that enables a statute to uphold the enforceability of its provisions over others that contradict it. Thus, in case of a contradiction between these two laws, which would prevail?
- Introducing Digital India Act will likely to override other laws: Reports indicate that MeitY aims to introduce a newer version of the IT Act, namely the ‘Digital India Act’. This law will likely deal with matters related to lawful interception and other matters related to the governance of digital communications applications. If such a law is passed, the ‘Digital India Act’ would override the enacted version of the telecom bill.
- Judicial challenge of acknowledgment: A situation emerges where the telecom bill, if enacted, may face a judicial challenge. Based on the analysis of the court’s treatment of special laws, this proposed legislation is unlikely to prevail as the ‘Digital India Act’ will emerge after it
Conclusion
- National security and privacy of citizens an equally important. One cannot be traded for other. Arbitrary power of surveillance must be regulated by independent body under the parliament which will seek the transparency and accountability from law enforcement authorities.
Mains Question
Q.Unchecked communication networks are grave internal security threat. Comment why new law is necessary for interception and regulation of communication networks in India?
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Is Draft Telecommunications Bill, 2022 Flawless?
From UPSC perspective, the following things are important :
Prelims level: Right to Privacy
Mains level: Cyber security,Right to privacy,Technology
 Context
Context
- Keeping an eye on the telecommunication regulatory framework Supreme Court issued substantive legal reform on surveillance laws in India. Union government has published the Draft Telecommunications Bill, 2022 to replace the Telegraph Act, 1885.
Background
- Over two decades ago, allegations of surveillance against politicians led to a CBI inquiry and report against V P Singh’s government. The allegations revealed that imaginary reasons were given for ordering phone tapping without authorization.
- Last years, many publications reported that phones of several dozen Indian journalists, lawyers and human rights activists had been compromised using an invasive Israeli-developed malware called Pegasus.
 What is Draft Telecommunications Bill, 2022?
What is Draft Telecommunications Bill, 2022?
- The draft Indian Telecommunication Bill, 2022 is an attempt by the Department of Telecommunications (DoT) to consolidate various legislations presently governing the telecommunication landscape in India.
- The Bill seeks to replace three laws, the Indian Telegraph Act, 1885, the Indian Wireless Telegraphy Act, 1933 and the Telegraph Wires (Unlawful Possession) Act, 1950.
- The new regulatory framework is to bring the law at par with technological advancements and remove obsolete provisions from the colonial era laws.
What are the current laws governing communication surveillance in India?
Communication surveillance in India takes place primarily under two laws:
- Telegraph Act, 1885: It deals with interception of calls.
- Call interception:Under Section 5(2) of this law, the government can intercept calls only in certain situations.
- For sovereignty:They include the interests of the sovereignty and integrity of India, the security of the state, friendly relations with foreign states or public order, or for preventing incitement to the commission of an offense.
- Free speech restrictions:These are the same restrictions imposed on free speech under Article 19(2) of the Constitution.
- Exceptions for journalists:A provision in Section 5(2) states that even this lawful interception cannot take place against journalists.
- Information Technology Act, 2000: It was enacted to deal with surveillance of all electronic communication, following the Supreme Court’s intervention in 1996.
- Electronic surveillance:Section 69 of the IT Act and the IT (Procedure for Safeguards for Interception, Monitoring, and Decryption of Information) Rules, 2009 were enacted to further the legal framework for electronic surveillance.
- Data interception:Under the IT Act, all electronic transmission of data can be intercepted.
- Section 69 of the IT Act adds another aspect that makes it broader — interception, monitoring, and decryption of digital information “for the investigation of an offense”.
 How the loopholes in the current system breaching the Data Privacy?
How the loopholes in the current system breaching the Data Privacy?
- No comprehensive data Protection Law:
- No comprehensive data protection law leaving ambiguities over several laws.
- A comprehensive data protection law to address the gaps in existing frameworks for surveillance is yet to enact.
- Unaccountable, opaque exercise of surveillance:
- The Telegraph Act contains broad and excessive powers of interception and surveillance of communications carried out through any telegraph.
- The surveillance power is principally contained under Section 5(2), and has resulted in an unaccountable, opaque and unconstitutional exercise of surveillance that has led to accusations across the political spectrum.
- Less transparency:
- Ministry of Home Affairs refuses to disclose even aggregate data on the number of surveillance orders issued by it each year illegally gathered evidence is being sought to prosecute people.
- For instance, the Bombay High Court about three years ago noted in a case that premier investigating agencies such as the CBI have used, interception orders (that) neither have sanction of law nor issued for legitimate aim.
 Key features of the Draft Telecommunications Bill, 2022
Key features of the Draft Telecommunications Bill, 2022
- Broad Definitions:
- The Bill introduces a broad definition of ‘telecommunication services’.
- It now includes internet-based services, in-flight and maritime connectivity, interpersonal communications services, machine to machine communication services, and over-the-top (OTT) based communication services that are made available to users by telecommunication
- KYC and caller id requirements:
- The Bill requires licensed entities to ensure that they identify the persons to whom they provide telecommunication services.
- The Bill places an obligation on telecommunication service providers to do this through a ‘verifiable mode’, as prescribed by the government.
- Licensing, registration, and authorization:
- Under the Bill, four types of permissions are identified – license, registration, authorization and assignment.
- While the Bill does not differentiate between the four types of permissions, it clarifies that a license is only required for providing telecommunication services or operating telecommunication networks
- Wide ranging powers of Central Government:
- The Bill includes wide-ranging powers for the central and state governments in the event of a public emergency or in interest of public safety.
- These powers include taking temporary possession of any telecommunication services, suspension of transmission in cases of public emergency, interception/detainment/disclosure of messages, suspension of communications, or otherwise transmit certain announcements for public safety and national security purposes.
- User protection and duties: User has been declared as an important policy objective of the Government. It places a duty on users to not furnish false information, suppress material information or impersonate others when proving identity to avail telecommunication services.
- Offences and penalties: Any offence under the Bill may be punished with a fine, imprisonment, suspension of telecommunication services or a combination of the above. For companies, the employees who were responsible for the conduct or the business relating to the offence at the time the offence was committed will be punished.
- Dispute resolution mechanism: The Bill provides for the right of appeal before the appellate authority. It also creates an enabling provision for the Central Government to set up an alternate dispute resolution mechanism such as arbitration, mediation or other processes of dispute resolution
What are Concerns over the Draft Telecommunication bill, 2022?
- Regulatory overlaps:The broad of the definition of ‘telecommunication services’ include OTT communication platforms such as WhatsApp, Telegram, Signal among others, may potentially lead to regulatory or jurisdictional overlaps.
- Unchecked use of State powers:The Bill gives broad powers to the central government in prescribed situations without any accompanying checks and balances. The Bill empowers the central and state government to intercept messages in the interest of public safety and emergency without the providing clearly defined guardrails for it.
- Undefined National security: The term, national security is left undefined and does not match constitutional precedent or text which instead uses the phrase,in the interests of the security of state
- Users Less choice in the privacy and security of their digital footprint:
- Power to prescribe standards under Clause 23, which may result in regulations as recently issued by the Computer Emergency Response Team (CERT-In) that have resulted in the closure of servers or services by leading, global VPN providers such as Proton and TunnelBear.
- All of this practically means that users will have less choice in the privacy and security of their digital footprint, as these powers will lead to requirements to locally register and host data, and comply with requirements to identify users (KYC requirements).
Conclusion
- There should be some reasonable basis or some tangible evidence to initiate or seek approval for interception by State authorities. Any digression from the ethical and legal parameters set by law would be tantamount to a deliberate invasion of citizens.
Mains Question
Q. Any deviation from the moral and legal parameters set by the law would amount to a deliberate attack on citizens. In this context discuss the data privacy of citizens in the era of massive expansion of internet and mobile usage.
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Personal Data Protection Bill
From UPSC perspective, the following things are important :
Prelims level: European Union’s Digital Services Act
Mains level: Paper 2- Need for personal data protection act
Context
In a surprise development last week, the Government withdrew the Personal Data Protection (PDP) Bill, 2019, thereby abruptly halting the country’s quest for a national data protection law that had been in the works for over five years.
Reasons for withdrawal of the Bill
- The short circular issued by the Minister of Electronics and Information Technology states that considering the report of the Joint Parliamentary Committee (JPC) — it had proposed 81 amendments and made 12 recommendations — “a comprehensive legal framework is being worked on”.
- There is no elaboration on what such a “comprehensive legal framework” entails.
- Possible plan of action: The Government could enact a fresh privacy legislation or a comprehensive data protection law (covering both personal and non-personal data).
- Subsuming data protection in IT Act: Alternatively, it could subsume data protection under its ongoing attempts at revising the existing Information Technology Act, 2000.
- Digital markets law: It could also enact a digital markets law, along the lines of the European Union’s Digital Services Act, focusing on competition and innovation in the digital space.
Background of the introduction of Personal Data Protection Bill
- When the Supreme Court of India affirmed the right to privacy in K.S. Puttaswamy judgment in 2017, the nine-judge Bench of the Court referred to the Government’s Office Memorandum constituting the B.N. Srikrishna Committee to suggest a draft Data Protection Bill.
- The committee released its draft Personal Data Protection Bill in 2018, which was the first public articulation of a data protection law in India.
- When the Supreme Court upheld the constitutionality of the Aadhaar Act, the majority emphasised that it believed that “there is a need for a proper legislative mechanism for data protection”.
- In December 2019, the Government introduced the PDP Bill, 2019 in the Lok Sabha as a comprehensive personal data protection regime.
- The Bill was referred to the JPC for its recommendations.
What were the issues with the Bill?
- Power to exemption with state: The Bill’s expansive exemptions allowed the state to exempt the entire application of the law simply as if it was “expedient” to do so in the interest of national security or public order.
- Powers without accountability: The PDP Bill, 2019 as well as the JPC’s version established a strong regulator (the Data Protection Authority) with a lot of power, but very little independence or accountability.
- Data localisation: The Bill imposed a strong data localisation mandate, requiring companies to store all sensitive personal data and critical personal data (which was not defined) in India.
- Subsuming the personal and non-personal data: The JPC recommended subsuming the regulation of personal data and non-personal data within a single legislation, even though it undermined the Puttaswamy mandate to ensure protection of personal data.
Why we need data protection law?
- Increasing internet use: India currently has over 750 million Internet users, with the number only expected to increase in the future.
- The Government is also making a strong push for a ‘Digital India’, with increased focus on digitisation of access to health, ration, banking, insurance, especially after the COVID-19 pandemic.
- There is a greater focus on the inter-linking of data, whether through facial recognition, Aadhaar, or the Criminal Procedure (Identification) Act, 2022.
- Data breaches: At the same time, India has among the highest data breaches in the world.
- Without a data protection law in place, the data of millions of Indians continues to be at risk of being exploited, sold, and misused without their consent.
- Lack of writ proceeding against corporate action: Unlike state action, corporate action or misconduct is not subject to writ proceedings in India.
- This is because fundamental rights are, by and large, not enforceable against private non-state entities.
- This leaves individuals with limited remedies against private actors.
- A personal data protection legislation would remedy this lacuna by providing individuals with proper grievance redress options and creating sufficient deterrence among private actors.
Conclusion
It is imperative that the Government soon introduces a fresh data protection legislation, drawn after proper public consultation. Such a law should take into consideration the criticisms that have been raised by civil society as well as the private sector.
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Right to privacy after 5 years
From UPSC perspective, the following things are important :
Prelims level: article 21
Mains level: right to privacy
 Context
Context
- Data privacy breaches which result in the loss and theft of personal, sensitive data have not reduced in terms of measurable frequency or their impact.
- It has been 5 years since the nine-judge Supreme Court bench delivered the judgment in the Puttaswamy case. It asserted that Indians have a constitutionally protected fundamental right to privacy.
Right to Privacy can be defined as
- A right to be let alone;
- The right of a person to be free from any unwarranted publicity;
- The right to live without any unwarranted interference by the public in matters with which the public is not necessarily concerned.
 Definition of data
Definition of data
- Data is a collection of discrete values that convey information, describing quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted.
What is Data Protection?
- Data protection refers to policies and procedures seeking to minimise intrusion into the privacy of an individual caused by collection and usage of their personal data.
What is data privacy?
- Data privacy refers to controlling access to the data. Organizations must determine who has access to data. Understandably, a privacy breach can lead to data security issues.
What is data security?
- Data security refers specifically to measures taken to protect the integrity of the data itself against manipulation and malware. It provides defense from internal and external threats.
Why we need data protection?
- Increasing internet use: India currently has over 750 million Internet users, with the number only expected to increase in the future.
- Data breaches: At the same time, India has among the highest data breaches in the world. Without a data protection law in place, the data of millions of Indians continues to be at risk of being exploited, sold, and misused without their consent.
- Individual privacy: Data monetization may happen at cost of individual privacy. The most sought-after datasets are those that contain sensitive personal data of individuals, ex. medical history, financial data.

Issues with the data breaches in India
- Violation of the right to privacy: The right to privacy was recognized as a fundamental right, included under the right to life and liberty by the Supreme Court of India in 2017.
- Absence of legal framework: Without a law in place to regulate data collection and to act as an oversight mechanism, valid concerns about privacy and other rights violations continue to arise.
- High Infrastructural Costs: Technologies like Artificial Intelligence and Big Data are costly to implement. The size of stored information is extremely large and requires huge network & data storage facilities, which are currently not available in India.
- The concern of Data Leakage: In today’s world of cybercrime, it is important to put appropriate safeguards in place in order to ensure the integrity of the repository/database, so that it doesn’t leak out the information and is not privatized or monetized.
- Reliability & Authenticity: As the data collected may be used in the court of law during the course of a criminal trial, the reliability and the admissibility of the data along with standards and procedures followed would be taken into consideration. Hence, the authenticity of the data is crucial.
Conclusion
- Today, there is a relentless pace of digitisation that relies on gathering personal data in all spheres of our lives. All of this is done in a legal vacuum without any oversight or remedy. This underscores the urgent need for robust data protection law.
Mains question
Q. What do you understand by the term data privacy? Explain how data leakages threatens the sacred right to privacy?
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Issue of withdrawal of Personal Data Protection Bill
From UPSC perspective, the following things are important :
Prelims level: MEITY
Mains level: Paper 2- Need for data protection law
Context
The Minister for the Ministry of Electronics and IT withdrew the Personal Data Protection Bill, 2019. The reasons for the withdrawal were circulated in a note to MPs, which stated that,“considering the report of the JPC (Joint Parliamentary Committee), a comprehensive legal framework is being worked upon…”.
Background of Personal Data Protection Bill
- An expert committee headed by Justice (retd) A P Shah recommended in October, 2012,“a detailed framework that serves as the conceptual foundation for the Privacy Act”.
- This did not come to fruition, with proposals buried by 2014 due to objections from the intelligence establishment on surveillance reforms.
- While petitions on the constitutionality of Aadhaar and the right to privacy were pending before the Supreme Court, the Union government constituted an expert group headed by Justice (retd) B N Srikrishna in July, 2017.
- In August, a nine-judge bench unanimously pronounced the Puttaswamy judgment that reaffirmed the fundamental right to privacy for the autonomy, dignity and liberty for every Indian.
- Justice D Y Chandrachud, who authored the majority opinion, noted the formation of the Srikrishna Committee as a positive obligation on the government to enact a law for informational privacy.
- In December 2019, government introduced the Personal Data Protection Bill, 2019 in Parliament.
- The draft law was referred to a JPC of 30 MPs that submitted a report after two years.
- With the withdrawal in Parliament on August 3, it almost seems institutional processes, in which all three branches of government worked for years, are being jettisoned in favour of “a comprehensive legal framework”.
Issues with reasons given for withdrawal of the Bill
- The JPC has nowhere suggested a withdrawal in favour of a “comprehensive legal framework”.
- The proper course was to consider the JPC’s recommendations including the dissent notes and expert analysis, redraft and introduce a new Data Protection Bill.
- Compliance burden concern of government: With the government setting the goal of a one trillion dollar digital economy, fears of a compliance burden can impede innovation and growth.
- Date protection is needed for innovation: Here, detailed reasoning is available in the Srikrishna Committee’s report as well as a growing international consensus suggesting that next-generation innovation in technology needs data protection.
- Regulatory intervention will improve business practices requiring engineering decisions that focus on user trust.
- Imperfections in law argument: With the imperfections within the Personal Data Protection Bill, 2019 and even the JPC report, there exists a reasonable argument that if passed into law, it may institutionalise bad privacy practices.
- Such a line of reasoning fails to recognise that institutional memory develops through reasonable due diligence and experience.
- Legislative foresight is limited and no law is perfect, which is why there exist parliamentary amendments and judicial review.
Conclusion
Today, there is a relentless pace of digitisation that relies on gathering personal data in all spheres of our lives. All of this is done in a legal vacuum without any oversight or remedy. This underscores the urgent need for data protection law.
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Govt withdraws Data Protection Bill
From UPSC perspective, the following things are important :
Prelims level: NA
Mains level: Issues with Personal Data Protection Bill
The government has withdrawn the Personal Data Protection Bill from Parliament after several amendments were proposed by the Joint-Parliamentary Committee.
What is Personal Data?
- Data can be broadly classified into two types: personal and non-personal data.
- Personal data pertains to characteristics, traits or attributes of identity, which can be used to identify an individual.
- Non-personal data includes aggregated data through which individuals cannot be identified.
- For example, while an individual’s own location would constitute personal data; information derived from multiple drivers’ location, which is often used to analyse traffic flow, is non-personal data.
What is Data Protection?
- Data protection refers to policies and procedures seeking to minimise intrusion into the privacy of an individual caused by collection and usage of their personal data.
Why was a bill brought for Personal Data Protection?
- In August 2017, the Supreme Court had held that Privacy is a fundamental right under Article 21 of the Constitution.
- The Court also observed that privacy of personal data and facts is an essential aspect of the right to privacy.
- In July 2017, a Committee of Experts, chaired by Justice BN Srikrishna, was set up to examine various issues related to data protection in India.
- The committee submitted its report, along with a Draft Personal Data Protection Bill, 2018 to the Ministry of Electronics and Information Technology in July 2018.
How is personal data regulated currently?
- Currently, the usage and transfer of personal data of citizens is regulated by the Information Technology (IT) Rules, 2011, under the IT Act, 2000.
- The rules hold the companies using the data liable for compensating the individual, in case of any negligence in maintaining security standards while dealing with the data.
Issues with IT Rules, 2011
- The IT rules were a novel attempt at data protection at the time they were introduced but the pace of development of digital economy has shown its shortcomings.
- For instance, (i) the definition of sensitive personal data under the rules is narrow, and (ii) some of the provisions can be overridden by a contract.
- Further, the IT Act applies only to companies, not to the government.
What the Personal Data Protection Bill sought to provide?

- Collection and storage: The bill regulate personal data related to individuals, and the processing, collection and storage of such data.
- Data Principal: Under the bill, a data principal is an individual whose personal data is being processed.
- Data fiduciary: The entity or individual who decides the means and purposes of data processing is known as data fiduciary.
- Data processing: The Bill governs the processing of personal data by both government and companies incorporated in India.
- Data localization: It also governs foreign companies, if they deal with personal data of individuals in India.
- General consent: The Bill provides the data principal with certain rights with respect to their personal data. Any processing of personal data can be done only on the basis of consent given by data principal.
- Data Protection Authority: To ensure compliance with the provisions of the Bill, and provide for further regulations with respect to processing of personal data of individuals, the Bill sets up a DPA.
Issues with the PDP Bill
- Exemptions to the govt: Section 35 of the bill permits the Central Government to exempt any agency of the Government from the provisions of the law.
- No reasonable exemptions: There is no sufficient reason for government agencies to be exempted from basic provisions of the Bill.
- Easy breach: Though this would be subject to procedures, safeguards, and oversight mechanisms to be prescribed by the Government.
- Executive hegemony: There is no scope for oversight over the executive’s decision to issue such an order.
- Arbitrary and intrusive: As demonstrated by the Pegasus case, the current frameworks for protecting citizens from arbitrary and intrusive State action lack robustness.
Why is the state given exemption?
- Biggest needy of Data: The State is one of the biggest processors of data, and has a unique ability to impact the lives of individuals.
- Welfare objectives: It has a monopoly over coercive powers as well have the obligation to provide welfare and services.
Issues with Exemption to State
- Grounds of expediency: the use of this provision on grounds of expediency is an extremely low bar for the Government to meet.
- Non requirement for exemption order: There is no requirement for an exemption order to be proportionate to meeting a particular State function.
- No oversight on executive actions: There is no scope for oversight over the executive’s decision to issue such an order or any safeguards prescribed for this process.
- State surveillance: Section 36(a) of the Bill provides for an exception where personal data is being processed against criminal investigation. This provision could therefore encourage vigilantism or enable privatized surveillance.
Best practices followed across the world
- The European GDPR (General Data Protection Regulation) is commonly seen as the pinnacle of data protection regulation worldwide.
- The EU law has in place a separate law that deals with the processing of personal data by law enforcement agencies.
- UK’s Data Protection Act dedicates Part 3 that liberalises certain obligations while at the same time ensuring that data protection rights are also protected.
Way forward
- Balancing privacy interests with those of public needs (such as that of State security) is a difficult task.
- This should undergo rigorous consultations in Parliament taking into confidence all stakeholders.
- Once debated in Parliament, one can only hope that adequate time and attention is given to finding a better balance between competing interests.
UPSC 2023 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
What laws govern tapping a phone; what are the checks in place?
From UPSC perspective, the following things are important :
Prelims level: Phone Tapping
Mains level: Read the attached story
A lady IPS officer is facing an FIR in Mumbai for allegedly tapping the phones of a Rajya Sabha MP in Maharashtra.
How are phones tapped in India?
- In the era of fixed-line phones, mechanical exchanges would link circuits together to route the audio signal from the call.
- When exchanges went digital, tapping was done through a computer.
- Today, when most conversations happen through mobile phones, authorities make a request to the service provider.
- The service provider is bound by law to record the conversations on the given number and provide these in real time through a connected computer.
Who can tap phones?
- The State Police have the powers to tap phones.
- Ten Central agencies are authorised to do so: Intelligence Bureau, CBI, Enforcement Directorate, Narcotics Control Bureau, Central Board of Direct Taxes, Directorate of Revenue Intelligence, National Investigation Agency, R&AW, Directorate of Signal Intelligence, and the Delhi Police Commissioner.
- Tapping by any other agency would be considered illegal.
What laws govern this?
- Phone tapping in India is governed by The Indian Telegraph Act, 1885.
- Section 5(2) says that “on the occurrence of any public emergency, or in the interest of the public safety”, phone tapping can be done by the Centre or states.
- It can be done in the interest of “public safety”, “sovereignty and integrity of India, the security of the State, friendly relations with foreign States or public order or for preventing incitement to the commission of an offence”.
- There is an exception for the press: “press messages intended to be published in India of correspondents accredited to the Central Government or a State Government shall not be intercepted or detained, unless their transmission has been prohibited under this sub-section”.
- The competent authority must record reasons for tapping in writing.
Who authorises phone tapping?
- Rule 419A of the Indian Telegraph (Amendment) Rules, 2007, says phone tapping orders “shall not be issued except by an order made by the Secretary to the GoI in the Ministry of Home Affairs.
- It can be authorised by the Secretary to the State Government in-charge of the Home Department in the case of a State Government.
- The order has to be conveyed to the service provider in writing; only then can the tapping begin.
What happens in an emergency?
- In unavoidable circumstances, such an order may be issued by an officer, not below the rank of a Joint Secretary to the GoI, who has been authorised by the Union Home Secretary, or the State Home Secretary.
- In remote areas or for operational reasons, if it is not feasible to get prior directions, a call can be intercepted with the prior approval of the head or the second senior-most officer of the authorised law enforcement agency at the central level, and by authorised officers, not below the rank of Inspector General of Police, at the state level.
- The order has to be communicated within three days to the competent authority, who has to approve or disapprove it within seven working days.
- If the confirmation from the competent authority is not received within the stipulated seven days, such interception shall cease.
- For example, during the 26/11 attacks in Mumbai, the authorities had no time to follow the complete procedure, and so a mail was sent to the service provider by the Intelligence Bureau.
What are the checks against misuse?
- The law is clear that interception must be ordered only if there is no other way of getting the information.
- The directions for interception remain in force, unless revoked earlier, for a period not exceeding 60 days.
- They may be renewed, but not beyond a total of 180 days.
- Any order issued by the competent authority has to contain reasons, and a copy is to be forwarded to a review committee within seven working days.
- At the Centre, the committee is headed by the Cabinet Secretary with the Law and Telecom Secretaries as members.
- In states, it is headed by the Chief Secretary with the Law and Home Secretaries as members.
- The committee is expected to meet at least once in two months to review all interception requests.
What if misuse occurs?
- When the Review Committee is of the opinion that the directions are not in accordance with the provisions referred to above it may set aside the directions.
- It may order for destruction of the copies of the intercepted message or class of messages.
- Under the rules, records pertaining to such directions shall be destroyed every six months unless these are, or are likely to be, required for functional requirements.
- Service providers too are required to destroy records pertaining to directions for interception within two months of discontinuance of the interception.
Is the process transparent?
- There are multiple provisions aimed at keeping the process transparent.
- Directions for interception are to specify the name and designation of the officer or the authority to whom the intercepted call is to be disclosed.
- The directions have to be conveyed to designated officers of the service providers in writing by an officer not below the rank of SP or Additional SP or equivalent.
- The officer is expected to maintain records with details of the intercepted call.
- The designated nodal officers of the service providers are supposed to issue acknowledgment letters to the security/law enforcement agency within two hours on receipt of an intimation.
- They are to forward every 15 days a list of interception authorisations received to the nodal officers of the security and law enforcement agencies for confirmation of authenticity.
- It makes the service providers responsible for actions of their employees.
- In case of unauthorised interception, the service provider may be fined or even lose its licence.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Why draft data accessibility policy is dangerous
From UPSC perspective, the following things are important :
Prelims level: ABHA (Ayushman Bharat Digital Health Mission)
Mains level: Paper 2- Issues with draft data accessibility policy
Context
The Ministry of Electronics and Information Technology (MEITY) released the“Draft India Data Accessibility & Use Policy 2022”.
Objectives of the policy
- If passed, it would govern, “all data and information created/generated/collected/archived by the Government of India” as much as, “State Governments [who] will also be free to adopt the provisions of the policy”.
- The twin purpose to which this data will be put to will be government-to-government sharing and high value datasets for valuation and licensing.
Issues with the draft policy
1] Original objective will get dilutes in favour of commercial interests
- The immediate risk arises when a government starts licensing citizen data.
- Over the past three years, there has been a rapid expansion in the nature and scope of our most intimate details.
- While the middle classes faced the mendacity of voluntarily linking their Aadhaar to their bank accounts and mobile connections, today, the digital sweep is all pervasive.
- For agriculture, there is an Agristack; for unorganised labourers, we have the e-SHRAM portal; in health we have Aarogya Setu and ABHA (Ayushman Bharat Digital Health Mission); and for school children and teachers there is NDEAR (National Digital Education Architecture).
- For every area of our lives, the government now has a database filled with our personal data.
- Purpose of data collection: The stated purpose for collection has been improving service delivery, planning and checking leakages.
- Public data is now being viewed as a prized asset of the Union government that should be freely shared, enriched, valued and licensed to the private sector.
- Given that more data means more money, commercial interests will prompt the government to collect granular personal details through greater capture and increased retention periods.
- Tying government policy determinations with a fiscal potential may also lead to distortion of the aims of data collection — the welfare of farmers, healthcare, unorganised labourers or even schoolchildren.
- There is no indication that consent will be sought in a meaningful form.
- Over time, the original objectives for which databases are built will get diluted in favour of commercial interests.
2] Absence of values and objectives related to transparency
- The second issue emerges from the disingenuous phrasing of “making data open by default”.
- Importance of open data: The World Bank notes that one of the first benefits of open data is that it supports “public oversight of governments and helps reduce corruption by enabling greater transparency”.
- These principles were recognised in past policy pronouncements of the government.
- Specifically, the National Data Sharing and Accessibility Policy, 2012 and the implementation guidelines formulated in 2017 refer to the Right to Information Act, 2005.
- However, within the present draft data accessibility policy, while the phrase “open data” has been used, its values and objectives are absent.
- The primary, overpowering objectives in the draft data accessibility policy and the background note are commercial.
3] Absence of legal basis
- The final area for reconsideration is a larger trend of policy-based administration detached from our constitutional framework.
- Compounding this problem, the present policy, as many others, is untethered to any legislative basis and contains no proposals for the creation of a legal framework.
- As per the Supreme Court’s Puttaswamy judgment on the fundamental right to privacy, the first ingredient to satisfy constitutionality is the existence of a legal, more often a legislative, basis.
- Without a law, there is absence of defined limits to data sharing that are enforceable and contain remedies.
- Inadequate provisions for privacy preservation: In this case, the promise of privacy preservation through anonymisation tools holds little promise when it cannot be independently assessed by a body for data protection.
- Even heavily sampled anonymised datasets are unlikely to satisfy the modern standards for anonymisation set forth by GDPR and seriously challenge the technical and legal adequacy of the de-identification release-and-forget model.
- This becomes vital as it is the principal measure suggested in the draft data accessibility policy.
Suggestions
- Parliamentary enactments also help bring accountability through deliberation that furthers foresight and contains financial memorandums – given that public money would be spent to enrich datasets of public data.
- Since the policy contemplates sharing data between databases of the central and state governments as well as through central funded schemes, it may also be prudent to deliberate further in the Rajya Sabha.
- Federalism becomes a relevant issue given that such data, when it is generated, processed and enriched by state governments to comply with interoperability standards, will lead to revenue generation for itself.
Consider the question “What are the benefits of open data? Why privacy and welfare activists have raised concerns with the Draft India Data Accessibility & Use Policy 2022?”
Conclusion
These are the glaring issues in this short, draft data accessibility policy, which appears to transform the Union government into a data broker.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
IT Ministry pitches for Data Monetization Policy
From UPSC perspective, the following things are important :
Prelims level: Data Monetization
Mains level: India Data Accessibility and Use Policy, 2022
The Ministry of Electronics and Information Technology’s proposal to monetise data collected at the central level has data policy and other experts divided.
Backgrounder to this policy
- The idea of monetising citizens’ data for greater public good was first floated by the government in the Economic Survey of 2018-19.
- It had noted that since such data is generated and belongs to the people, it should be used for the people.
- The survey had also noted that private sector could be granted access to “select databases” for commercial use.
India Data Accessibility and Use Policy, 2022
Key Propositions:
- Sale of Public Data: The data, which has been collected by the central government and undergone some value addition be allowed to be sold for some price.
- Identifying value data: The draft of the policy suggests new framework for identifying “high value data-set” on the basis of the data’s degree of importance in the market.
- Establishment of India Data Office: The draft has also suggested setting up of a central India Data Office will be created under MeitY.
- Chief Data Officer: All the central government’s line ministries will have to form their respective Data Management Unit, which will be headed by a Chief Data Officer.
- India Data Council: These chief data officers along with the India Data Officer will together form the IDC, which will decide on the policy matters of data accessibility and its usage.
- Data sharing toolkit: It will be the broad umbrella to help respective central or state government ministries and departments “assess and optimally manage” the risks associated with the release and sharing of such data.
Significance of the move
- Non-personal data as national resource: The thought process to consider non personal data as community or national resource, in itself is commendable.
- Revenue generation: The core problem with the government selling citizens’ data is the revenue generation.
- Boosting investments: The new policy will encourage data sharing among government departments and potentially help the investor ecosystem.
Issues flagged with the Policy
- Individual privacy: Data monetization may happen at cost of individual privacy. The most sought-after datasets are those that contain sensitive personal data of individuals, ex. medical history, financial data.
- Absence of Data Protection Law: The new draft policy has been announced at a time when the country is yet to finalise the countours of a data protection law.
- State interference: The policy could also face pushback from big tech companies whose business model is based on the monetisation of large-scale data collection model.
- Political risks: When the govt starts selling citizen data, even if anonymised, the government gets into business its making money.
- Un-regulation: Once the govt starts making money, its very hard to reduce that activity or to regulate it in a manner where it is impartial to the public.
- Anonymisation of data: There is a lack of proper standard and framework on data anonymisation leading to a possible that such data may be “reverse-engineered”.
Way forward
- This policy is a good intent in which the government can monetise the wide range of data it currently holds.
- However it remains to be seen how the pricing mechanism would work.
- It is important to understand that datasets cannot be priced uniformly, and the value of a particular dataset varies depending on the context in which it is solved.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
The Personal Data Protection Bill conundrum
From UPSC perspective, the following things are important :
Prelims level: Not much
Mains level: Paper 2- Issues with the Personal Data Protection Bill
Context
The Joint Committee report on the Bill has failed to provide robust draft legislation ensuring the privacy of citizens.
Background of the Personal Data Protection Bill
- The Puttaswamy judgment held that the right to privacy is a fundamental right.
- The Puttaswamy judgment and the Justice B.N. Srikrishna committee report led to the Personal Data Protection Bill of 2019.
- The Joint Committee report on the Bill has failed to provide a robust draft legislation ensuring the privacy of citizens.
Issues with the Joint Committee report on Personal Data Protection Bill
- Division into Government and private domains: The report has divided the digital world into two domains — government and private.
- This division is based on the presumption that the question of right to privacy emerges only where operations and activities of private entities are concerned.
- Exemption to government and government agencies: Clause 12 of the Bill provides exemptions for the government and government agencies and Clause 35 exempts government agencies from the entire Act itself.
- Clause 12, which says personal data can be processed without consent for the performance of any function of the state, is an umbrella clause that does not specify which ministries or departments will be covered.
- The issue with the defining harm: The Bill says, “harm includes any observation or surveillance that is not reasonably expected by the data principal”.
- This means if you install any software in your computer and the software violates the principle of privacy and data get leaked, the complaint of the data principal will not be legally tenable as the defence will be that ‘once you have installed the software, you should have reasonably expected this level of surveillance’.
- The government can use these provisions as a means of control and surveillance.
- The Committee has failed to provide formidable firewalls to protect the privacy of individuals and has also carved out a mechanism for government control over personal data.
- Against the Supreme Court judgement: The provisions are ultra vires of the judgment on privacy.
- Inclusion of non-personal data harms the economy: By including non-personal data within the ambit of the Bill, the Joint Committee has put a huge compliance burden on the economy.
- This will hit the MSME sector and small businesses harder as technical processes involving data-sharing are very expensive.
- The government-constituted panel headed by S. Gopalkrishnan also opposed the idea of including non-personal data in the Bill.
- Mandatory data localisation, it is estimated, will squeeze the economy by 0.7-1.7%.
- Hamper the smooth cross-border flow of data: This may also invite similar measures by other sovereign countries which will hamper smooth cross-border flow of data.
Concerns with the Data Protection Authority
- For compliance with the provisions of the Act, a data protection authority (DPA) has to be appointed.
- It is doubtful whether a single authority will be able to discharge so many functions in an efficient manner.
- Concern with appointment: Unlike the Justice Srikrishna committee report which provided for a judicial overlook in the appointments of the DPA, the Bill entrusts the executive with the appointments.
- Although the Joint Committee report expanded the committee, the power to appoint the panelists vests with the Central government.
- Lack of independence: Clause 86 says, “Authority should be bound by the directions of the Central Government under all cases and not just on questions of policy”.
- This weakens its independence and gives the government excessive control.
- Violation of federalism: There is internal data flow and the States are key stakeholders in the process.
- Even if the proposed central authority issues directions to allow processing of data on the grounds of ‘public order’, it is important to note that ‘public order’ is an entry in the State List.
Consider the question “What are the issues with the provision in the Personal Data Protection Bill, 2019? Suggest the way forward.”
Conclusion
The report has raised more questions than it has solved. At the time of passage of the Bill, loopholes must be plugged so that India can have a robust data protection law.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
How India’s data protection Bill compares with EU regulation
From UPSC perspective, the following things are important :
Prelims level: Key terms in PDP Bill
Mains level: Personal Data Protection Bill
The Personal Data Protection Bill is in some aspects very similar with some differences to global standards such as European Union’s General Data Protection Regulation. Here is how:
Must read:
Major similarities
[1] Consent
- EU: Users must have informed consent about the way their data is processed so that they can opt in or out.
- India: Processing of data should be done in a fair and transparent manner, while also ensuring privacy
[2] Breach
- EU: Supervisory authority must be notified of a breach within 72 hours of the leak so that users can take steps to protect information
- India: Data Protection Authority must be informed within 72 hours; DPA will decide whether users need to be informed and steps to be taken
[3] Transition period
- EU: Two-year transition period for provisions of GDPR to be put in place
- India: 24 months overall; 9 months for registration of data fiduciaries, 6 months for DPA to start
[4] Data fiduciary
- EU: Data fiduciary is any natural or legal person, public authority, agency or body that determines purpose and means of data processing
- India: Similar suggestions; additionally, NGOs which also process data to be included as fiduciaries
Differences:
[1] Anonymous information
- EU: Principles of data protection do not apply to anonymous information since it is impossible to tell one from another
- India: Non-personal data must come under the ambit of data protection law such as non-personal data
[2] Punishment
- EU: No jail terms. Fines up to 20 million euros, or in the case of an undertaking, up to 4 % of their total global turnover of the preceding fiscal year
- India: Jail term of up to 3 years, fine of Rs 2 lakh or both if de-identified data is re-identified by any person.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Back in news: Right to be Forgotten
From UPSC perspective, the following things are important :
Prelims level: Right to be Forgotten
Mains level: Art 21 and its broad aspects

The Centre has informed the Delhi High Court that the Personal Data Protection Bill 2019 contains provisions related to the ‘right to be forgotten’.
Right to be Forgotten
- ‘Right to be forgotten’ is a fairly new concept in India where an individual could seek to remove or delete online posts which may contain an embarrassing picture, video or news articles mentioning them.
- It comes under the right to privacy which has been held to be a fundamental right by the Supreme Court under Article 21.
- In 2017, the Right to Privacy was declared a fundamental right by the Supreme Court in its landmark verdict.
Why in news?
- The Personal Data Protection Bill 2019 contains provisions related to the doctrine of ‘right to be forgotten’.
- It highlighted two judgments passed by the Orissa High Court and the Karnataka High Court where they have accepted the doctrine of the ‘right to be forgotten’ as an essential part of the ‘right to privacy’.
Mention in PDP Bill
- The PDP bill aims to set out provisions meant for the protection of the personal data of individuals.
- Clause 20 under Chapter V of this bill titled “Rights of Data Principal” mentions the “Right to be Forgotten.”
- It states that the “data principal (the person to whom the data is related) shall have the right to restrict or prevent the continuing disclosure of his personal data by a data fiduciary”.
- A data fiduciary means any person, including the State, a company, any juristic entity, or any individual who alone or in conjunction with others determines the purpose and means of the processing of personal data.
Implications
- Under the Right to be forgotten, users can de-link, limit, delete or correct the disclosure of their personal information held by data fiduciaries.
Other similar provisions
- Section 69A of the IT Act does provide for removal of “certain unlawful information” from an intermediary platform.
- It primarily applies to ‘national security and public order related issues’ only.
Also read:
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Draft Personal Data Protection Bill, 2021
From UPSC perspective, the following things are important :
Prelims level: Right to Privacy
Mains level: Personal Data Protection Bill
The Joint Parliamentary Committee (JPP) on the Personal Data Protection Bill of 2019 is said to have adopted the final draft. The Bill will be tabled in the Winter Session of Parliament.
What is Personal Data?
- Data can be broadly classified into two types: personal and non-personal data.
- Personal data pertains to characteristics, traits or attributes of identity, which can be used to identify an individual.
- Non-personal data includes aggregated data through which individuals cannot be identified.
- For example, while an individual’s own location would constitute personal data; information derived from multiple drivers’ location, which is often used to analyse traffic flow, is non-personal data.
What is Data Protection?
- Data protection refers to policies and procedures seeking to minimise intrusion into the privacy of an individual caused by collection and usage of their personal data.
Why was a bill brought for Personal Data Protection?
- In August 2017, the Supreme Court had held that Privacy is a fundamental right under Article 21 of the Constitution.
- The Court also observed that privacy of personal data and facts is an essential aspect of the right to privacy.
- In July 2017, a Committee of Experts, chaired by Justice BN Srikrishna, was set up to examine various issues related to data protection in India.
- The committee submitted its report, along with a Draft Personal Data Protection Bill, 2018 to the Ministry of Electronics and Information Technology in July 2018.
How is personal data regulated currently?
- Currently, the usage and transfer of personal data of citizens is regulated by the Information Technology (IT) Rules, 2011, under the IT Act, 2000.
- The rules hold the companies using the data liable for compensating the individual, in case of any negligence in maintaining security standards while dealing with the data.
Issues with IT Rules, 2011
- The IT rules were a novel attempt at data protection at the time they were introduced but the pace of development of digital economy has shown its shortcomings.
- For instance, (i) the definition of sensitive personal data under the rules is narrow, and (ii) some of the provisions can be overridden by a contract.
- Further, the IT Act applies only to companies, not to the government.
What does the Personal Data Protection Bill provide?

- Collection and storage: The bill regulate personal data related to individuals, and the processing, collection and storage of such data.
- Data Principal: Under the bill, a data principal is an individual whose personal data is being processed.
- Data fiduciary: The entity or individual who decides the means and purposes of data processing is known as data fiduciary.
- Data processing: The Bill governs the processing of personal data by both government and companies incorporated in India.
- Data localization: It also governs foreign companies, if they deal with personal data of individuals in India.
- General consent: The Bill provides the data principal with certain rights with respect to their personal data. Any processing of personal data can be done only on the basis of consent given by data principal.
- Data Protection Authority: To ensure compliance with the provisions of the Bill, and provide for further regulations with respect to processing of personal data of individuals, the Bill sets up a DPA.
Issues with the PDP Bill
- Exemptions to the govt: Section 35 of the bill permits the Central Government to exempt any agency of the Government from the provisions of the law.
- No reasonable exemptions: There is no sufficient reason for government agencies to be exempted from basic provisions of the Bill.
- Easy breach: Though this would be subject to procedures, safeguards, and oversight mechanisms to be prescribed by the Government.
- Executive hegemony: There is no scope for oversight over the executive’s decision to issue such an order.
- Arbitrary and intrusive: As demonstrated by the Pegasus case, the current frameworks for protecting citizens from arbitrary and intrusive State action lack robustness.
Why is the state given exemption?
- Biggest needy of Data: The State is one of the biggest processors of data, and has a unique ability to impact the lives of individuals.
- Welfare objectives: It has a monopoly over coercive powers as well have the obligation to provide welfare and services.
Issues with Exemption to State
- Grounds of expediency: the use of this provision on grounds of expediency is an extremely low bar for the Government to meet.
- Non requirement for exemption order: There is no requirement for an exemption order to be proportionate to meeting a particular State function.
- No oversight on executive actions: There is no scope for oversight over the executive’s decision to issue such an order or any safeguards prescribed for this process.
- State surveillance: Section 36(a) of the Bill provides for an exception where personal data is being processed against criminal investigation. This provision could therefore encourage vigilantism or enable privatized surveillance.
Best practices followed across the world
- The European GDPR (General Data Protection Regulation) is commonly seen as the pinnacle of data protection regulation worldwide.
- The EU law has in place a separate law that deals with the processing of personal data by law enforcement agencies.
- UK’s Data Protection Act dedicates Part 3 that liberalises certain obligations while at the same time ensuring that data protection rights are also protected.
Way forward
- Balancing privacy interests with those of public needs (such as that of State security) is a difficult task.
- This should undergo rigorous consultations in Parliament taking into confidence all stakeholders.
- Once debated in Parliament, one can only hope that adequate time and attention is given to finding a better balance between competing interests.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Facial Recognition Technology
From UPSC perspective, the following things are important :
Prelims level: Right to privacy
Mains level: Paper 2- Issues with use of facial recognition technologies by the police
Context
According to police officials, more than six lakh CCTV cameras have already been deployed in the city, with the very real possibility that this number will continue to increase. These all-pervasive cameras will soon be connected in a real-time network managed by Hyderabad’s Command and Control Centre.
Facial Recognition
It is a biometric technology that uses distinctive features of the face to identify and distinguish an individual. Over a period of almost 6 decades, it has evolved in many ways- from looking at 3D contours of a face to recognizing skin patterns.
How does it work?
- The facial recognition system works primarily by capturing the face & its features through the camera and then using various kinds of software to reconstruct those features.
- The captured face along with its features is stored into a database, which can be integrated with any kind of software that may be used for security purposes, banking services, etc.
- In the Automated Facial Recognition System (AFRS), the large database (containing photos and videos of peoples’ faces) is used to match and identify the person. The image of an unidentified person, taken from CCTV footage, is compared to the existing database using Artificial Intelligence technology, for pattern-finding and matching.
What are the uses?
- Authentication: It is used for identification and authentication purposes with a success rate of almost 75%.
- For instance, the NCRB’s Crime and Criminal Tracking Network & Systems (CCTNS) managing crime data for police, use automated facial recognition to identify criminals, missing people, and unidentified dead bodies, as well as for “crime prevention”.
- The project is aimed at being compatible with other biometrics such as iris and fingerprints.
- The integration of fingerprint databases, face recognition software and iris scans will massively boost the police department’s crime investigation capabilities.
- Force Multiplier: In India, where there are just 144 constables per 1 lakh citizens, this can act as a force multiplier. It neither requires too much manpower nor regular up-gradation. Hence, this technology coupled with the present manpower in place can act as a game-changer.
- Varied applications: It is increasingly being used for everything from unlocking mobile phones to validating the identity, from auto-tagging of digital photos to finding missing persons, and from targeted advertising to law enforcement.
Opposition to facial recognition technologies
- How it works: Facial recognition technology identifies the distinctive features of a person’s face to create a biometric map, which an algorithm then matches to possible individuals.
- The system searches across databases of millions of images scraped without knowledge or consent and often fails.
- Severe scrutiny: The use of facial recognition technology is already under severe scrutiny around the world, with some jurisdictions, including Belgium and Luxembourg, have already banned its use.
- Ban by EU: The European Union is in the process of finalizing and passing one of the most comprehensive bans on facial recognition technology yet, while in the United States, multiple cities- and state-level bans and moratoria have been imposed.
- More than 200 organizations have called for a global ban on the use of biometric surveillance technologies that enable mass and discriminatory surveillance, while even Facebook announced that it would be shutting down its facial recognition program.
Issues with the use of facial recognition technologies in India
- Violation of the right to privacy: The right to privacy was recognized as a fundamental right, included under the right to life and liberty by the Supreme Court of India in 2017.
- Absence of legal framework: Without a law in place to regulate data collection and to act as an oversight mechanism, valid concerns about privacy and other rights violations continue to arise.
- High Infrastructural Costs: Technologies like Artificial Intelligence and Big Data are costly to implement. The size of stored information is extremely large and requires huge network & data storage facilities, which are currently not available in India.
- Image Collection: The sources from which images will be collected to create a repository/database need to be known.
- The concern of Data Leakage: In today’s world of cybercrime, it is important to put appropriate safeguards in place in order to ensure the integrity of the repository/database, so that it doesn’t leak out the information and is not privatized or monetized.
- Required Expertise: Experts are needed to verify and authenticate data collected before storing them who should be provided proper training to protect & avoid abuse and misuse of the collected data & database.
- Reliability & Authenticity: As the data collected may be used in the court of law during the course of a criminal trial, the reliability and the admissibility of the data along with standards and procedures followed would be taken into consideration. Hence, the authenticity of the data is crucial.
- Huge amounts of public money are being spent on these technologies with no evidence of their effectiveness, further squandering precious public funds.
The National Automated Facial Recognition System
- To empower the Indian police with information technology, India approved the implementation of the National Automated Facial Recognition System (NAFRS).
- On its implementation, it will function as a national-level search platform that will use facial recognition technology.
- It will help to facilitate investigation of crime or for identifying a person of interest regardless of face mask, makeup, plastic surgery, beard, or hair extension.
Way Forward
- Save the time of police: This is a compare and contrast tool meant for identification based on existing information. The process of identification can be accelerated by its use.
- Proper Legal safeguards are a must: With proper safeguards, this technology is much needed for India. Having the biggest IT workforce in the world, state-of-the-art technology can act as a game-changer for India.
- Need to learn from Global examples: Police departments in London are under pressure to put a complete end to the use of facial recognition systems following evidence of discrimination and inefficiency.
- Hence, it is necessary to make use of such technology, but it cannot act as the silver bullet for all the police reforms that we need.
Conclusion
Government programs such as Safe City, Smart City, and the Nirbhaya Fund have been utilized to bankroll these projects — yet the human rights violations that occur as a result of their use far outweigh any purported benefit that these technologies claim to provide.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Supreme Court forms committee to examine Pegasus allegations
From UPSC perspective, the following things are important :
Prelims level: Articles mentioned in the newscard
Mains level: Pegasus issue

The Supreme Court has appointed an independent expert technical committee overseen by a former apex court judge, Justice R.V. Raveendran, to examine allegations that the government used Israeli spyware, Pegasus, to snoop on its own citizens.
Why need a committee?
- Decisions in cases seeking enforcement of fundamental rights are based on facts.
- The task of determining these facts, when they are disputed or unknown, are often assigned to committees, which act as an agent of the court.
- Such committees or fact-finding teams can summon individuals, prepare ground reports, and inform the court.
- The Pegasus case involves technical questions, and requires extensive fact-finding for the court to determine whether fundamental rights were violated, and to pass suitable orders.
Functions of the committee:

What is Pegasus?
- All spyware do what the name suggests — they spy on people through their phones.
- Pegasus works by sending an exploit link, and if the target user clicks on the link, the malware or the code that allows the surveillance is installed on the user’s phone.
- A presumably newer version of the malware does not even require a target user to click a link.
- Once Pegasus is installed, the attacker has complete access to the target user’s phone.
Why in news?
- The three-judge bench, headed by CJI N V Ramana rejected the government’s plea to let it constitute an expert panel to investigate the issue.
What did the SC rule?
- The SC order broadly addresses three issues that have been flagged in the Pegasus row:
- Citizen’s right to privacy (Article 21)
- Judicial review when the executive invokes national security (Article 13, Article 32)
(Article 13: declares that any law which contravenes any of the provisions of the part of Fundamental Rights shall be void.
Articles 32 and 226 entrusts the roles of the protector and guarantor of fundamental rights to the Supreme and High Courts.)
- Implications of surveillance on free speech
[A] Upholding Right to Privacy
- The Court, pointing to its own judgment in K S Puttaswamy Case (2017) has said that “right to privacy (under Article 21) is as sacrosanct as human existence.
- It is inalienable to human dignity and autonomy.
- While agreeing that it is not an absolute right, the Court has said any restrictions “must necessarily pass constitutional scrutiny”.
- Any surveillance or snooping done on an individual by the state or any outside agency is an infringement of that person’s right to privacy.
- Hence, any violation of that right by the state, even in national interest, has to follow procedures established by the law.
[B] Linking surveillance and censorship
- The Court has also drawn a link between:
- Surveillance, especially the knowledge that one is under the threat of being spied on”, and
- Censorship, particularly self-censorship, to reflect on the potential chilling effect that snooping techniques may have
- The chilling effect surveillance can produce, is an assault on the vital public-watchdog role of the press, which may undermine the ability of the press to provide accurate and reliable information.
[C] Constituting a panel
- The Court has constituted a panel of experts under former SC judge Justice R V Raveendran.
- It has sharply defined the questions it needs to ask and find answers to: Was any Pegasus suite of spyware acquired by the central or any state government for use against the citizens of India.
- It would inquire under what law, rule, guidelines, protocol or lawful procedure was such deployment made.
- These are vital questions at the heart of a citizen’s basic rights.
Significance of the Judgement
- The order is a strong rebuttal of the government’s specious and self-serving use of national security.
- The Court has ruled that the state does not get a free pass every time the spectre of ‘national security’ is raised.
- This also means “no omnibus prohibition can be called for against judicial review” if the matter impinges on national security.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Contentious Clauses in Data Protection Bill
From UPSC perspective, the following things are important :
Prelims level: Data privacy
Mains level: Contentious Clauses in Data Protection Bill
The Joint Parliamentary Committee on Data Protection has found a middle ground on certain contentious clauses. Many panellists had objected to the clause, saying that it made the entire Act infructuous.
What is the issue?
- The Data Protection Law has some clauses in the name of “sovereignty”, “friendly relations with foreign states” and “security of the state”.
- These clauses allow any agency under the Union government exemption from all or any provisions of the law.
- The legislation gives powers to the Central government to suspend all or any of the provisions of the Act for government agencies.
Personal Data Protection Bill, 2019
- The PDP Bill was introduced in Lok Sabha by the Minister of Electronics and Information Technology in 2019.
- The Bill seeks to provide for protection of personal data of individuals, and establishes a Data Protection Authority for the same.
Here are the key features:
Applicability
- The Bill governs the processing of personal data by: (i) government, (ii) companies incorporated in India and (iii) foreign companies dealing with personal data of individuals in India.
- Personal data is data which pertains to characteristics, traits or attributes of identity, which can be used to identify an individual.
- The Bill categorises certain personal data as sensitive personal data.
- This includes financial data, biometric data, caste, religious or political beliefs, or any other category of data specified by the government, in consultation with the Authority and the concerned sectoral regulator.
Data fiduciary and his obligations
- A data fiduciary is an entity or individual who decides the means and purpose of processing personal data. Such processing will be subject to certain purpose, collection and storage limitations.
- For instance, personal data can be processed only for specific, clear and lawful purpose.
- Additionally, all data fiduciaries must undertake certain transparency and accountability measures such as: (i) implementing security safeguards (such as data encryption and preventing misuse of data), and (ii) instituting grievance redressal mechanisms to address complaints of individuals.
- They must also institute mechanisms for age verification and parental consent when processing sensitive personal data of children.
Rights of the individual
The Bill sets out certain rights of the individual (or data principal). These include the right to:
- Obtain confirmation from the fiduciary on whether their personal data has been processed
- Seek correction of inaccurate, incomplete, or out-of-date personal data
- Have personal data transferred to any other data fiduciary in certain circumstances and
- Restrict continuing disclosure of their personal data by a fiduciary, if it is no longer necessary or consent is withdrawn
Grounds for processing personal data
- The Bill allows the processing of data by fiduciaries only if consent is provided by the individual. However, in certain circumstances, personal data can be processed without consent.
- These include: (i) if required by the State for providing benefits to the individual, (ii) legal proceedings, (iii) to respond to a medical emergency.
Social media intermediaries
- The Bill defines these to include intermediaries which enable online interaction between users and allow for sharing of information.
- All such intermediaries which have users above a notified threshold, and whose actions can impact electoral democracy or public order, have certain obligations, which include providing a voluntary user verification mechanism for users in India.
Data Protection Authority
- The Bill sets up a Data Protection Authority which may: (i) take steps to protect interests of individuals, (ii) prevent misuse of personal data, and (iii) ensure compliance with the Bill.
- It will consist of a chairperson and six members, with at least 10 years’ expertise in the field of data protection and information technology.
- Orders of the Authority can be appealed to an Appellate Tribunal. Appeals from the Tribunal will go to the Supreme Court.
Transfer of data outside India
- Sensitive personal data may be transferred outside India for processing if explicitly consented to by the individual, and subject to certain additional conditions.
- However, such sensitive personal data should continue to be stored in India.
- Certain personal data notified as critical personal data by the government can only be processed in India.
Exemptions:
The central government can exempt any of its agencies from the provisions of the Act:
- In interest of security of state, public order, sovereignty and integrity of India and friendly relations with foreign states
- For preventing incitement to commission of any cognisable offence (i.e. arrest without warrant) relating to the above matters
- Processing of personal data is also exempted from provisions of the Bill for certain other purposes such as: (i) prevention, investigation, or prosecution of any offence, or (ii) personal, domestic, or (iii) journalistic purposes.
- However, such processing must be for a specific, clear and lawful purpose, with certain security safeguards.
Sharing of non-personal data with government:
The central government may direct data fiduciaries to provide it with any:
- Non-personal data and
- Anonymised personal data for better targeting of services.
Amendments to other laws
- The Bill amends the Information Technology Act, 2000 to delete the provisions related to compensation payable by companies for failure to protect personal data.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Deployment of Facial Recognition Systems (FRS) in India
From UPSC perspective, the following things are important :
Prelims level: FRS
Mains level: Right to Privacy Issues

India has seen a rapid deployment of Facial Recognition Systems (FRS) in recent years, both by the Centre and State governments, without putting in place any law to regulate their use.
Facial Recognition System
- A FRS is a technology capable of matching a human face from a digital image or a video frame against a database of faces.
- It is typically employed to authenticate users through ID verification services, works by pinpointing and measuring facial features from a given image.
Why in news?
- There is a growing unabated use of this potentially invasive technology without any safeguards.
- This poses a huge threat to the fundamental rights to privacy and freedom of speech and expression of the citizens.
FRS in India
- Currently, 18 FRSs are in active utilisation by the Centre and State governments for the purpose of surveillance, security and authentication of identity.
- 49 more systems are in the process of being installed by different government agencies.
- Delhi Police was the first law enforcement agency in the country to start using the technology in 2018.
- Only Telangana is ahead of Delhi at present with four facial recognition systems in active utilization for surveillance and authentication of identity.
Judicial scrutiny of the move
- States say that they are authorized by the Delhi High Court in terms of the decision in the case of ‘Sadhan Haldar vs NCT of Delhi’.
- In that particular case, the High Court had authorized the Delhi police to obtain facial recognition technology for the purpose of tracking and reuniting missing children.
- FRS may be used in the investigation in the interest of safety and security of the general public.
A potential mis-use?
Ans. Can’t say!
- Activists pointed out that Delhi Police was now using the FRS, which was meant for tracking missing children, for wider security and surveillance and investigation purpose.
- There is a “function creep” happening with Police gradually using the technology beyond its intended purpose.
- For example, the use of FRS to identify accused who took part in the farmers’ tractor rally violence in January this year.
Need of the hour
Ans. Bring accountability
- Surveillance of any kind happens in secret and the people generally don’t know that they are being watched.
- The idea behind is to bring light to the fact that these technology systems are being used without any laws in place to regulate them.
- Police and state authorities should use such technologies for specific and special purposes with proper authorization.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Delhi HC observations on Right to be Forgotten
From UPSC perspective, the following things are important :
Prelims level: Article 21
Mains level: Right to be Forgotten
The Delhi High Court upheld the view that the “Right to Privacy” includes the “Right to be Forgotten” and the “Right to be Left Alone”.
Right to be Forgotten in India
- The Right to be Forgotten falls under the purview of an individual’s right to privacy, which is governed by the Personal Data Protection Bill that is yet to be passed by Parliament.
- In 2017, the Right to Privacy was declared a fundamental right by the Supreme Court in its landmark verdict.
- The court said at the time that “the right to privacy is protected as an intrinsic part of the right to life and personal liberty under Article 21 and as a part of the freedoms guaranteed by Part III of the Constitution”.
What was the recent case?
- The TV celebrity had moved Delhi High Court with the plea that orders be issued to Google and relevant entities to facilitate the removal of posts, videos, articles and any information related to incidents that he was involved.
- His plea cited that his presence on the internet is a source of “utmost psychological pain” to him.
Legal issues
- India does not have a law yet on right to be forgotten.
- In the meantime, the Information Technology Rules, 2011 — which is the current regime governing digital data — does not have any provisions relating to the right to be forgotten.
- The Personal Data Protection (PDP) Bill was tabled in Parliament in 2019 and is being examined by a Joint Parliamentary Committee (JPC).
Key features of PDP Bill
- Personal Data: Section 20 of the PDP Bill says that a ‘data principal’ — or the person who generates the data or to whom the information pertains — can rightfully ask a ‘data fiduciary’, which is any entity that stores or processes such data, to “restrict or prevent the continuing disclosure of his personal data” in specific circumstances.
- Purpose of data: To seek the erasure of data, it is necessary to establish that it “has served the purpose for which it was collected or is no longer necessary for the purpose; was made with the consent of the data principal.
- Right to be forgotten: The Bill says that the right to be forgotten can be enforced only on an order of an adjudicating officer following an application filed by the data principal.
- Contravention with Free Speech: However, the decision on whether the right to be forgotten can be granted with respect to any data will depend on whether it contravenes “the right to freedom of speech and expression and the right to information of any other citizen”.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
The National Automated Facial Recognition System
From UPSC perspective, the following things are important :
Prelims level: Not much
Mains level: Paper 2- Issues with automated facial recognition system
Context
On June 23, 2021, the Joint Committee examining the Personal Data Protection Bill (2019) was granted a fifth extension by Parliament. While the Government has been simultaneously exploring the potential of facial recognition technology.
Automatic Facial Recognition in India
- To empower the Indian police with information technology, India approved implementation of the National Automated Facial Recognition System (NAFRS).
- On its implementation, it will function as a national-level search platform that will use facial recognition technology.
- It will help to facilitate investigation of crime or for identifying a person of interest regardless of face mask, makeup, plastic surgery, beard or hair extension.
Issues with AFR technology
- Intrusive in nature: The technology is absolutely intrusive, for the purposes of ‘verification’ or ‘identification’, the system compares the faceprint generated with a large existing database of faceprints typically available to law enforcement agencies.
- Accuracy and bias: Though the accuracy of facial recognition has improved over the years due to modern machine-learning algorithms, the risk of error and bias still exists.
- With the element of error and bias, facial recognition can result in profiling of some overrepresented groups (such as Dalits and minorities) in the criminal justice system.
- Privacy: As NAFRS will collect, process, and store sensitive private information: facial biometrics for long periods; if not permanently — it will impact the right to privacy.
- Accordingly, it is crucial to examine whether its implementation is arbitrary and thus unconstitutional, i.e., is it ‘legitimate’, ‘proportionate to its need’ and ‘least restrictive’?
- The Supreme Court, in the K.S. Puttaswamy judgment provided a three-fold requirement to safeguard against any arbitrary state action.
- Unfortunately, NAFRS fails each one of these tests.
- Any encroachment on the right to privacy requires the existence of ‘law’ (to satisfy legality of action); there must exist a ‘need’, in terms of a ‘legitimate state interest’; and, the measure adopted must be ‘proportionate’ and it should be ‘least intrusive.’
- Lack of law: It does not stem from any statutory enactment (such as the DNA Technology (Use and Application) Regulation Bill 2018 proposed to identify offenders or an executive order of the Central Government.
- Rather, it was merely approved by the Cabinet Committee on Economic Affairs in 2009.
- Fails proportionality test: Even if we assume that there exists a need for NAFRS to tackle modern day crimes, this measure is grossly disproportionate.
- For NAFRS to achieve the objective of ‘crime prevention’ or ‘identification’ will require the system to track people on a mass scale — avoiding a CCTV in a public place is difficult — resulting in everyone becoming a subject of surveillance: a disproportionate measure.
- Impact on civil liberties: As anonymity is key to functioning of a liberal democracy, unregulated use of facial recognition technology will dis-incentivise independent journalism or the right to assemble peaceably without arms, or any other form of civic society activism.
- Due to its adverse impact on civil liberties, some countries have been cautious with the use of facial recognition technology.
- In the United States, the Facial Recognition and Biometric Technology Moratorium Act of 2020 was introduced in the Senate to prohibit biometric surveillance without statutory authorisation.
- Similarly, privacy watchdogs in the European Union have called for a ban on facial recognition.
Way forward
- Statutory basis: NAFRS should have statutory authorisation, and guidelines for deployment.
- Data protection law: In the interest of civil liberties it is important to impose a moratorium on the use of facial recognition technology till we enact a strong and meaningful data protection law.
Consider the question “What are the issues associated with the deployment of NAFRS? Suggest the way forward.”
Conclusion
In sum, even if facial recognition technology is needed to tackle modern-day criminality in India, without accountability and oversight, facial recognition technology has strong potential for misuse and abuse.
UPSC 2022 countdown has begun! Get your personal guidance plan now! (Click here)
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Surveillance and human rights
From UPSC perspective, the following things are important :
Prelims level: Right to privacy
Mains level: Paper 2- Surveillance and its impact on democracy
Context
The Pegasus revelations reflect an attack on Indian democracy and Indian citizens.
Role of government in protecting the fundamental and human rights of citizens
- The surveillance of the target group in India through Pegasus raises doubts about the functioning of democracy in India.
- Constitutional duty of government: The government has a constitutional duty to protect the fundamental and human rights of its citizens, irrespective of who they are.
- There is clear evidence that the rule of law has been undermined.
- More evidently, this reflects extremely poor governance.
- The Intelligence Bureau, the Research and Analysis Wing, and the National Security Council Secretariat should have forewarned the government and citizens against such surveillance seriously violating privacy and fundamental rights.
- The Supreme Court, in K.S. Puttaswamy v. Union of India (2017), declared privacy a constitutionally protected value.
Violation of human rights
- India is a signatory to the Universal Declaration of Human Rights.
- Article 12 provides that everyone has the right to the protection of the law against arbitrary interference with his privacy, family, home or correspondence.
- The International Covenant on Civil and Political Rights, also signed by India, in Article 17 states, “No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence, nor to unlawful attacks on his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks.”
- In K.S. Puttaswamy, the Supreme Court noted India’s commitments under international law and held that by virtue of Article 51 of the Constitution, India has to endeavour to “foster respect for international law and treaty obligations…”
- The Protection of Human Rights Act, 1993 is a fallout of this commitment.
Recommendations on digital communication technologies
- The annual report of the United Nations High Commissioner for Human Rights (UNHCHR) in 2014 made recommendations on “digital communications technologies”.
- Judicial oversight: The UNHCHR report stated, judicial involvement that meets international standards can help to make it more likely that the overall statutory regime will meet the minimum standards that international human rights law requires.
- At the same time, the report stated that judicial involvement in oversight should not be viewed as a panacea.
- Independent body: The report also recommended an independent oversight body to keep checks.
- Effective remedy to victim: The International Covenant on Civil and Political Rights requires states parties to ensure that victims of violations of the Covenant have an effective remedy.
- Role of business: The report also dealt with the role of businesses and stated that when a state requires that an information and communications technology company provide user data, it can only supply it in respect of legitimate reasons.
- Earlier, due to concerns of member states, the General Assembly adopted Resolution 68/167 affirming that rights held by people offline must also be protected online.
- The resolution also called upon all states to respect and protect the right to privacy, including in digital communication.
Conclusion
Indians have a right to call upon NSO to terminate the agreement, if any, with the Indian government or any private player and to cooperate with citizens to unravel the truth.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Right to be Forgotten in India
From UPSC perspective, the following things are important :
Prelims level: Right to be Forgotten
Mains level: Right to Privacy Issues
A TV celebrity has approached the Delhi High Court with a plea saying that his videos, photographs, and articles, etc. be removed from the internet citing his “Right to be Forgotten”.
What is the plea about?
- The plea mentions that the posts and videos on the internet related to him have caused the petitioner psychological pain for his diminutive acts.
- The plea also states that the petitioner’s mistakes in his personal life become and remains in public knowledge for generations to come.
- Consequently, the values enshrined under Article 21 of the Indian Constitution and the emergent jurisprudential concept of the Right to be Forgotten becomes extremely relevant in the present case.”
What is the ‘Right to be Forgotten’ in the Indian context?
- The Right to be Forgotten falls under the purview of an individual’s right to privacy, which is governed by the Personal Data Protection Bill that is yet to be passed by Parliament.
- In 2017, the Right to Privacy was declared a fundamental right by the Supreme Court in its landmark verdict.
What does the Personal Data Protection Bill say about this?
- The Personal Data Protection Bill was introduced in Lok Sabha on December 11, 2019, and it aims to set out provisions meant for the protection of the personal data of individuals.
- Clause 20 under Chapter V of this draft bill titled “Rights of Data Principal” mentions the “Right to be Forgotten.”
- It states that the “data principal (the person to whom the data is related) shall have the right to restrict or prevent the continuing disclosure of his personal data by a data fiduciary”.
- Therefore, broadly, under the Right to be forgotten, users can de-link, limit, delete or correct the disclosure of their personal information held by data fiduciaries.
- A data fiduciary means any person, including the State, a company, any juristic entity, or any individual who alone or in conjunction with others determines the purpose and means of the processing of personal data.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Surveillance Laws in India and Individual Privacy
From UPSC perspective, the following things are important :
Prelims level: Right to Privacy
Mains level: Surveillance related issues
After alleged WhatsApp snooping cases the government has claimed that all interception in India takes place lawfully.
Try this question in the comment box:
Q.There should be some reasonable basis or some tangible evidence to initiate or seek approval for interception by State authorities. Critically comment with respect to individual privacy and surveillance laws in India. (250W)
What are the laws covering surveillance in India?
Communication surveillance in India takes place primarily under two laws:
- Telegraph Act, 1885: It deals with interception of calls.
- Information Technology Act, 2000: It was enacted to deal with surveillance of all electronic communication, following the Supreme Court’s intervention in 1996.
[I] Telegraph Act, 1885
- Call interception: Under Section 5(2) of this law, the government can intercept calls only in certain situations.
- For sovereignty: They include the interests of the sovereignty and integrity of India, the security of the state, friendly relations with foreign states or public order, or for preventing incitement to the commission of an offense.
- Free speech restrictions: These are the same restrictions imposed on free speech under Article 19(2) of the Constitution.
- Exceptions for journalists: A provision in Section 5(2) states that even this lawful interception cannot take place against journalists.
Supreme Court intervention
- In Public Union for Civil Liberties v Union of India (1996), the Supreme Court pointed out the lack of procedural safeguards in the provisions of the Telegraph Act.
- The court noted that authorities engaging in interception were not even maintaining adequate records and logs on an interception.
- It noted that- tapping is a serious invasion of an individual’s privacy.
- The Supreme Court’s guidelines formed the basis of introducing Rule 419A in the Telegraph Rules in 2007 and later in the rules prescribed under the IT Act in 2009.
- Rule 419A states that a Secretary in the MHA can pass orders of interception in the case of the Centre, and a secretary-level officer who is in charge of the Home Department can issue such directives in States.
[II] IT Act, 2000
- Electronic surveillance: Section 69 of the IT Act and the IT (Procedure for Safeguards for Interception, Monitoring, and Decryption of Information) Rules, 2009 were enacted to further the legal framework for electronic surveillance.
- Data interception: Under the IT Act, all electronic transmission of data can be intercepted.
- Section 69 of the IT Act adds another aspect that makes it broader — interception, monitoring, and decryption of digital information “for the investigation of an offense”.
Identifying the gaps
- In 2012, the Planning Commission was tasked with identifying the gaps in laws affecting privacy.
- It pointed out divergence in-laws on permitted grounds, “type of interception”, “granularity of information that can be intercepted”, the degree of assistance from service providers, and the “destruction and retention” of intercepted material.
- Although the grounds of selecting a person for surveillance and the extent of information gathering have to be recorded in writing, the wide reach of these laws has not been tested in court against the cornerstone of fundamental rights.
Only inference: Right to Privacy is not absolute
- Only in such exceptional circumstances, however, can an individual’s right to privacy be superseded to protect the national interest.
- In today’s times, when fake news and illegal activities such as cyber terrorism on the dark web are on the rise, the importance of reserving such powers to conduct surveillance cannot be undermined.
What is our concern?
- For Pegasus-like spyware to be used lawfully, the government would have to invoke both the IT Act and the Telegraph Act.
- There is no comprehensive data protection law leaving ambiguities over several laws.
- A comprehensive data protection law to address the gaps in existing frameworks for surveillance is yet to enact.
What should be the basis for surveillance?
- There should be some reasonable basis or some tangible evidence to initiate or seek approval for interception by State authorities.
- Any action without such evidence or basis would be struck down by courts as arbitrary, or invasive of one’s right to privacy.
- Any digression from the ethical and legal parameters set by law would be tantamount to a deliberate invasion of citizens’ privacy and make India a surveillance state.
Way forward
- The security of a device becomes one of the fundamental bedrock of maintaining user trust as society becomes more and more digitized.
- There is an urgent need to take up this issue seriously by constituting an independent high-level inquiry with credible members and experts that can restore confidence and conduct its proceedings transparently.
Conclusion
- We must recognize that national security starts with securing the smartphones of every single Indian by embracing technologies such as encryption rather than deploying spyware.
- This is a core part of our fundamental right to privacy.
- This intrusion by spyware is not merely an infringement of the rights of the citizens of the country but also a worrying development for India’s national security apparatus.
Back2Basics: Right to Privacy
- Right to Privacy can be defined as:
- a right to be let alone;
- the right of a person to be free from any unwarranted publicity;
- the right to live without any unwarranted interference by the public in matters with which the public is not necessarily concerned”.
- Article 21 states that “No person shall be deprived of his life or personal liberty.
- The right to privacy is not enumerated as a Fundamental Right in the Constitution of India.
- After reading Article 21, it has been interpreted that the term ‘life’ includes all those aspects of life which go to make a man’s life meaningful, complete, and worth living.
- The scope of this right first came up for consideration in Kharak Singh’s Case which was concerned with the validity of certain regulations that permitted surveillance of suspects.
- The 1978’s judgment in Maneka Gandhi Case established the new doctrine that the distinct fundamental rights are not carved out from each other but overlap paving way for the Right to Privacy.
- The latest interpretation included the Naz Foundation Case (2009) in which Delhi HC gave the landmark decision on consensual homosexuality.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
EdTech needs an ethics policy
From UPSC perspective, the following things are important :
Prelims level: Not much
Mains level: Paper 2- Need for ethics policy in EdTech
The article highlights the privacy concerns associated with EdTech apps in the absence of a regulatory framework.
Privacy risks associated with EdTechs
- Since the onset of the pandemic, online education has replaced conventional classroom instruction.
- This has given rise to several EdTech apps which have become popular.
- To perform the process of learning customisation, the apps collect large quantities of data from the learners through the gadgets that the students use.
- These data are analysed in minute detail to customise learning and design future versions of the app.
- The latest mobile phones and hand-held devices have a range of sensors like GPS, gyroscope, accelerometer, magnetometer and biometric sensors apart from the camera and microphones.
- These provide data about the learner’s surroundings along with intimate data like the emotions and attitudes experienced and expressed via facial expressions and body temperature changes.
- In short, the app and device have access to the private spaces of the learner that one would not normally have access to.
Informed consent in research
- Researchers dealing with human subjects need to comply with ethics rules along with global standards.
- One of the cardinal rules that should never be broken is informed consent.
- Before any research on human subjects is undertaken, researchers have to submit detailed proposals to their respective ethics committees and obtain their permissions.
- Further, a researcher working with children, for example, would also have to convince schoolteachers, parents, and school managements about the nature of the research to be undertaken, type of data to be collected, method of storage, the potential harmful effects of such data, etc.
Minimal safeguards in EdTech
- The safeguards that traditional researchers are subject to are either missing or minimal in research that the EdTech industry promotes.
- The concept of informed consent is not meaningful since there are no proper primers to explain to stakeholders the intricacies in layperson terms.
- Since India does not have protection equivalent to the GDPR, private data collected by an EdTech company can be misused or sold to other companies with no oversight or protection.
Way forward
- Given these realities, it is necessary to formulate an ethics policy for EdTech companies.
- Such a policy draft should be circulated both online and offline for discussions and criticism.
- Issues of fairness, safety, confidentiality and anonymity of the user would have to be dealt with.
- EdTech companies would have to be encouraged to comply in the interest of a healthier learning ecosystem.
Consider the question “What are the challenges associated with the adoption of online education mode? Suggest the ways to deal with these challenges.”
Conclusion
The lack of a regulatory framework in India along the lines of the General Data Protection Regulation (GDPR) in Europe could impinge on the privacy of students. What we need is ethics policy in online education space.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Protecting freedom in era of technological transformation
From UPSC perspective, the following things are important :
Prelims level: Not much
Mains level: Paper 2- How governments are dealing with the dominance of social media
The article discusses the issue of growing influence of social media companies and response of the governments.
Issues with the growing influence of social media companies
- In the US the last two general elections in 2016 and 2020 have seen strong charges of political manipulation by social media companies.
- But influence of social media companies is not limited ot elections, it envelops a range of domestic and international issues.
- These issuesincludes: the concentration of economic power, individual rights against the state as well as the corporation, disinformation, the rise of digital geopolitics, and global digital governance.
How governments are responding
- Democratic forces need to consult each other and collaborate in developing new norms for managing the digital world.
- In the US, both the left and right are demanding that digital behemoths like Amazon, Google, Facebook and Twitter are brought under greater control if not broken up.
- Last December, the European Commission proposed new rules to promote competition and fairness in digital markets.
- The EU is likely to approve a Digital Markets Act next year.
- Australia has decreed that Google must work out an arrangement with Australian newspapers to pay for the use of their content.
- The current digital giants, however, are not easily amenable to political attack.
- They are bigger than the biggest we have known.
3 Issues with business practices of social media companies
- Governments are now questioning the sharp business practices of the tech giants especially labour rights, taxes and politics.
- While the tech giants have created a lot of new wealth, some of them have sharply squeezed the labour.
- In California, trade unions are battling against the success of Uber and Lyft to turn employees into “contract workers” to deny them multiple benefits.
- Digital giants have been aggressive tax evaders.
- On the political front recently,Twitter and Facebook shut down President Donald Trump’s accounts.
- European leaders raised important questions about social media’s actions against Trump.
Way forward
- Answer to deal with social media on political front lies in laying down a clear set of obligations and responsibilities for the digital giants.
- This move will help in building digital sovereignty.
- The world’s democracies must get together to discuss global digital governance.
Consider the question “What are the challenges posed by the growing influence of social media companies in the democratic countries?”
Conclusion
As governments push back against big tech, a new challenge presents itself — reining in the growing power of the state in the digital age. The answer lies in democracies modernising their laws to protect freedoms in the era of technological transformation.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
What is Non-price Competition?
From UPSC perspective, the following things are important :
Prelims level: Non-price competition
Mains level: Data privacy issues
Data privacy can take the form of non-price competition and abuse of dominance can lower privacy protection, a study by the Competition Commission of India (CCI) has said.
Try this PYQ:
Q.Right to Privacy is protected as an intrinsic part of Right to Life and Personal Liberty. Which of the following in the Constitution of India correctly and appropriately imply the above statements?
(a) Article 14 and the provisions under the 42nd Amendment to the Constitution
(b) Article 17 and the Directive Principles of State Policy in Part IV
(c) Article 21 and the freedoms guaranteed in Part III
(d) Article 24 and the provisions under the 44th Amendment to the Constitution
What is Non-price Competition?
- Non-price competition is a marketing strategy “in which one firm tries to distinguish its product or service from competing products on the basis of attributes like design and workmanship”.
- It often occurs in imperfectly competitive markets as it exists between two or more producers that sell goods and services at the same prices but compete through non-price measures.
- Such measures include marketing schemes and greater quality or any sustainable competitive advantage other than price.
What is CCI’s observation?
- The CCI study made observations about non-price factors such as quality of service (QoS), data speeds etc. which are likely to be the new drivers of competitive rivalry between service providers in the telecom sector.
- CCI noted that an aspect of data in the context of competition in digital communications market is the conflict between allowing access and protecting consumer privacy.
Privacy at stake
- Abuse of dominance can take the form of lowering the privacy protection and therefore fall within the ambit of antitrust as low privacy standard implies lack of consumer welfare.
- Privacy can take the form of non-price competition, said the CCI.
- On other non-price factors of competition, CCI found that consumers ranked network coverage at the top followed by customer service despite their Privacy.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
New WhatsApp Privacy Policy
From UPSC perspective, the following things are important :
Prelims level: The principle of purpose limitation
Mains level: Paper 2- WhatsApp privacy policy update and issue of privacy
Privacy policy update by the WhatsApp recently led to widespread protest from the user forcing company to put the update on hold. If India had made Personal Protection Bill into the law, the privacy policy update would have been illegal. The article deals with this issue.
About WhatsApp
- WhatsApp’s unique blend of text, audio, and voice messaging and calling platform.
- In November 2014, WhatsApp adopted the Signal protocol for end-to-end encryption after its acquisition by Facebook.
- WhatsApp has two billion users worldwide, of which 400 million are in India, the largest in any country.
What the privacy policy update is about
- The updated policy seeks consent from users to allow the platform to share their data with Facebook and its companies,
- It means that WhatsApp would share transaction data, mobile device information, IP addresses, and other metadata on how users interact with businesses on WhatsApp.
- Such sharing would be done with the user being notified before the start of a chat if the business uses Facebook to store and analyze data and the user would have the option of blocking the business.
- The update would defy the principle of purpose limitation that has been the yardstick of addressing privacy concerns at a global level.
What is the principle of purpose limitation
- The Indian government has also sent a strong note to WhatsApp, seeking the company’s response to 14 queries.
- This note has sent a clear message to WhatsApp to not subject Indian users to greater information security risks and vulnerabilities with the consolidation of data from WhatsApp and Facebook.
- In the note, the government referred to the principle of purpose limitation provisions in the Personal Data Protection Bill (PDPB) currently being discussed by a joint select committee.
- Had the bill been passed by now, WhatsApp’s move would have been illegal.
- Provisions in the bill required that every data intermediary has to take explicit permission from the user whose data would be harvested.
- Even the method of data classification into sensitive personal data and critical data has been defined and their processing possibilities mentioned in the bill.
Way forward
- The government should make the Personal Data Protection Bill into law so that such restrictive practices can never be introduced in the first place.
- It is due to such law, WhatsApp did make an exception for its users in the European Union.
- The Competition Commission of India should take note that this is a classic case of an organization using its near-monopolistic power to push through something that is not in the consumer interest.
Consider the question “What is the principle of purpose limitation in the Personal Data Protection Bill? How it can help user protect its privacy?”
Conclusion
As Digital India expands and brings in more users from the current base of 70 crores, and more take to social media for communications and business, they must be ensured a safer digital space, given that most wouldn’t be aware of the reach of the data being generated.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
WhatsApp’s contentious Privacy Policy
From UPSC perspective, the following things are important :
Prelims level: Article 21
Mains level: Right to Privacy
The Government of India has asked WhatsApp to withdraw the proposed changes in its privacy policy.
Q.What are the factors responsible for the spread of misinformation on social media? Suggest the measures to tackle it.
Core of the news
- WhatsApp has been embroiled in a controversy over its updated privacy policy.
- The posts are pointers on the new policy.
What was the news Privacy Policy?
- When one goes to the status tab on the app, one can see the WhatsApp icon and its four posts, along with the statuses of one’s contacts.
- While one reads ‘We are committed to your privacy’, another reads, ‘WhatsApp can’t read or listen to your personal conversations as they’re end-to-end encrypted’.
- Another post reads ‘WhatsApp can’t see your shared location’ and yet another reads ‘WhatsApp doesn’t share your contacts with Facebook’.
- The messaging app reviewed its privacy policy and asked users to accept the terms and conditions by February 8. Following this, the app faced severe backlash from its users and privacy advocates.
Issues pointed by Govt.
- said that the proposed changes raised “grave concerns” over the implications of the choice and the autonomy of Indian citizens.
- It pointed out that the Indian users, who have not been given the option to opt-out of data-sharing with Facebook companies, were being subjected to differential treatment.
- The issue is the impact it has on informational privacy, data security and user choice.
Data at stake
- The government asked WhatsApp to reconsider its approach to respect the informational privacy, freedom of choice and data security of Indian citizens.
- It said that India’s distinct identity and its people must be properly respected and any unilateral changes to WhatsApp Terms of Service and Privacy would not be fair and acceptable.
A discriminatory move
- India formed the largest segment of WhatsApp’s user base globally and any change in policies would have a disproportionate impact on its citizens.
- The privacy policy offered by WhatsApp to its European users specifically prohibits the use of any information shared with a Facebook company for those companies’ own purposes.
- This Clause is not present in the privacy policy offered to Indian users.
- This differential and discriminatory treatment of Indian and European users is attracting serious criticism and betrays a lack of respect for the rights and interest of Indian citizens.
What lies ahead?
- India has a huge user base of WhatsApp and Facebook in India.
- The consolidation of sensitive information exposes a very large segment of Indian citizens to greater information security risks.
- By not providing Indian users with the ability to opt-out of this data sharing with other Facebook companies, WhatsApp is treating users with an ‘all-or-nothing’ approach.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Personal Data Protection Bill 2019
From UPSC perspective, the following things are important :
Prelims level: Data Protection Authority
Mains level: Paper 2- Personal Data Protection Bill 2019 and issues with it
The Personal Data Protection Bill (2019) has several provisions which could have implications for the privacy of an individual. The article examines such provisions and highlights the need for further debate on the Bill.
Evolution of privacy as a fundamental right
- The Supreme Court in MP Sharma v. Satish Chandra (1954) and Kharak Singh v. Uttar Pradesh (1962) had declared that while in certain circumstances the privacy of individuals was to be protected, there was no constitutional right to privacy in and of itself.
- However, in Puttuswamy v India (2017) the Supreme Court accepted privacy as a fundamental right.
- This was an important development.
Rising importance of data
- The rising importance of data has pushed over 80 countries to pass national laws protecting the collection and use of their citizens’ data by companies and the government.
- The DPB will have huge commercial and political consequences for India.
- In India, the Personal Data Protection Bill 2019 (DPB) is currently under consideration by a parliamentary committee.
- According to Ernst and Young, emerging technologies in India will create $1 trillion in economic value by 2025.
- Much of this value will be founded on the creation, use, and sale of data, and the DPB will have immense implications as firms scramble to meet new privacy regulations.
Conditions for access to data and issues
- The bill establishes a number of conditions for companies to follow.
- For one, it would require digital firms to obtain permission from users before collecting their data.
- It also declares that users who provide data are, in effect, the owners of their own data.
- So that the users will be able to control the data their online selves produce, and may request firms to delete it, just as European internet-users’ “right to be forgotten”.
- But the bill stipulates that critical or sensitive personal data, related to information such as religion, or to matters of national security, must be accessible to the government if needed to protect national interest.
- Critics have suggested that such open-ended access could lead to misuse.
- Even B N Srikrishna, who chaired the committee that drafted the original bill has also expressed concerns about this provision.
- Other major concern is about Data Protection Authority (DPA).
Concerns about Data Protection Authority
- The bill outlines the establishment of a Data Protection Authority (DPA).
- The DPA will be charged with managing data collected by the Aadhaar programme.
- It will be led by a chairperson and six committee members, appointed by the central government on the recommendation of a selection committee.
- But this selection committee will be composed of senior civil servants, raising questions about the board’s independence.
- The government’s power to appoint and remove members at its discretion also stokes fears about its ability to influence this independent agency.
- Unlike similar institutions, such as the Reserve Bank of India or the Securities and Exchange Board, the DPA will not have an independent expert or member of the judiciary on its governing committee.
Consider the question “Discuss the various provision of Personal Data Protection Bill 2019 for the protection of individual’s privacy. What are the concerns over the various provisions of the Bill?”
Conclusion
The DPB is a unique opportunity for India, a country with some 740 million internet users, to forge a pathbreaking agenda that will act as a standard-setter in the still-developing field of national data protection legislation.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Narco Test and the Issue of Consent
From UPSC perspective, the following things are important :
Prelims level: Narcoanalysis, Polygraph Test
Mains level: Not Much
Involuntary administration of narco or lie detector tests is an “intrusion” into a person’s “mental privacy,” a Supreme Court judgment of 2010 has held.
Try this question:
Q.What are the ethical issues associated with the Lie-detection tests?
Various Lie detector tests
(1) Polygraph Test
- A polygraph test is based on the assumption that physiological responses that are triggered when a person is lying are different from what they would be otherwise.
- Instruments like cardio-cuffs or sensitive electrodes are attached to the person, and variables such as blood pressure, pulse, respiration, change in sweat gland activity, blood flow, etc., are measured as questions are put to them.
- A numerical value is assigned to each response to conclude whether the person is telling the truth, is deceiving, or is uncertain.
(2) Narcoanalysis
- Narcoanalysis, by contrast, involves the injection of a drug, sodium pentothal, which induces a hypnotic or sedated state.
- In such a state, the subject’s imagination is neutralized, and they are expected to divulge information that is true.
- The drug, referred to as “truth serum” in this context, was used in larger doses as anaesthesia during surgery and is said to have been used during World War II for intelligence operations.
Why these tests are so (in)famous?
- Investigating agencies seek to employ these tests in the investigation, and are sometimes seen as being a “softer alternative” to torture or “third degree” to extract the truth from suspects.
- These tests put into consideration the international norms on human rights, the right to a fair trial, and the right against self-incrimination under Article 20(3) of the Constitution.
Legal status in India
- In ‘Selvi & Ors vs State of Karnataka & Anr’ (2010), a Supreme Court Bench comprising CJI ruled that no lie detector tests should be administered “except on the basis of the consent of the accused”.
- Those who volunteer must have access to a lawyer, and have the physical, emotional, and legal implications of the test explained to them by police and the lawyer, the Bench said.
- It said that the ‘Guidelines for the Administration of Polygraph Test on an Accused’ published by the National Human Rights Commission in 2000, must be strictly followed.
- The subject’s consent should be recorded before a judicial magistrate, the court said.
What was the latest Judgement?
- Involuntary administration of narco or lie detector tests is an “intrusion” into a person’s “mental privacy,” a Supreme Court judgment of 2010 has held.
- The consequences of such tests on “individuals from weaker sections of society who are unaware of their fundamental rights and unable to afford legal advice” can be devastating.
- It may involve future abuse, harassment and surveillance, even leakage of the video material to the Press for a “trial by media.”
- Such tests are an affront to human dignity and liberty and have long-lasting effects.
- “An individual’s decision to make a statement is the product of a private choice and there should be no scope for any other individual to interfere with such autonomy,” the apex court had held.
Legal status of its outcome
- The results of the tests cannot be considered to be “confessions”, because those in a drugged-induced state cannot exercise a choice in answering questions that are put to them.
- However, any information or material subsequently discovered with the help of such a voluntarily-taken test can be admitted as evidence, the court said.
- Thus, if an accused reveals the location of a murder weapon in the course of the test, and police later find the weapon at that location, the statement of the accused will not be evidence, but the weapon will be.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
What is Non-Personal Data?
From UPSC perspective, the following things are important :
Prelims level: Non-personal data
Mains level: Data privacy issues
A government committee headed by Infosys co-founder has suggested that non-personal data generated in the country be allowed to be harnessed by various domestic companies and entities.
Practice question for mains:
Q.What is Non-Personal Data? Discuss its utility and various privacy concerns associated with it.
What is non-personal data?
- In its most basic form, non-personal data is any set of data which does not contain personally identifiable information.
- This, in essence, means that no individual or living person can be identified by looking at such data.
- For example, while order details collected by a food delivery service will become non-personal data if the identifiers such as name and contact information are taken out.
- The government committee, which submitted its report, has classified non-personal data into three main categories, namely public non-personal data, community non-personal data and private non-personal data.
Types of non-personal data
Depending on the source of the data and whether it is anonymised in a way that no individual can be re-identified from the data set, the three categories have been divided:
1) Public
All the data collected by government and its agencies such as census, data collected by municipal corporations on the total tax receipts in a particular period or any information collected during execution of all publicly funded works have been kept under the umbrella of public non-personal data.
2) Community
Any data identifiers about a set of people who have the same geographic location, religion, job, or other common social interests will form the community non-personal data. For example, the metadata collected by ride-hailing apps, telecom companies, electricity distribution companies among others have been put under the community non-personal data category by the committee.
3) Private
Private non-personal data can be defined as those which are produced by individuals which can be derived from the application of proprietary software or knowledge.
How sensitive can non-personal data be?
- Unlike personal data, which contains explicit information about a person’s name, age, gender, sexual orientation, biometrics and other genetic details, non-personal data is more likely to be in an anonymised form.
- However, in certain categories such as data related to national security or strategic interests such as locations of government laboratories or research facilities, even if provided in anonymised form can be dangerous.
- Similarly, even if the data is about the health of a community or a group of communities, though it may be in anonymised form, it can still be dangerous, the committee opined.
- Possibilities of such harm are obviously much higher if the original personal data is of a sensitive nature.
- Therefore, the non-personal data arising from such sensitive personal data may be considered as sensitive non-personal data.
What are the global standards on non-personal data?
- In May 2019, the EU came out with a regulatory framework for the free flow of non-personal data.
- It suggested that member states of the union would cooperate with each other when it came to data sharing.
- Such data, the EU had then ruled would be shared by member states without any hindrances.
- The authorities must inform the commission of any draft act which introduces a new data localisation requirement or makes changes to an existing data localisation requirement.
- The regulation, however, had not defined what non-personal data constituted of and had simply said all data which is not personal would be under its category.
What areas does India’s non-personal data draft miss?
- Though the non-personal data draft is a pioneer in identifying the power, role, and usage of anonymised data, there are certain aspects such as community non-personal data, where the draft could have been clearer.
- Non-personal data often constitute protected trade secrets and often raises significant privacy concerns.
- The paper proposes the nebulous concept of community data while failing to adequately provide for community rights.
- Other experts also believe that the final draft of the non-personal data governance framework must clearly define the roles for all participants, such as the data principal, the data custodian, and data trustees.
Conclusion
- Regulation must be clear, and concise to provide certainty to its market participants, and must demarcate the roles and responsibilities of participants in the regulatory framework.
- The report is unclear on these counts and requires public consultation and more deliberation.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Aarogya Setu app is now open source
From UPSC perspective, the following things are important :
Prelims level: AarogyaSetu App
Mains level: Privacy concerns with AarogyaSetu App
Amid concerns over privacy of data being collected by its COVID-19 contact tracing app, the union government has open-sourced the Aarogya Setu app.
Right to Privacy is an important topic for GS. The Aarogya Setu app which has a lot more to offer is under the radar due to the underlying vacuum of Privacy Law in India. To tackle this, the government has launched a bug bounty programme (a sort of hackathon).
About AarogyaSetu App
- The App enables people to assess themselves the risk of their catching the Corona Virus infection.
- It is designed to keep track of other AarogyaSetu users that a person came in contact with and alert him or her if any of the contacts tests positive for COVID-19.
- It achieves this using the phone’s Bluetooth and GPS capabilities.
- Once installed in a smartphone through an easy and user-friendly process, the app detects other devices with AarogyaSetu installed that come in the proximity of that phone.
- The app can then calculate the risk of infection based on sophisticated parameters if any of these contacts have tested positive.
- The personal data collected by the App is encrypted using state-of-the-art technology and stays secure on the phone until it is needed for facilitating medical intervention.
Issues with the app
- The AarogyaSetu app faces the same issue as every other contact tracing technology that has come up during the pandemic period — it is people dependent.
- It needs widespread usage and self-reporting to be effective.
- Given that any number of total users will be a subset of smartphone owners in India, and there are bound to be variations in the levels of self-reporting, the efficacy is not bulletproof.
- The terms of use of the app also say as much, distancing the government from any failure on the part of the app incorrectly identifying COVID-19 patients.
1) Privacy concerns
- First of all, the app exists in the privacy law vacuum that is India.
- With no legislation that spells out in detail how the online privacy of Indians is to be protected, AarogyaSetu users have little choice but to accept the privacy policy provided by the government.
- The policy goes into some detail on where and how long the data will be retained, but it leaves the language around who will have access to it vague.
- As per the policy persons carrying out medical and administrative interventions necessary in relation to COVID-19” will have access to the data.
- This suggests interdepartmental exchanges of people’s personal information and is more excessive than countries like Singapore and even Israel.
2) Technical issue
- Beyond the legal loopholes, there are technical loopholes as well.
- The unique digital identity in AarogyaSetu is a static number, which increases the probability of identity breaches.
- The abundance of data collected is also potentially problematic.
- AarogyaSetu uses both Bluetooth as well as GPS reference points, which could be seen as overkill whereas other apps such as TraceTogether make do with Bluetooth.
3) Other issues
- Experts emphasise that automated contact tracing is not a panacea.
- They caution against an over-reliance on technology where a competent human-in-the-loop system with sufficient capacity exists.
Back2Basics: What is Open Source?
- The term open source refers to something people can modify and share because its design is publicly accessible.
- The term originated in the context of software development to designate a specific approach to creating computer programs.
- Today, however, “open source” designates a broader set of values—what we call “the open source way.”
- Open source projects, products, or initiatives embrace and celebrate principles of open exchange, collaborative participation, rapid prototyping, transparency, meritocracy, and community-oriented development.
The source code
- “Source code” is the part of the software that most computer users don’t ever see; it’s the code computer programmers can manipulate to change how a piece of software—a “program” or “application”—works.
- Programmers who have access to a computer program’s source code can improve that program by adding features to it or fixing parts that don’t always work correctly.
What is Open Source Software?
- At the simplest level, open-source programming is merely writing code that other people can freely use and modify.
- Open source is a term that originally referred to open source software (OSS).
- OSS is a code that is designed to be publicly accessible—anyone can see, modify, and distribute the code as they see fit.
- An open-source development model is a process used by an open-source community project to develop open-source software.
- The software is then released under an open-source license, so anyone can view or modify the source code.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
What are the concerns around the AarogyaSetu app?
From UPSC perspective, the following things are important :
Prelims level: Aarogya Setu App
Mains level: Privacy issues with the app
- Recently the AarogyaSetu app — for pan-India use was launched as the main contact tracing technology endorsed by the Central government.
- Soon it became one of the most downloaded apps globally and has crossed the 75 million mark.
- However, there are concerns for more transparency on the inner workings of an app that seeks the personal details of millions.
RIght to Privacy is a very much contested topic for GS. The Aarogya Setu app which has a lot more to offer, is under the radar due to underlying vacuum of Privacy Law in India.
AarogyaSetu App
- The App enables people to assess themselves the risk of their catching the Corona Virus infection.
- It is designed to keep track of other AarogyaSetu users that a person came in contact with and alert him or her if any of the contacts tests positive for COVID-19.
- It achieves this using the phone’s Bluetooth and GPS capabilities.
- Once installed in a smartphone through an easy and user-friendly process, the app detects other devices with AarogyaSetu installed that come in the proximity of that phone.
- The app can then calculate the risk of infection based on sophisticated parameters if any of these contacts has tested positive.
- The personal data collected by the App is encrypted using state-of-the-art technology and stays secure on the phone till it is needed for facilitating medical intervention.
Issues with the app
- The AarogyaSetu app faces the same issue as every other contact tracing technology that has come up during the pandemic period — it is people dependent.
- It needs widespread usage and self-reporting to be effective.
- Given that any number of total users will be a subset of smartphone owners in India, and there are bound to be variations in the levels of self-reporting, the efficacy is not bulletproof.
- The terms of use of the app also say as much, distancing the government from any failure on the part of the app in correctly identifying COVID-19 patients.
Are there privacy concerns?
- First of all, the app exists in the privacy law vacuum that is India.
- With no legislation that spells out in detail how the online privacy of Indians is to be protected, AarogyaSetu users have little choice but to accept the privacy policy provided by the government.
- The policy goes into some detail on where and how long the data will be retained, but it leaves the language around who will have access to it vague.
- As per the policy persons carrying out medical and administrative interventions necessary in relation to COVID-19” will have access to the data.
- This suggests interdepartmental exchanges of people’s personal information and is more excessive than countries like Singapore and even Israel.
Technical issue
- Beyond the legal loopholes, there are technical loopholes as well.
- The unique digital identity in AarogyaSetu is a static number, which increases the probability of identity breaches.
- The abundance of data collected is also potentially problematic.
- AarogyaSetu uses both Bluetooth as well as GPS reference points, which could be seen as overkill whereas other apps such as TraceTogether make do with Bluetooth.
Other issues
- Experts emphasise that automated contact tracing is not a panacea.
- They caution against an over-reliance on technology where a competent human-in-the-loop system with sufficient capacity exists.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
Breach of trust
From UPSC perspective, the following things are important :
Prelims level: Not much.
Mains level: Paper 2- Breach of privacy in sharing of call record data of citizens.
Context
In bypassing established protocol to seek call details of citizens en masse, the government violates SC guidelines.
What is the issue?
- Departure from stringent protocol: The Cellular Operators Association of India has reported mass requests from the government for mobile call detail records (CDRs).
- Which is a serious departure from the stringent protocol established by the UPA government following an uproar in 2013 after prominent politicians were found to be under unauthorised surveillance.
- Records of all customers: Records have been sought for all consumers on certain dates in parts of Delhi, Andhra Pradesh, Haryana, Himachal Pradesh, Jammu & Kashmir, Kerala, Odisha, Madhya Pradesh and Punjab.
- In the case of Delhi, records were sought for the last three days of campaigning before assembly elections, while the anti-CAA protests were at their peak.
- How the data was requested? Requests were delivered by local offices of the Department of Telecommunications, taking advantage of a condition in licences granted to operators, which permits the DoT to inspect their CDRs, which go back one year.
Breach of many requirements and norms
- A serious breach of privacy: These requests depart from established protocol and international expectations on multiple counts, and amount to a serious breach of privacy.
- What is the protocol for requesting CDR information? A CDR request is supposed to be sanctioned by the home secretary and handled by a police officer of the rank of SP or above,
- But in this case DoT offices were used.
- The requirement of informing magistrate was not fulfilled: The requirement to report CDR requests on a monthly basis to the district magistrate was not complied with.
- No reason was offered: Most importantly, no reason was offered for snooping on the traffic of citizens.
- Surveillance must be specific and purposive: It is generally understood that communications surveillance must be specific and purposive, and must not trespass on the privacy of the innocent.
- Invasion of privacy of all citizens: Indiscriminate mass surveillance of communications invades the privacy of all citizens to the detriment of public trust. In this case, it was for purposes which are not verifiably honourable, since the government has chosen not to reveal them.
Why the CDR data matters if it is metadata only?
- Combining CDR with other data gives more information: CDRs are all metadata and no content. They do not reveal any words uttered or messaged.
- But combining the metadata with phone location data reveals a lot about connections between specific people and the actions that they take.
- Multi-dimensional map of human activity: If data is available at scale, as was the case here, it is possible to build a multi-dimensional map of human activity, and correlate it with real events.
- This would disturb the balance of information power between the citizen and the state, and amount to a breach of privacy.
Conclusion
If the government needs CDR data for a legitimate purpose, it should have no objection to following the rule-book scrupulously. And if there is a reason for sidestepping protocol in a sensitive matter, it should explain why.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
The issues around data localisation
From UPSC perspective, the following things are important :
Prelims level: Not much.
Mains level: Paper 2- Data localisation and issues involved.
Context
The contentious clauses on local data storage in the revised Personal Data Protection Bill need re-examination.
What Personal Data Protection Bill contains?
- Greater control to an individual: The draft law is a comprehensive piece of legislation that seeks to give individuals greater control over how their personal data is collected, stored and used.
- The promise of improvement over the current privacy law: Once passed, the law promises a huge improvement on current Indian privacy law, which is both inadequate and improperly enforced.
- Criticism of the bill: The proposed bill has attracted criticism on various grounds such as-
- The exceptions created for the state.
- The limited checks imposed on state surveillance, and-
- Regarding various deficiencies in the structures and processes of the proposed Data Protection Authority.
The issue over the “data localisation”
- Data within the country: The phrase, which can refer to any restrictions on cross-border transfer of data, has largely come to refer to the need to physically locate data within the country.
- Provisions for the transfer of personal data outside India: The PDP Bill enables the transfer of personal data outside India, with the sub-category of sensitive personal data have to be mirrored in the country (e. a copy will have to be kept in the country).
- Ban on transfer of critical data outside the country: Data processing/collecting entities will, however, be barred from transferring critical personal data (a category that the government can notify at a subsequent stage) outside the country.
- Different from Justice Srikrishna committee report: These above provisions have been changed from the earlier version of the draft Bill, released by the Justice Srikrishna Committee in 2018.
- The 2018 draft imposed more stringent measures that required both personal and sensitive personal data to be mirrored in the country (subject to different conditions).
- Welcome move: The move to liberalise the provisions in the 2019 version of the Bill is undoubtedly welcome, particularly for businesses and users.
How removing the restriction matters?
- Reduction in cost to business: Liberalised requirements will limit costs to business and ensure users have greater flexibility in choosing where to store their data.
- More proportionate approach: The changes in the 2019 draft reflect a more proportionate approach to the issue as they implement a tiered system for cross-border data transfer, ostensibly based on the sensitivity/vulnerability of the data.
- Move-in accordance with the right to privacy: This seems in accord with the Supreme Court’s dicta in the 2017 Puttaswamy case.
- Conditions for interference in privacy: The Court had made it clear that interference in the fundamental right to privacy would only be permissible if inter alia deemed necessary and proportionate.
Test of proportionality in the bill
- On closer examination, it appears that even the revised law may not actually stand the test of proportionality.
- The three-argument for imposing norms: There are broadly three sets of arguments advanced in favour of imposing stringent data localisation norms:
- Sovereignty and government functions. Referring to the need to recognise Indian data as a resource to be used to further national interest (economically and strategically), and-
- To enable enforcement of Indian law and state functions.
- Accruing benefits to the local industry: The second claim is that economic benefits will accrue to local industry in terms of creating local infrastructure, employment and contributions to the AI ecosystem.
- Protection of civil liberties: Regarding the protection of civil liberties, the argument is that local hosting of data will enhance its privacy and security by ensuring Indian law applies to the data and users can access local remedies.
- Contradiction in the claim of protection? If data protection was required for the above purposes, it would make sense to ensure that local copies were retained of all the categories of personal data provided for in the Bill (as was the case with the previous draft of the law).
- Sectoral obligations: In the alternative, sectoral obligations would also suffice as is currently the case with sectors such as digital payments data, certain types of telecom data, government data, etc.
- Will data localisation lead to privacy protection? We note that the security of data is determined more by the technical measures, skills, cybersecurity protocols, etc. put in place rather than its mere location.
- Localisation may make it easier for domestic surveillance over citizens.
- Enabler of better exercise of privacy by citizens: It may also enable the better exercise of privacy rights by Indian citizens against any form of unauthorised access to data, including by foreign intelligence.
- Effectiveness matters: The degree of protection afforded to data will depend on the effectiveness of the applicable data protection regime.
- Protecting privacy through less intrusive measures: Insofar as privacy is concerned, this could be equally protected through less intrusive, suitable and equally effective measures such as requirements for contractual conditions and using adequacy tests for the jurisdiction of the transfer.
- Such conditions are already provided for in the PDP Bill as a set of secondary conditions.
- The European Union’s General Data Protection Regulation too uses a similar framework.
- Extra-territorial operation: The extraterritorial application of the PDP Bill also ensures that the data protection obligations under the law continue to exist even if the data is transferred outside the country.
- Giving an individual a choice: If privacy protection is the real consideration, individuals ought to be able to choose to store their data in any location which afford them the strongest privacy protections.
- It is arguable that data of Indians will continue to be more secure if stored and processed in the European Union or California.
- These two jurisdictions have strong data protection laws and advanced technical ecosystems.
Way forward
- Identification of the issues: The joint parliamentary committee ought to, ideally, identify the need, purpose and practicality of putting in place even the (relatively liberal) measures contained in the PDP Bill.
- Broader thinking at policy level: Further, in order for localisation-related norms to bear fruit, either in terms of protecting citizen rights, enabling law enforcement access to data or enabling the development of the local economy, there has to be broader thinking at the policy level.
- This may include for instance-
- Reforming surveillance-related laws.
- Entering into more detailed and up-to-date mutual legal assistance treaties.
- Enabling the development of sufficient digital infrastructure, and
- Creating appropriate data-sharing policies that preserve privacy and other third party rights, while enabling data to be used for socially useful purposes.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
Right To Privacy
System Risk Indicator (SyRI)
From UPSC perspective, the following things are important :
Prelims level: SyRI
Mains level: Debate over right to privacy
- In a first anywhere in the world, a court in the Netherlands recently stopped a digital identification scheme for reasons of exclusion.
- This has a context for similar artificial intelligence (AI) systems worldwide, especially at a time when identity, citizenship and privacy are pertinent questions in India.
SyRI
- Last week, a Dutch district court ruled against an identification mechanism called SyRI (System Risk Indicator), because of data privacy and human rights concerns.
- It held SyRI was too invasive and violative of the privacy guarantees given by European Human Rights Law as well as the EU’s General Data Protection Regulation.
- The Dutch Ministry of Social Affairs developed SyRI in 2014 to weed out those who are most likely to commit fraud and receive government benefits.
- Legislation passed by Dutch Parliament allowed government agencies to share 17 categories of data about welfare recipients such as taxes, land registries, employment records, and vehicle registrations with a private company.
- The company used an algorithm to analyse data for four cities and calculate risk scores.
What were the arguments in court?
- After taking into account community concerns, civil society groups and NGOs launched a legal attack on this case of algorithmic governance.
- Legal criticism mounted, alleging that the algorithm would begin associating poverty and immigrant statuses with fraud risk.
- The Dutch government defended the programme in court, saying it prevented abuse and acted as only a starting point for further investigation instead of a final determination.
- The government also refused to disclose all information about how the system makes its decisions, stating that it would allow gaming of the system.
- The court found that opaque algorithmic decision-making puts citizens at a disadvantage to challenge the resulting risk scores.
- The Netherlands continuously ranks high on democracy indices.
How relevant is this for India?
- Similar to the Supreme Court’s Aadhaar judgment setting limits on the ID’s usage, the Hague Court attempted to balance social interest with personal privacy.
- However, the Aadhaar judgment was not regarding algorithmic decision-making; it was about data collection.
- The ruling is also an example of how a data protection regulation can be used against government surveillance.
- India’s pending data protection regulation, being analysed by a Joint Select Committee in Parliament, would give broad exemptions to government data processing in its current form.
- India’s proposed regulation is similar to the US in the loopholes that could be potentially exploited.
Get an IAS/IPS ranker as your 1: 1 personal mentor for UPSC 2024
























